Today we’re making our Openshift on AWS (ROSA) accelerator available for everybody to use *free of charge. This solution is the product of years of experience on the ground delivering application modernization on containers to some of the biggest companies in the world. With the release of ROSA (Red Hat OpenShift on AWS) at the […]
Information Architecture
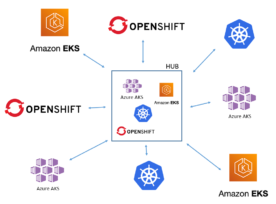
Kubernetes Multi-Cluster Management – Part 2
Introduction In Part I of our multi-cluster management series, we’ve introduced GitOps and gone over some of the reasons why you should adopt GitOps for the management of Kubernetes clusters. GitOps is always the #1 thing we set up when starting an engagement and we’ve spent a lot of time perfecting our best practices. Today […]
An Automated DevSecOps Framework
Automation for Automation – An Executable Framework for DevSecOps In an age where automated Continuous Integration and Continuous Delivery (CI/CD) is becoming more and more critical to the success of any organization, why are we still building our DevSecOps environments by hand? Instead why don’t we leverage automation for our automation? DevSecOps support teams are […]
Review of Industrial IoT Solutions – Part I
Introduction Edge computing and more generally the rise of Industry 4.0 delivers tremendous value for your business. Having the right data strategy is critical to get access to the right information at the right time and place. Processing data on-site allows you to react to events near real-time and propagating that data to every part […]
The 1001st Piece in your 1000 Piece Puzzle: .NET Default Interface Functions
I recently worked with a client who wanted a reasonably large subsystem added to Optimizely that would add automated management to their content. While cutting the code for this, I found myself writing similar code across multiple classes. I had to write it that way: 1) The client was currently on CMS11 and didn’t have […]
Create Workato Custom Connector Locally
Workato Introduction Workato is a low-code/no-code, cloud-based iPaaS Solution that is hosted on public cloud infrastructure from Google Cloud Platform and Amazon Web Services (AWS). It means everything you create here is a drag-and-drop application component that resides on cloud. Workato Connector To achieve any automation in the Workato tool, we create a recipe. The […]
Kubernetes Multi-cluster Management – Part 1
Introduction With more and more organizations adopting Kubernetes across multiple teams, the need for IT to provide a way for these teams to quickly provision and configure clusters is increasing fast. This is not only true in cloud environments but also at the edge, and from a practical standpoint, adding more clusters can become exponentially […]
Leveraging MuleSoft’s API Led Connectivity and Event-Driven Architecture with Solace
Organizations today are going into a rapid digital transformation. With MuleSoft’s API Led connectivity approach, the integration strategy of the enterprises is now going towards more reusability with quicker deliverables of projects through discovery, self-service, and reusability. But what if we mix the flavor of Event Driven Architecture also into the Enterprise’s Integration Strategy? With this blog, […]
How Good is your AEM Security? – AEMaaCS and 3rd Party Dependencies
Large scale data breaches and critical security vulnerabilities have companies thinking about security more than ever. Many developers are familiar with the OWASP top 10 (https://owasp.org/www-project-top-ten/). There are already many resources on generic mitigation for these vulnerabilities. So instead, in this series, I cover security issues and mitigations specific to AEM. In this final post, […]
Fun with custom Sitecore Processors, a look into the future (of your Sitecore content)!
This is a little P.O.C. I worked out a while ago that allowed for the creation of a custom a preview site where a user could tack on a date & time via the QueryString to see what the content would look like on that date. Only requirements were 1. it had to be friendly […]
Introduction to Event Driven Microservices
What is a Microservice? Many Large-Scale Software Projects Employ the architectural approach known as a Microservice System. Efficiency, dependability, performance, and scalability are to be increased. A single application can be developed using the microservice architectural style as a Collection of Small Services, each of which runs in its own process and Communicate with other […]
How good is your AEM Security? – Mitigation Tools
Large scale data breaches and critical security vulnerabilities have companies thinking about security more than ever. Many developers are familiar with the OWASP top 10 (https://owasp.org/www-project-top-ten/). There are already many resources on generic mitigation for these vulnerabilities. So instead, in this series, I will cover security issues and mitigations specific to AEM. Here I will […]