Welcome back to our “Four Microsoft 365 network connectivity principles you need to know” blog series, it has been almost 2 months since the first article (sorry for the large gap), so if you haven’t had a chance to read the first blog, you can check it out here. Last time we talked about the first network connectivity principle which involved optimizing your network traffic. Once you’ve done your due diligence with the planning and optimization of your network traffic, you can start focusing on the second principle of enabling local Internet egress.
Principle #2 – Enable Local Egress
This second principle calls for enabling local internet egress from the location(s) where you have users directly into Microsoft’s global backbone.
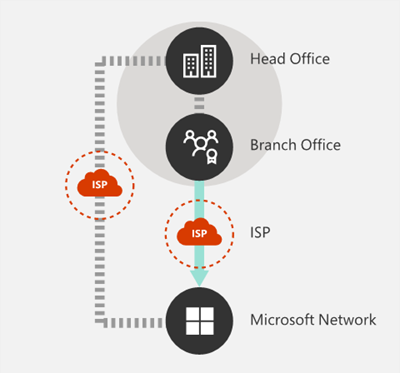
This principle of local egress ensures that the requests from the most sensitive Microsoft 365 applications are not being backhauled across your private WAN but rather using your direct Internet connections to reach the destinations quicker. By using local egress, you maximize your chances that the connection is going to be routed through the closest Microsoft network POP (point-of-presence) for best performance. In addition, this principle also suggests that DNS egress for Microsoft 365 domains should be configured to egress locally, preferably through the proximate local DNS servers performing the recursive resolver (RR) functionality. This part of the principle is critical for traffic management decisions that the cloud makes by directing the user traffic to the closest set of front doors for best performance.
Today, many traditional network architectures will have all outbound Internet connections traversing the corporate network through a central location. With the new era of networking, Microsoft recommends adopting an Internet-facing network architecture as this is better optimized for supporting latency-sensitive cloud services (i.e. Teams, Exchange, SharePoint, OneDrive, etc.) Microsoft has done a lot of work in order to supply customers with the most optimal path to the cloud. How do they do this you may ask? Well, the Microsoft Global Network was designed in a way where they provide a Distributed Service Front Door infrastructure to customers, that consists of a dynamic fabric of global entry points which in turn routes incoming cloud service connections to the closest entry point. This results in lower latency due to the reduction in length of the “last mile” by shortening the route between the customer and the cloud. The diagram below depicts what the ideal architecture looks like for SaaS (Software-as-a-Service) applications.
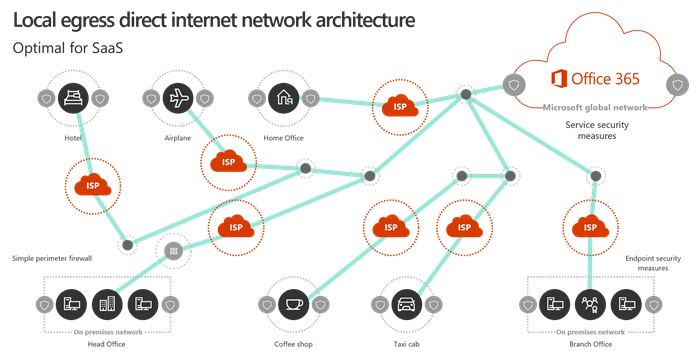
In this diagram, you’ll notice that regardless of where you reside (whether it be in your head office, home office, hotel, or coffee shop), by egressing locally you ensure the shortest possible route to the nearest Microsoft Global Network entry point. Egressing locally also reduces the load on your corporate network infrastructure and you can even rest assured knowing that the connection on both ends is secure as this will be leveraging client endpoint security and cloud security features. This summarizes the second of four network connectivity principles for Microsoft 365. Next time, we’ll tackle the third principle of enabling direct connectivity, so I hope you’ll check back soon to learn more about that topic!

