Azure Active Directory (AD) is Microsoft’s directory and Identity and Access Management (IAM) service in the cloud as opposed to ADFS, a Windows on-premise, claims-based Security Token Service (STS). In a Security Assertion Markup Language (SAML) federation however, Azure AD and ADFS are functionally equivalent acting as Identity Provider (IdP) for a Service Provider (SP) such as a cloud-based application. Previously, we have discussed SAML federation with ADFS and Oracle PBCS here. In this discussion, we outline the high-level steps to establish SAML SSO between Azure and Oracle Enterprise Planning and Budgeting Cloud Service (EPBCS).
IdP configuration: Since IdP configuration is performed by an Azure administrator and details are dependent on the version of Azure being used, we only highlight the requirements to configure Azure as Identity Provider for EPBCS below.
From Azure portal, add EPBCS application
Continue to configure SSO for EPBCS in Azure. Select SAML protocol for EPBCS
Input EPBCS details
An example of Identifier: https://login.us.oraclecloud.com:443/oam/fed/cloud/adomain. Identifier is known as Sign on URL or Provider ID in EPBCS. An example of Reply URL: https://login.us.oraclecloud.com:443/oam/server/fed/sp/sso?tenant=adomain. Reply URL is known as Assertion Consumer Service (ACS) URL in EPBCS. At this point, these values do not have to be exact; we can update them later.
Continue with EPBCS configuration, generate Azure federation metadata and save as xml file, e.g., IdPmetadata.xml. Save EPBCS configuration in Azure.
SP configuration: configure EPBCS as Service Provider
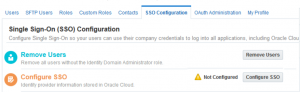
Logon to EPBCS domain with identity domain admin ID. Navigate to Users->SSO Configuration
Click Configure SSO
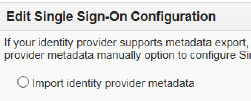
Select ‘Import identity provider metadata’ and browse to upload the IdPmetadata.xml file saved earlier.
Leave SSO protocol as HTTP Post and User Identifier at User Email Address contained in NameID. Click Save to continue.
In the screenshot below, step 2 shows IdP information stored in EPBCS. Note EPBCS Provider ID and ACS URL shown in step 3. As mentioned earlier, in Azure update the SP URLs for EPBCS and save.
Also from the portal, an Azure administrator can assign users and groups to EPBCS. The same users or groups must exist in EPBCS, either by manual entry or by uploading from a CSV file exported from Azure. Details of a batch upload process can be found here.
Test and enable SSO from EPBCS
Click Test to initiate federation SSO
Click StartSSO and enter user ID as defined in Azure and in EPBCS, for instance, user’s company email. SSO success message is returned.
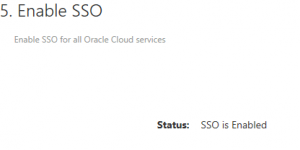
Once testing is successful, enable SSO in EPBCS
Enable identity domain (cloud) credentials:
EPBCS domain now presents both cloud and Azure sign on options:
Additional Oracle Resources
Oracle EPBCS / PBCS Documentation
- About SSO
- User Login with SSO
- SAML Identity Provider Requirements
- User Synchronization Requirements for SSO Configuration
- Automated and Manual Configuration
- Testing Your SSO Configuration
- Troubleshooting Your SSO Configuration