As we know, AWS Lambda is a serverless computing service that lets you run code without provisioning or managing servers. However, for Lambda functions to interact with other AWS services or resources, it needs permissions. This is where the AWS Lambda execution role comes into picture.
An execution role is an AWS Identity and Access Management (IAM) role that Lambda assumes when it runs your lambda function. This role gives the permissions to function which it needs to access AWS services and resources securely.
Why Lambda Execution Role Required?
When you create a Lambda function, it needs permissions to access other AWS resources like S3 buckets, DynamoDB tables, or CloudWatch logs. Instead of embedding credentials directly in your code (which is insecure and impractical), you assign an execution role to the Lambda function. This role defines the permissions the function has when it is invoked.
Creating an Execution Role Using AWS Management Console (GUI)
- Sign in to the AWS Management Console:
- Open the IAM console.
- Create a New Role:
- In the navigation pane, choose “Roles” and then “Create role.”
- Choose “AWS service” as the type of trusted entity.
- Choose “Lambda” from the list of services.
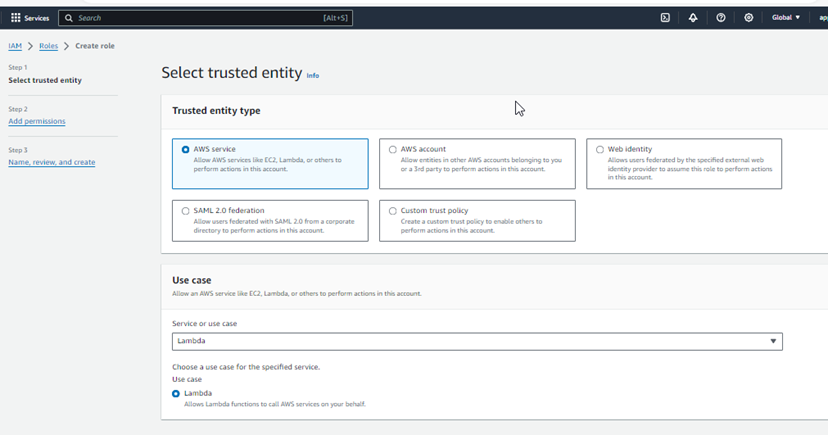
-
- Click “Next: Permissions.”
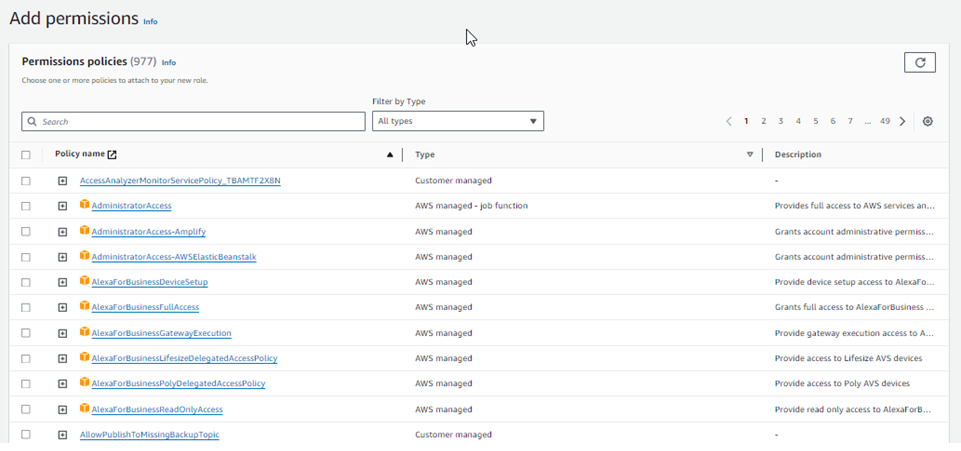
3. Attach Permissions Policies:
-
- You can either choose existing policies or can create a custom policy.
-
- Click “Next: Tags” (optional), then “Next: Review.
4.Review and Create:
-
- Enter a role name
- Review the role and click “Create role.”
- Attach the Role to Your Lambda Function:
-
- Open the Lambda console.
- Select your function.
- Under “Execution role,” choose “Use an existing role.”
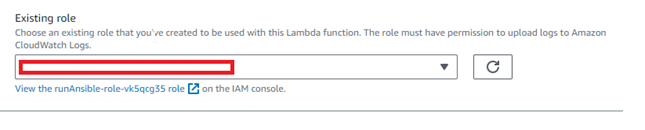
-
- Select the role you just created and click “Save.”
Creating an Execution Role Using AWS CLI
- Create the Trust Policy:
cat > policy.json <<EOF
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Effect”: “Allow”,
“Principal”: {
“Service”: “lambda.amazonaws.com”
},
“Action”: “sts:AssumeRole”
}
]
}
EOF
2.Create the Role:
aws iam create-role –role-name LambdaExecutionRole –assume-role-policy-document file://policy.json
3.Attach Permissions Policies:
aws iam attach-role-policy –role-name LambdaExecutionRole –policy-arn arn:aws:iam::aws:policy/AmazonS3ReadOnlyAccess
4. Attach the Role to Your Lambda Function:
aws lambda update-function-configuration –function-name YourLambdaFunctionName –role arn:aws:iam::YourAccountID:role/LambdaExecutionRole
Using IAM Access Analyzer to Identify Required Permissions
IAM Access Analyzer helps you identify the permissions your Lambda function needs. It analyzes your function’s activities and generates a policy that grants only the required permissions.
- Enable Access Analyzer:
- Go to the IAM Access Analyzer console.
- Create an analyzer.
Conclusion
Creating an AWS Lambda execution role is essential for granting your Lambda function the necessary permissions to interact with other AWS services securely. Whether you prefer using the AWS Management Console or the CLI, the process is straightforward. Additionally, IAM Access Analyzer will help to refine your policies to follow the principle of least privilege, enhancing the security of your applications.
By following these steps, you can ensure that your Lambda functions have the appropriate permissions while maintaining a secure and manageable environment.


Nice clarification
Perfect blog…
Excellent 👌👌
Great, Helpful Blog.👍👍
@Ankit Srivastava Well Explained..
Excellent!!!! Good Job Ankit
Excellent 👌👌
Great work and very nice explained user friendly GUI functions.
Appreciated @Ankit…!
much informative blog.
well done
Very nice and informative.
Well written Ankit.
Good to see Ankit,
Very helpful explanation, great!!!😀