Back in April 2017, Microsoft announced the release of support for Modern Authentication for the Skype for Business Online PowerShell Module. Adding Modern Authentication introduces new scenarios where multi-factor authentication (MFA) can be used for authenticating remote PowerShell sessions out to Skype for Business Online. Using MFA for authentication for PowerShell sessions provides another layer of security for administrator accounts when managing Office 365 workloads. This blog post is going to go through enabling and configuring a Skype for Business Online tenant with MFA. I am not getting into the pros/cons of enabling Modern Authentication or other considerations for enabling MFA for a user. This is a simple demo using a strictly Skype for Business Online deployment.
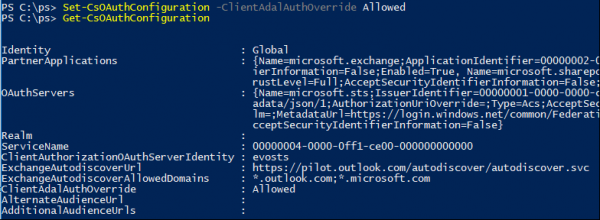
Some minor prerequisites are needed, such as the latest version of the Skype for Business Online PowerShell Module, or at least version 7.0.1045.0 or higher (Download Link). You will also want to connect to your Skype for Business Online tenant and use the Set-CsOAuthConfiguration to enable ADAL Authentication. Also use the Get-CsOAuthConfiguration command to verify the setting is changed.
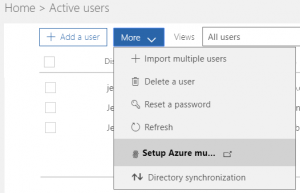
Now it’s time to set up MFA in your tenant. First, log into the Office 365 admin portal (https://portal.office.com) and select Active Users on the left menu. In the Active Users window, select the More drop-down menu, and select Setup Azure multi-factor auth.
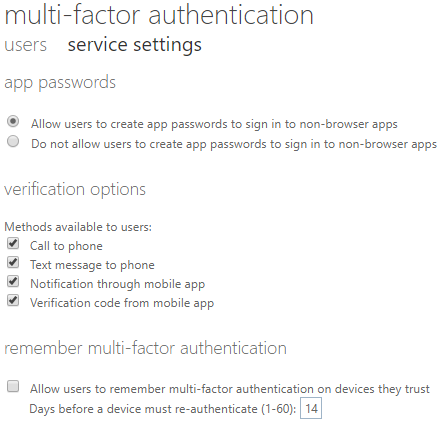
In the multi-factor authentication page, select the Service Settings menu to view the various options for creating app passwords, verification options, and MFA timeouts. For now, I am leaving all MFA options enabled. When finished, click Save and click back on the User menu.
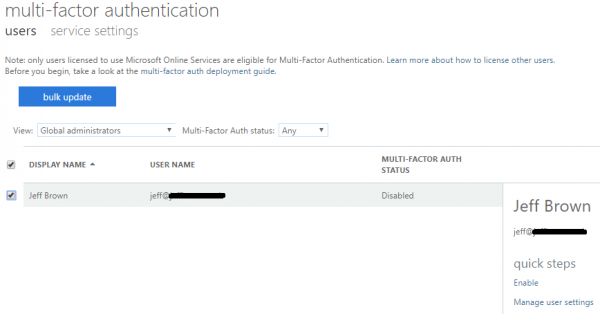
Next, select the user(s) to enable for MFA, and select Enable underneath Quick Steps on the right. The steps for enabling are pretty straight forward, and once completed, the user’s Multi-Factor Auth Status is now Enforced.
Now that the user is enabled, he or she will need to configure their preferred MFA option. If the user regularly uses a web application, such as Outlook on the Web or OneDrive, the next time the user navigates to those pages, he or she will need to set up MFA. If they do not use web applications often, a different URL is provided to send them when they were enabled in the previous step. For myself, I decided to navigate to outlook.office.com and was presented with the following screen to set up my account with additional security verification.
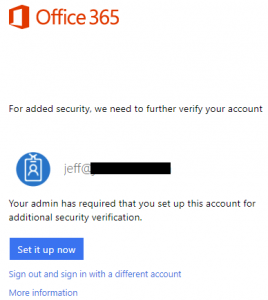
After clicking Set it up now, I had the option to select which MFA format I wanted: Authentication Phone, Office Phone, or Mobile App. I opted for the mobile app option using Microsoft Authenticator for iPhone and to provide a verification code. After select the mobile app option, click Set up.
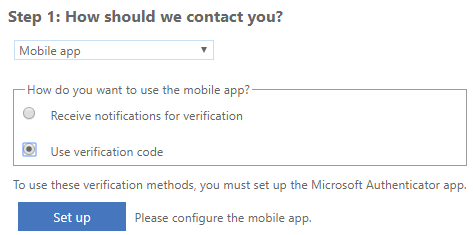
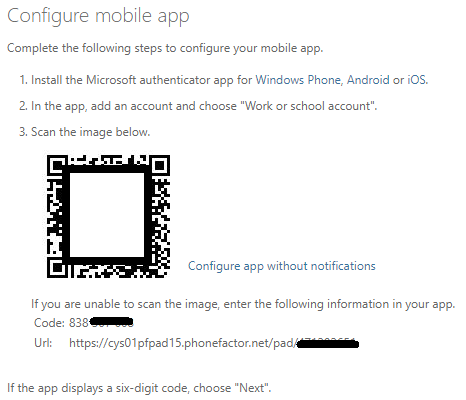
The next page presents the instructions on how to configure the mobile app with a QR code to link your account. After following the instructions and completing the set up, the account was added to my authenticator app with a 6-digit code that refreshes every 30 seconds. This code is entered into the web site to complete the set up.
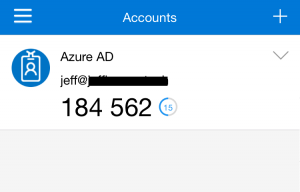
Authentication code from the mobile app:
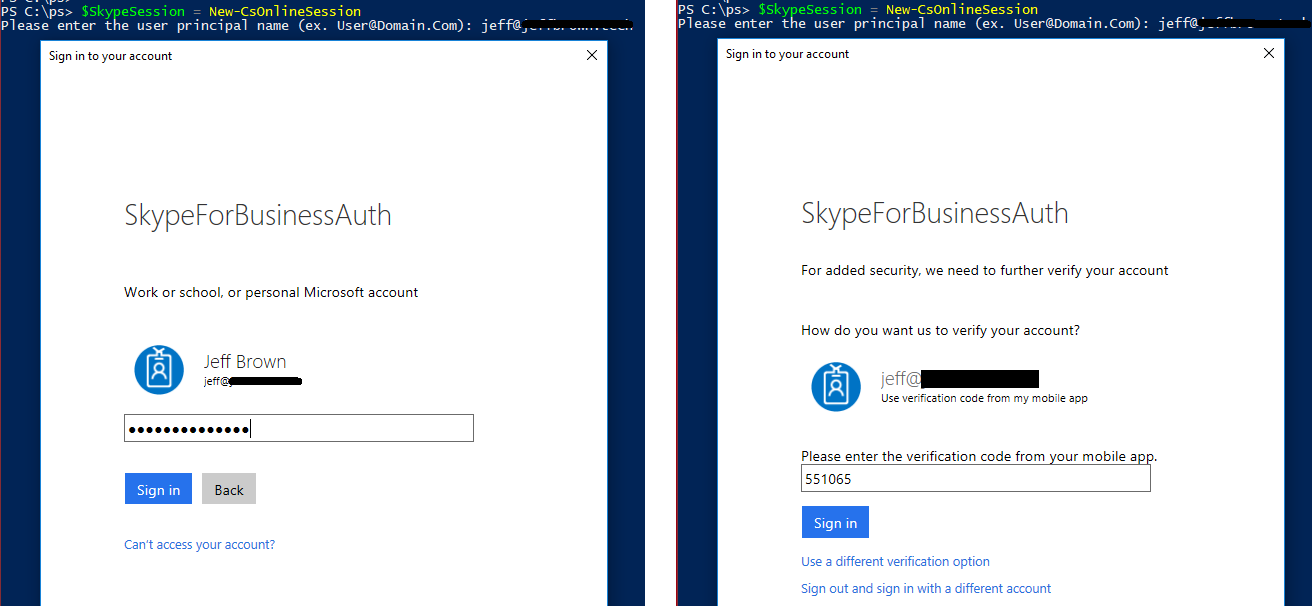
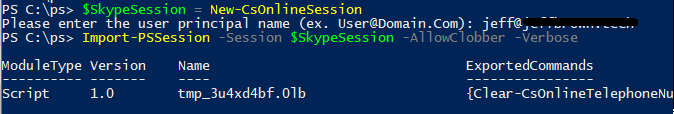
After completing set up, I was redirected to Outlook on the Web, but this wasn’t our final goal. Let’s return to a new PowerShell window and create a new CsOnlineSession. In the announcement above, Microsoft specifies that when using an account with MFA enabled, you can no longer use a PSCredential object when creating the session. This means when using the New-CsOnlineSession, specify just a username or leave it blank as it will prompt for the username. After entering the command, I was prompted for the user principal name to use, and then the SkypeForBusinessAuth window appeared. Here I entered my username’s password and was redirected to another security page to enter the 6-digit code from my mobile app. After the session was created successfully, I imported the session using the Import-PsSession command and successfully connected to the PowerShell session.
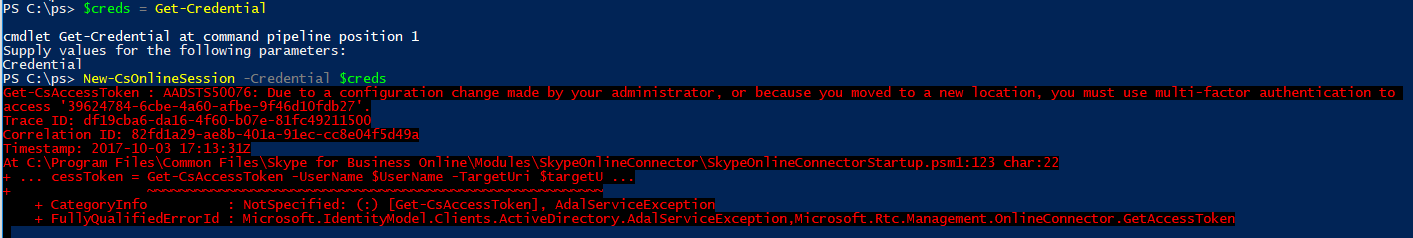
If you attempt to use a PSCredential object when creating the session, you will receive an error stating that you must use multi-factor authentication to access the tenant:
References:
Set Up Multi-Factor Authentication for Office 365 Users
Modern Authentication for the Skype for Business Windows PowerShell Module
Did you find this article helpful? Leave a comment below or follow me on Twitter (@JeffWBrown) for more information on Skype for Business and Microsoft Teams.
Skype for Business Online – Enabling MFA for PowerShell Sessions
by Jeff Brown on October 3rd, 2017 | ~ minute read


So how do I combine MFA and scripting tasks ?
Something like a windows scheduled task, running a script every X hours/days connecting to Skype Online.
Hi GW,
Without testing, I do not think MFA would work in a scheduled task scenario. You have to provide some other factor during the creation of the PowerShell session, whether it is a numeric code or approval in the authenticator app. If it were automated, someone would constantly be pestered with the second-factor authentication method. Unfortunately any account that is used to schedule the task would probably have to remain without MFA. Ideally this is a service account with limited permissions and a long, complex password.