Welcome back to part 3 of the “Four Microsoft 365 network connectivity principles you need to know” blog series! Last time we discussed the topic of local egress and how enabling local egress of Microsoft 365 data ensures the greatest chance of the traffic being routed through the closest Microsoft network point of presence in turn giving you the best performance. This time we’ll discuss the third principle, which involves direct connectivity.
Principle #3: Enabling Direct Connectivity
The third principle takes things to the next level. In addition to the local egress that we discussed in the last blog, this principle calls for direct connectivity specifically for Microsoft 365 connections. This means that the routing of Microsoft connections directly to Microsoft without any type of network intermediation. In the diagram below you’ll notice intermediation which is sending connections through a third-party intermediary such as a Security as a Service cloud (SECaaS)[1], on-premises solution, or gateway running in the Infrastructure as a Service (IaaS)[2] may have an impact on achievable performance, availability, interoperability, compared to direct connections [3]. With all that being said, direct connectivity allows for future advancements, and improvements of the Microsoft 365 cloud will automatically accrue to customers who are allowed to connect to Microsoft directly.
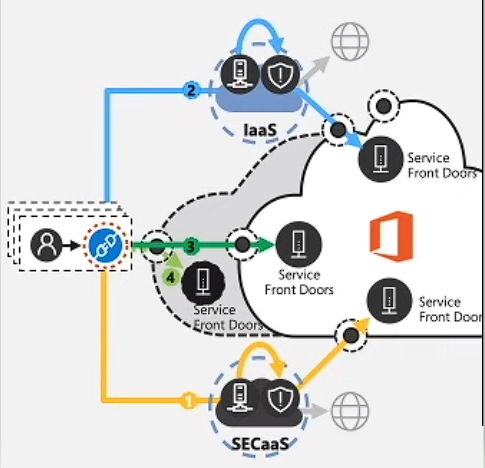
As Microsoft continues to expand its POPs (Points of Presence) and advancements of the Service Front Door infrastructure, this will allow Microsoft to get closer and closer to user geographies. In turn, direct connectivity will ensure that these types of investments automatically accrue to these organizations which will reduce latency and improve the end-user experience. This suggests that this principle of direct connectivity makes the network “future-proof” and also allows the cloud benefits to accrue the end-user experience automatically. Microsoft even went so far as to prove this point by running a series of tests for end-users connecting to the Office 365 Serve Front Door and the latency each scenario experienced. As you will see, those end-users with network topologies that have intermediation properties (i.e. IaaS [2] or SECaas[1]), experienced worse latency and performance characteristics than those connecting directly.
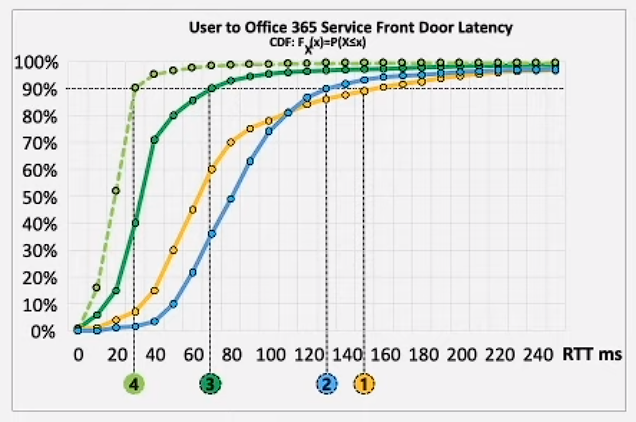
You’ll also notice the dotted line at the 90% mark, this is because Microsoft uses the 90th percentile to measure the true user experience with many of the productivity services. You’ll see the vast difference between the direct connection architecture and the intermediate/indirect connection can be upwards of 100+ms which can be very impactful to the end-user experience. This summarized the third of our four principles of network connectivity in Microsoft 365. Check back shortly where we will cover the last principle which entails modernizing security for Software as a Service (Saas). This will involve avoiding intrusive network security for Microsoft 365 connections. More on that in the next blog!

