In the interconnected landscape of modern software development, Application Programming Interfaces (APIs) have emerged as the linchpin, facilitating seamless communication and integration between diverse systems. As the digital ecosystem expands, the need to fortify APIs against potential vulnerabilities becomes paramount. This blog delves into the intricacies of API security, unraveling 12 indispensable tips to bolster the defense of your API infrastructure.
Demystifying APIs
What is an API, and Why is it Used?
An API, or Application Programming Interface, is a collection of protocols and tools that allow various software programs to communicate with one another. It acts as a bridge, allowing developers to access the features of a system, library, or service without diving into its core workings. APIs are the foundation of modern applications, promoting interoperability and allowing developers to construct integrated, feature-rich software.
What is API Security?
API security is the process of creating safeguards to protect APIs from unauthorized access, data breaches, and other possible dangers. APIs permit the flow of sensitive information across systems, therefore their security is critical for safeguarding data integrity, confidentiality, and availability.
Different Types of API Security
- Authentication: Verifying the identity of users or systems accessing the API.
- Authorization: Determining the permissions and privileges granted to authenticated users or systems.
- Encryption: Securing data in transit by encrypting the communication between systems.
- Input Validation: Validating and sanitizing input data to prevent injection attacks.
- Rate Limiting: Controlling the number of requests a user or system can make within a specified time frame.
12 Guidelines for API Security
1. API Versioning
- Why is it important? API versioning guarantees that API updates do not break current functionality for users who rely on certain versions. It enables backward compatibility and a smooth transition for users to new capabilities.
- Best Practice: Implement a versioning technique to explicitly describe and manage API versions by including a version number in the URL or header.

2. Allowlist
- Why is it important? An allowlist (or whitelist) limits API access to a specified set of allowed entities, lowering the attack surface by preventing access to unauthorized individuals or systems.
- Best Practice: Precisely identify and maintain a list of trustworthy entities that are permitted to access the API while denying access to all others.
3. Check OWASP API Security Risks
Why is it Important? The Open Web Application Security Project (OWASP) comprehensively lists API security risks. Regularly checking and addressing these risks enhances the overall security posture of your API.
Best Practice: Conduct regular security audits and vulnerability assessments based on the OWASP API Security Top Ten to identify and remediate potential risks.

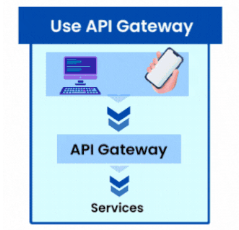
4. Use API Gateway
- Why is it important? API gateways serve as intermediates between clients and services, offering a centralized location for security, authentication, and traffic control.
- Best Practice: Implement an API gateway to manage authentication, authorization, logging, and other security-related duties, resulting in a single and secure entry point for your API.
5. Error Handling
- Why is it important? Detailed error messages may accidentally reveal sensitive information or offer attackers insight into an API’s underlying workings. This danger can be mitigated with proper error management.
- Best Practice: Create generic error messages for users and extensive error logs for developers. Avoid revealing stack traces or internal system information in error answers.

6. Input Validation
- Why is it important? Input validation stops unauthorized actors from injecting harmful data into your API, hence reducing typical security issues like SQL injection and cross-site scripting.
- Best Practice: Validate and sanitize all incoming data to ensure it follows anticipated forms and contains no harmful information.
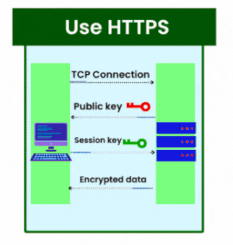
7. Use HTTPS
- Why is it important? Encrypting data in transit is critical for safeguarding sensitive information against eavesdropping and man-in-the-middle attacks.
- Best Practice: Enforce using HTTPS (HTTP Secure) to encrypt data sent between clients and the API server, creating a secure communication channel.
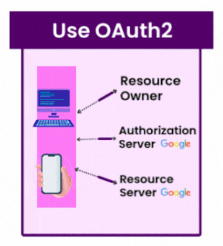
8. Use OAuth2
- Why is it important? OAuth2 is a secure and standardized authentication and authorization mechanism that allows you to grant access to resources without disclosing your credentials.
- Best Practice: Implement OAuth2 for safe and standardized authentication and authorization processes, guaranteeing that only authorized users and systems may access the API.
9. Use WebAuthn
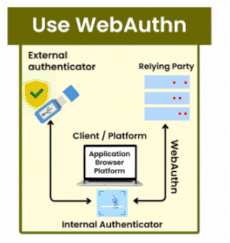
- Why is it important? WebAuth is a modern authentication standard that improves security by allowing users to log in with biometrics, security keys, or other strong authentication methods.
- Best Practice: Implement WebAuth to tighten user authentication, reduce the danger of compromised credentials, and improve overall API security.
10. Use Leveled API Keys
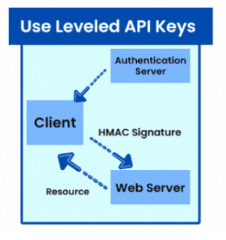
- Why is it important? Using several levels of API keys enables more granular control over access privileges. This aids in applying the principle of least privilege, ensuring that users or systems only have access to the required resources.
- Best Practice: Assign API keys to specified roles or scopes, providing access to just the resources and activities required by the user or system.
11. Authorization
Why is it Important? Authorization ensures that authenticated users or systems have the appropriate permissions to perform specific actions within the API, preventing unauthorized access.
Best Practice: Implement role-based access control (RBAC) or attribute-based access control (ABAC) to define and enforce authorization policies based on user roles or attributes.
12. Rate Limiting
Why is it Important? Rate limiting controls the number of requests a user or system can make within a specified time frame, mitigating the risk of abuse, DoS attacks, or unintentional resource exhaustion.
Best Practice: Implement rate-limiting policies to control API requests’ frequency, prevent abuse and ensure fair usage of resources.
Example:
Basic API Gateway Security with JWT in Java (Kong Example)
This example simulates a scenario where a client requests user information from a backend service exposed through Kong, a popular API Gateway. Here, Kong validates the request using a JWT (JSON Web Token) before forwarding it. The Java code resides within the backend service.
Components:
- Kong: Acts as the API Gateway and enforces security policies.
- Java Backend Service: Provides user data (replace it with your actual service).
Here’s a breakdown of the implementation:
1. Kong Configuration (Pseudo-code):
# Route for GET /users/{id} requests
GET /users/{id} -> UserService
# JWT Validation Plugin Configuration
plugin {
name = "jwt"
config {
# Secret key used for JWT signing (replace with yours)
secret = "your-secret-key"
# Audience claim to validate (optional)
audience = "your-api-gateway"
}
} 2. Java Backend Service (with JWT validation logic):
@RestController
@RequestMapping("/users")
public class UserController {
@Autowired
private UserService userService;
@GetMapping("/{id}")
public ResponseEntity<User> getUserById(@RequestHeader("Authorization") String authorization) {
if (authorization == null || !isValidToken(authorization)) {
return ResponseEntity.status(HttpStatus.UNAUTHORIZED).build();
}
long userId = getUserIdFromToken(authorization); // Parse user ID from token
User user = userService.getUserById(userId);
if (user != null) {
return ResponseEntity.ok(user);
} else {
return ResponseEntity.notFound().build();
}
}
private boolean isValidToken(String authorization) {
String token = authorization.replace("Bearer ", "");
// Replace with your JWT validation library (e.g., JJWT)
try {
Claims claims = Jwts.parser().setSigningKey("your-secret-key").parseClaimsJws(token).getBody();
// Optional: validate audience claim
return claims.getAudience().contains("your-api-gateway");
} catch (Exception e) {
return false;
}
}
private long getUserIdFromToken(String token) {
// Replace with logic to extract user ID from claims
Claims claims = Jwts.parser().setSigningKey("your-secret-key").parseClaimsJws(token).getBody();
return claims.getSubjectAsLong(); // Assuming user ID is in subject claim
}
} Explanation:
- Kong enforces JWT validation using a plugin with your secret key configured.
- The backend service retrieves the JWT from the
Authorizationheader. - It uses a library like JJWT (not included) to parse and validate the JWT signature and claims.
- The example validates the audience claim (optional) to ensure the token is intended for this API Gateway.
- If the token is valid, the user ID is extracted from the claims.
- The service then retrieves user data using the user ID and returns the appropriate response.
Important Notes:
- This is a simplified example and doesn’t cover error handling or logging comprehensively.
- You’ll need to replace placeholders with your actual secret key, audience claim (if used), and logic for extracting user ID from the token.
- Remember to configure JWT signing on the service that generates the tokens.
Conclusion:
In today’s changing digital connection world, API security is critical to protecting sensitive data, maintaining user confidence, and strengthening the resilience of digital ecosystems. The 12 guidelines provided in this blog offer a thorough reference for developers, architects, and security practitioners looking to improve the security posture of their APIs.
As organizations continue to leverage APIs for seamless integration and communication, the onus lies on the guardians of these gateways to implement robust security measures. From versioning and allowlisting to employing OAuth2 and WebAuth, each tip contributes to building a multi-layered defense against potential threats.
In the quest for digital innovation and interconnection, API security becomes a strategic objective rather than a need. By adopting and applying these best practices, businesses can confidently traverse the changing threat landscape, ensuring that their APIs remain bastions of security in an era dominated by digital data interchange.


