Implementing AWS cross-account access is crucial to managing a secure and scalable cloud environment. This setup simplifies the management process, enhances security by adhering to the principle of least privilege, streamlines operations by reducing the need to switch accounts, and facilitates compliance and auditing by centralizing access and control.
Imagine GlobalTech’s website is hosted on EC2 instances in Account A. The company’s DNS management team, responsible for updating and managing DNS records, operates within Account B using Amazon Route 53. By configuring cross-account access, the DNS team can update DNS records to reflect changes in the IP addresses of the EC2 instances or manage traffic routing without needing direct access to them. This centralization improves efficiency, enhances security, and ensures that DNS configurations are managed consistently across the company’s infrastructure.
Let’s understand this using the examples below:
Scenario: Cross-Account Access for Route 53 DNS Management
Business Context
Your company, “GlobalTech,” has a multi-account AWS environment managed through AWS Organizations. The company uses:
- Account A: Hosting EC2 instances for various applications.
- Account B: Managing DNS records using Amazon Route 53.
You want to configure cross-account access so that Route 53 in Account B can manage DNS records for EC2 instances running in Account A. This allows your DNS management team to handle DNS configurations centrally without requiring direct access to EC2 instances.
- Prerequisites
- Configuration Overview
- Best Practices
- Conclusion
Prerequisites
- AWS Organizations: GlobalTech uses AWS Organizations with an organizational unit (OU) structure.
- IAM Roles and Policies: Proper IAM roles and policies must be configured to allow cross-account access.
- Route 53 Hosted Zone: Hosted zones are set up in Account B.
Configuration Overview
Steps to Implement the Scenario
- Create IAM Role in Account A (EC2 Instances Account):
- Log in to AWS Management Console for Account A.
- Navigate to IAM and click on Roles, then Create role.
- Select Trusted Entity:
- Choose Another AWS account.
- Enter the Account ID of Account B (Route 53 account).
- Add Permissions:
- Attach the following policies to the role:
- AmazonRoute53FullAccess: Grants full access to Route 53.
- Custom policy for specific permissions, if needed.
- Attach the following policies to the role:
- Role Name:
- Name the role Route53CrossAccountRole.
- Create Role.
Update Trust Relationship in Account A Role
- Navigate to the Trust relationships tab for the Route53CrossAccountRole.
- Edit the trust policy to allow Account B to assume the role:
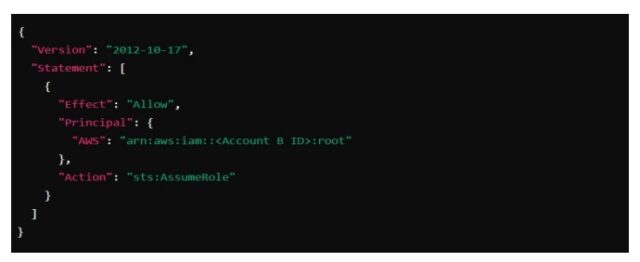
Create IAM Role in Account B (Route 53 Account)
- Log in to AWS Management Console for Account B.
- Navigate to IAM and click on Roles, then Create role.
- Select Trusted Entity:
- Choose Another AWS account.
- Enter the Account ID of Account A (EC2 account).
- Add Permissions:
- Attach policies needed for Route 53 management (if additional permissions are required).
- Role Name:
- Name the role EC2ManagementRole.
- Create Role.
Configure Route 53 Hosted Zone in Account B
- Log in to AWS Management Console for Account B.
- Navigate to Route 53 and create or select the existing hosted zone.
- Add DNS records pointing to the public IP addresses of the EC2 instances in Account A.
Assign IAM Role to EC2 Instances in Account A
- Log in to AWS Management Console for Account A.
- Navigate to EC2, and select the instances you want to associate with the role.
- Click on Actions > Security > Modify IAM Role.
- Select the Route53CrossAccountRole and save changes.
Automate DNS Updates (Optional)
- Use AWS Lambda or a similar service to automatically update DNS records in Route 53 when EC2 instances are launched or terminated in Account A.
- Ensure the Lambda function assumes the Route53CrossAccountRole to make necessary API calls to Route 53.
Testing and Verification
- Verify Role Assumption: Ensure that Account B can assume the Route53CrossAccountRole in Account A.
- Update DNS Records: Try updating DNS records in Route 53 for EC2 instances in Account A.
- Check DNS Resolution: Verify that the DNS records are correctly resolving to the EC2 instances in Account A.
Multiple Scenarios
- Use Case: Developers in Account A need temporary access to resources in Account B, such as an S3 bucket.
- Use Case: The finance team in Account A needs access to billing information for multiple AWS accounts
- Use Case: Enable network communication between VPCs in different AWS accounts
Best Practices
To ensure secure and efficient cross-account access management in AWS, follow these best practices:
1. Use AWS Organizations
- Centralized Management: Use AWS Organizations to manage multiple accounts centrally, allowing for better control and governance.
- Service Control Policies (SCPs): Apply SCPs to enforce permission boundaries and ensure accounts only have the necessary permissions.
2. Implement IAM Roles
- Cross-Account Roles: Create IAM roles for cross-account access instead of using root accounts or IAM users.
- Role Assumption: Set up trust relationships to allow users or services in one account to assume roles in another account using the sts: AssumeRole API.
3. Principle of Least Privilege
- Minimum Permissions: Grant only the permissions necessary for users, roles, and services to perform their tasks.
- Fine-Grained Policies: Use detailed IAM policies to control access at a granular level.
4. Enable Multi-Factor Authentication (MFA)
- MFA for Sensitive Operations: To add an extra layer of security, require MFA for roles and users performing sensitive operations.
- MFA Enforcement: Use IAM policies to enforce MFA for specific actions or API calls Centralize Logging and Monitoring
- AWS CloudTrail: Enable CloudTrail in all accounts to capture and log all API calls and user activities.
- Centralized Logging: Store CloudTrail logs in a centralized S3 bucket for easier analysis and monitoring.
- Amazon GuardDuty: Enable GuardDuty for continuous threat detection and monitoring.
5. Establish a Secure Network Architecture
- VPC Peering and Transit Gateway: Use VPC peering or AWS Transit Gateway to enable secure and efficient network connectivity between accounts.
6. Regular Security Audits
- Compliance Checks: Perform regular security audits and compliance checks to ensure cross-account access configurations meet security and compliance requirements.
- Security Best Practices: Regularly update your knowledge of AWS security features and follow AWS security best practices.
7. Utilize AWS Trusted Advisor
- Security Checks: Use AWS Trusted Advisor to perform security checks and receive recommendations for improving your security posture.
- Review Recommendations: Regularly review and act on the recommendations provided by AWS Trusted Advisor
To ensure secure and efficient cross-account access management in AWS, implement AWS Organizations for centralized management, use IAM roles for granting cross-account access, enforce the principle of least privilege, enable MFA for sensitive operations, centralize logging and monitoring with CloudTrail and GuardDuty, and utilize AWS Resource Access Manager (RAM) for secure resource sharing. Automate account management, establish a secure network architecture, perform regular security audits, and adopt a tagging strategy for resource organization. Following these best practices will enhance security, streamline management, and maintain compliance in your AWS environment.

