Microsoft Cloud App Security (MCAS) is Microsoft’s Cloud App Security Broker (CASB) solution that provides organizations with simple deployment, centralized management, and innovative automation capabilities. One of the great features within MCAS that not many administrators leverage (or even know about) is the ability to save your custom queries! In this blog, we’ll create our own query, and then we’ll highlight how to save the query and even turn that query into its own policy! Let’s get started!
Creating a custom query
Let’s start by navigating to portal.cloudappsecurity.com. Once there, we’re going to go to the Investigate tab and then select Activity log.
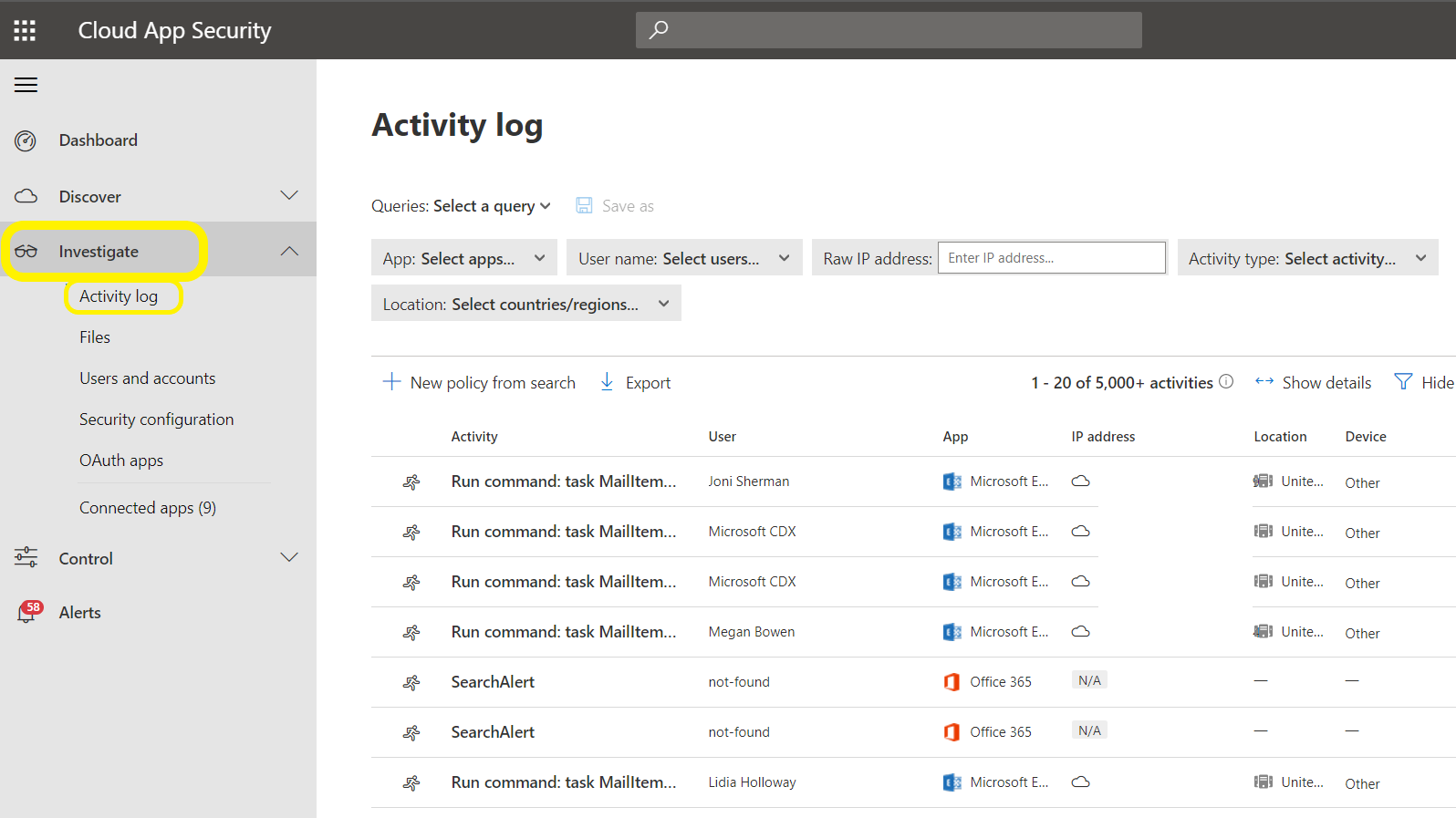
Now that we’re where we need to perform a query, you should see the “Select a query” option at the top. Microsoft gives you 10 suggested queries to choose from, but in our case, we’re going to create our own!
Creating and using the custom query
For our scenario, I’ll use something we came across with a recent customer, that being ActiveSync. Since Exchange ActiveSync is not designed to be used for server-to-server communications in the online environment, the customer wanted to block ActiveSync and instead leverage more modern authentication methods. To block this, we were going to leverage Conditional Access rules. However, we weren’t entirely sure how many users were leveraging ActiveSync within the environment. Thanks to MCAS, we’re able to create a custom query that will show us who is using ActiveSync today to properly plan for this change. To do this, we would need to toggle the Advanced Filters option to On and then select the following filters:
Device >Type > Equals > Mobile
Activity Type > Equals > ”Log on: OrgIdWsTrust2:process” and “Failed Log On: OrgIdWsTrust2:process”
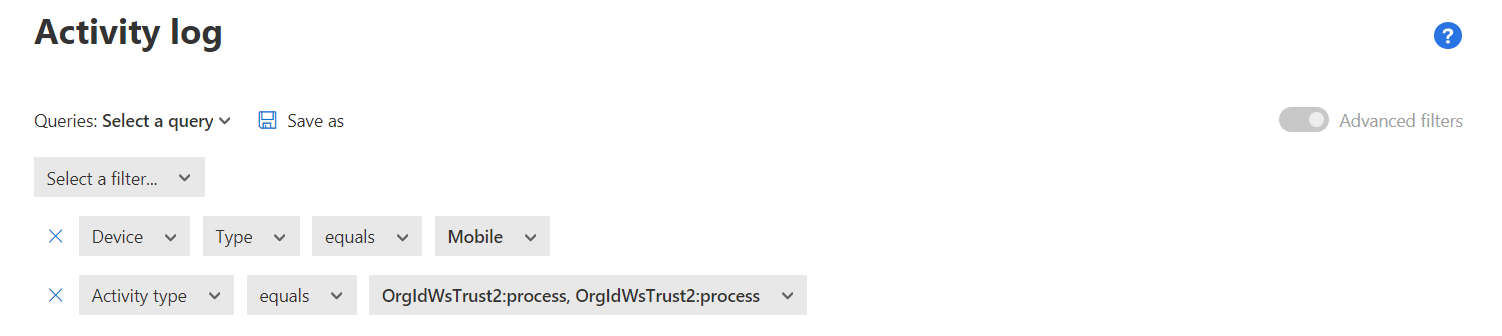
So, in summary, this query is “saying,” find any mobile device with ActiveSync data. Since new users are constantly joining the organization, we will want to run this report daily to keep the reports as up-to-date as possible. Instead of finding these advanced filters each and every time you want to run this report, MCAS gives you the ability to save a query! To do that, just select the “Save as” option, name the query, and that’s it! Now when you come into work the next day, you’ll be able to easily find and run that particular query!
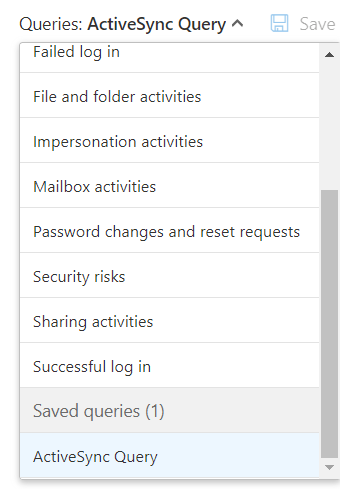
Turning your query into a policy
We can even take things a step further by turning this query into its own custom policy! To do this, just select the ” + New Policy from search” option below the query. You’ll notice all of the filters and conditions will be pre-populated for you, so all you’ll need to do is add a name to your policy, select a category to classify your query, include a description (optional), and add any actions that you want to be performed when the policy is triggered.
It’s as simple as that! MCAS is a potent tool, and with the amount of flexibility and customization at your fingertips, the capabilities are endless! I hope you have found this article helpful, and I encourage you to check back soon for more Microsoft-related content!

Hi Brian, I don’t have an Investigate tab, just Discover, Control and Alerts. How do I get to Investigate?
Hi Phil,
Apologies for the late reply. This could likely be due to one of the following:
1) Licensing – What licensing do you currently have in your tenant? If you only have E3 licensing this could be the culprit. Unfortunately E3 licensing won’t cut it with MCAS you’ll need E5 licensing. You can check out all the licensing required for MCAS here: https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2NXYO
2) Insufficient admin permissions. You will need either the Global Administrator or Security Administrator role to access and make changes within MCAS. However, since it sounds like you have access to MCAS but just don’t see the “Investigate” tab, this probably isn’t the issue.