Setting it all up
Who are we trying to secure against?
- Think of millions of people and thousands of companies in hundreds of countries

- Who?
- Script Kiddies
- Hackers/Thieves
- Industrial Espionage
- Terrorist
Most aren’t trying to protect themselves from state agencies. They have vast intercept networks and the capability to break through most security
Here’s the risk
- A hack means your users or potential users know longer trust you or your data
- Data leakage, corruption, deletion etc.
IBM SaaS is securing a number of things.
- Users, administrators, builders, operators
- Data, programs, and a host of other things
It’s in the best interest of both IBM and the users of SmartCloud for Social Business for it to be secure. In order to do so, you have to take a holistic approach to what you secure
- Client machines, laptops, mobile devices, etc.
- On the netwrox. Think of proxies, reverse proxies, routers, etc.
- On the application servers
- Data in flight
- Data in the data centers. This is both completely at rest and partially at rest (in memory cache)
What are the kinds of attacks
- Viruses and worms
- spyware
- phishing
- machines imitating people
- spam
- denial of serice
- intrusion via weakness in processers
- Replay
What do they do for all this?
- Censor incoming requests via firewalls, virus scanning, active content
- INtrustion detection
- Automated network management
- Encryption
- Forsenics for evidence and legal
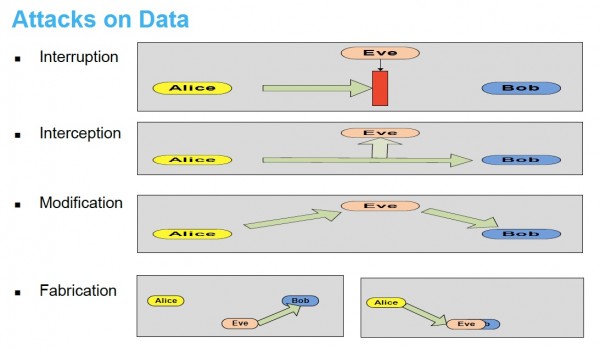
Eve is the hacker here
What is SmartCloud For Social Business Doing?
Encryption and Identification
It’s enforcing secure traffic by:
- HTTPS for Web Traffice
- NRPC encryption
- Sametime Protocol
- Opportunistic TLS for SMTP
- Give options for encryption of stored data. (very helpful in the healthcare world)
- Defensive engineering like encrypt email if the client supports encrypted email.
This is with every web request that they monitor and apply encryption.
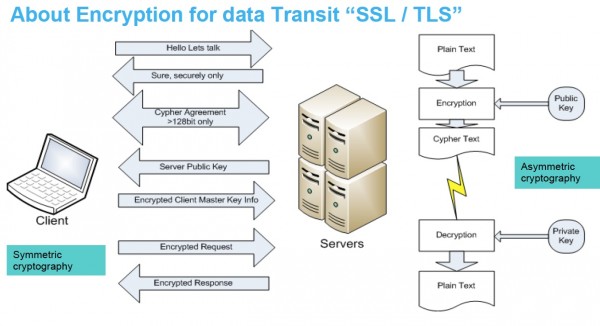
Asymetric: Once you have the public key, you can encrypt it. But only the holder of the private key can decrypt it. This is computationally extensive. Lots bigger data size and more compute cycles. It’s the price you pay for asymetric encryption.
Symetric: Do this after you have setup the public and private keys via asymetric
Have to think about rules on encryption. IBM won’t take anything less than 128 bit encryption
Smart Cloud for Social Business (SC4SB) uses extended validation certificates for all web facing points. These are cryptographically signed by a trusted authority like Verisign, GeoTrust, Comodo, and Symantec.

It’s always a good idea to check the certificate.
IBM uses the extended certificates. “We go and spend a HUGE amount of money to get the best certificates in the world”
SmartCloud does use Akamai Network acceleration
It’s great for performance and allows for worldwide caching and optimization. It’s used for the Engage and Sametime applications.
For security, TLS is terminated at the Akamai edge and is reestablished on the route to the SmartCloud data center. This makes it harder to come in via Akamai.
Note: IBM does not cache customer data. They cached style sheets, images, and other pieces of the overall application.
Encryption At Rest
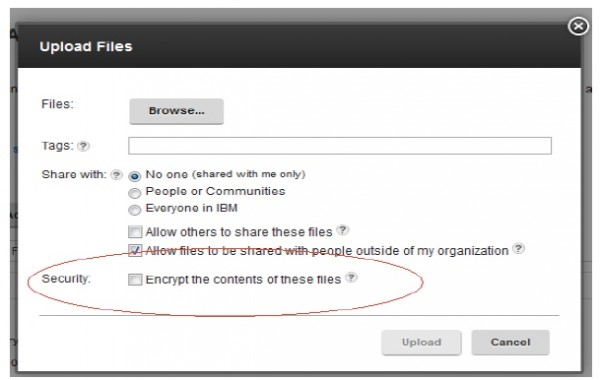
Via the admin console, you can set you encryption setting for data at rest. Not sure if this is files only.
Viruses, Worms, etc.
IBM uses active virus scanners for all data uploaded to SC4SB. The servers are also periodically scanned. The virus db are updated frequently and the OS’s are patched regularly.
Intrusion Protection
SC4SB has a variety of gates against this.
- There is no illegitimate access to the servers …… as far as they know
- Secure Software Engineering
- Do threat modeling
- employ ethical hacking
- User IBM security tools to scan code and the system
- Intrusion prevention systems scan incoming traffic looking for intrusion patterns
- Servers are scanned periodically for open vulerabilityes
- Layered architecture
- Use the standard DMZ approach to their architecture with multiple tiers and firewalls.
Phishing Attacks
SC4SB uses active content filtering to prevent cross site scripting. They also use a secure engineering approach to prevent code against vulnerabilities. User supplied links must be fully readable.
Protecting authenticity
- Maintain secure sessions with the servers
- Replay protection via unique session and request tokens
- Robust SSO integration using SAML
- Oauth is available for custom application integration
- Have incoming IP range restrictions
- Will do Directory Synchronization
We ran out of time but he still had a wide range of topics to address including;
- Protecting against spam
- Denial of Service Attacks
- Accidental leakage
- Protecting against infrastructure failure
- Incident response to review any security events.

Thanks for sharing your insights Michael. You raise some very valid points here. Great post!
Pingback: Google Play gift card Hack