This is Part 2 of a two-part series on Connectivity for Azure VMware Solution (AVS).
In this article, we’ll review Network Extensions with HCX and managing AVS networking with NSX.
Read more about AVS, its use cases, and benefits in my previous blog article – Azure VMWare Solution: What is it?
VMware HCX Network Extension
Although HCX has a few different capabilities, today we are going to focus on Network Extension. Network extension allows a Layer 2 network that exists in a vSphere distributed switch, NSX segment, or NSXv logical switch to be extended to AVS. Once the extension is in place, traffic is tunneled so that virtual machines in both the source and AVS environment are on the same Layer 2 network and utilize the network gateway at the source to traverse to other networks.
An important note: Matching segments are automatically created in NSX once networks are extended to AVS. But when unextending a network, the segment in NSX is not automatically removed.
Appliance Deployment
When a Service Mesh is configured in HCX, multiple appliances are deployed to facilitate the specific functionality that has been enabled. For each appliance deployed at the source, a partner appliance is deployed in AVS.
As part of the service mesh configuration, you’ll set the number of network extension appliances required. Each appliance for Network Extension can support up 8 extended networks. Network Extension does support high availability for the appliances, so if needed, set the number of appliances to twice the required amount needed to support the number of networks being extended.
The appliances cannot have extended networks associated with them when enabling HA, so be sure to configure HA first. The HA setup process automatically selects an unused appliance to be the second member of the active/standby HA group. Networks to be extended will then be associated with the group instead of a specific appliance.
Mobility Optimized Networking (MON)
The traffic flow for VMs in AVS on extended networks may be undesirable since all traffic is traversing the on-premises gateway. This is especially true when workloads are micro segmented and multiple parts exist in AVS, but on different networks.
Mobility Optimized Networking (MON) can be enabled in HCX to improve network traffic flow. With MON enabled, traffic can route to different networks within AVS without flowing through the on-premises gateway. In addition, MON policy routes can be created to define traffic that will flow through the cloud gateway for things outside of AVS like Azure services, and internet egress.
Figure 1 demonstrates how communication between two virtual machines on separate networks in AVS would behave with and without MON enabled. As you can see enabling MON optimizes the flow so that communication between the two virtual machines remains local to AVS.
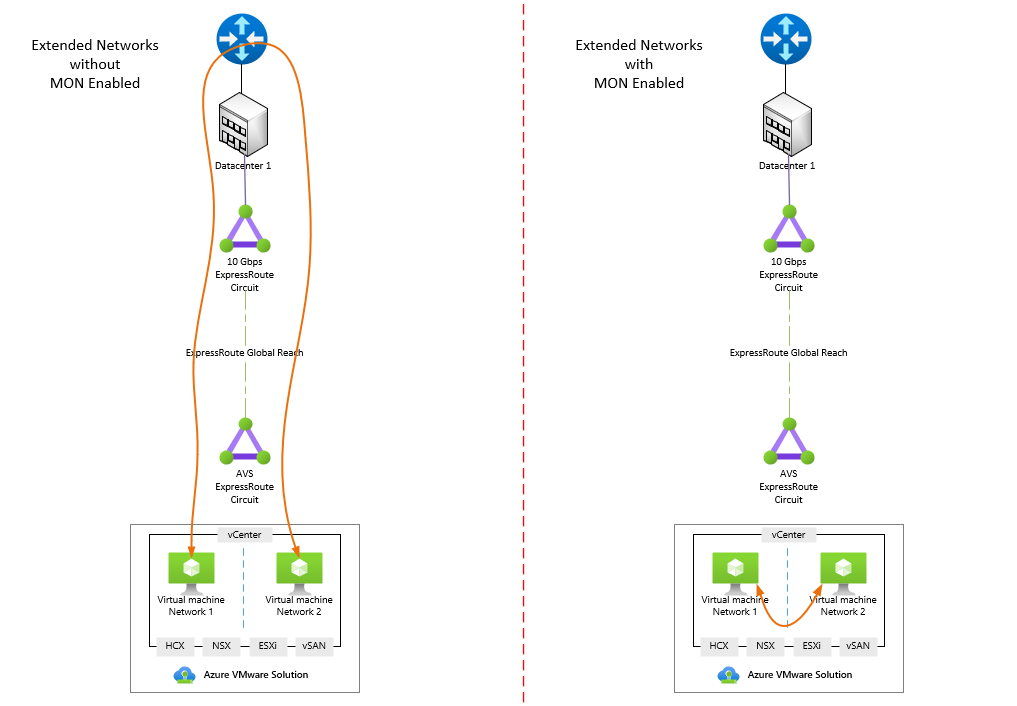
Figure 1: Traffic flow with and without Mobility Optimized Networking.
VMware NSX
NSX is included in the Azure VMware Solution deployment and is utilized to manage the networking within the VMware private cloud environment. Networks within the environment are referred to as segments. Segments define the subnet, gateway, and DHCP settings.
NSX can be configured to run a DHCP server or relay if a DHCP server already exists. If relaying to a DHCP server across a network extension, the traffic must be allowed since all DHCP requests are blocked by default. This can be completed by creating a segment profile and assigning it to the segment where the DHCP server exists.
NSX Gateways
The default deployment of NSX in AVS includes a Tier-0 gateway in active/active mode which connects to the edge to provide North/South connectivity. The Tier-0 gateway is managed by Microsoft and should not be altered.
Connected to the Tier-0 gateway is a Tier-1 gateway in active/standby mode which provides East/West connectivity and is where segments for your virtual machines will be added. Additional Tier-1 gateways can be created if desired to further segment traffic. Multiple Tier-1 gateways can be connected to a single Tier-0 gateway.
There are two management options available for the default Tier-1 gateway. Azure provides a simplified interface in the Azure portal for creating segments, configuring DHCP, setting up DNS forwarding, and configuring port mirroring. Alternatively, NSX has its own interface that can be used to manage all aspects of the platform. If additional Tier-1 gateways were added, they can only be managed via the NSX interface and are not available in the Azure portal.
Figure 2 displays a high-level layout of connectivity from the NSX gateways to external networks.
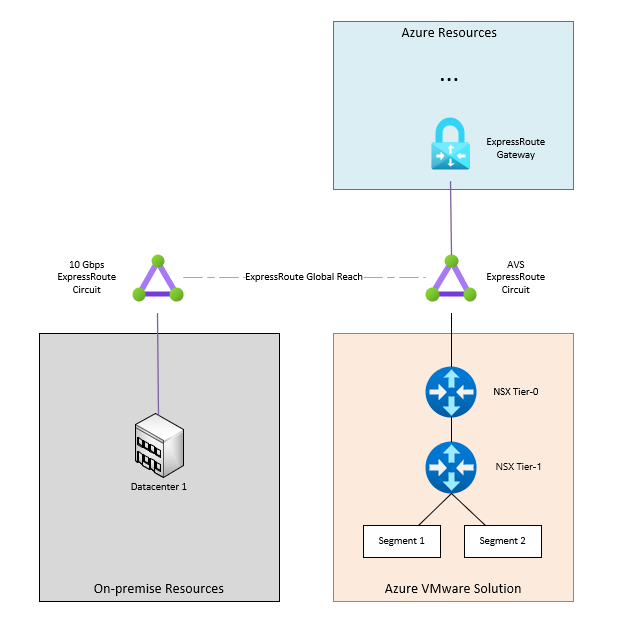
Figure 2: NSX Gateway Connectivity
Interested in taking Azure VMware Solution for a test drive?
Take part in a Proof-of-Concept (POC) to learn more about Azure VMware Solution and how it functions. Undoubtedly, you’ll quickly learn that functionality isn’t much different from what you use every day in your own datacenter, just with less management overhead. A POC is the perfect opportunity to not only validate the solution, but also get familiar with tools included in AVS that may be new to your organization such as VMware NSX for networking and HCX for inter-site connectivity and migrations.
Our dedicated Microsoft Azure practice can get you started. Our team of Azure experts will lead you through a Proof-of-Concept deployment to validate the solution in your environment. Through Perficient’s extensive Microsoft partnership, there may be funding available to cover part of the cost of the POC.
