Retain full control of your organization’s sensitive data that is accessed, stored, and transmitted to other parties with Oracle ERP Cloud Payment.
Companies generate and collect a staggering amount of data every single day. Much of this data is sensitive and needs to be protected. Still, data breaches occur all too frequently in the form of insider attacks, inadvertent insider leaks, or an employee forgets an envelope on a metro rail seat. Data is pervasive, and security a tough thing to do and even harder to do right. However, there are things companies can do to protect themselves and have a little better hygiene overall.
Oracle ERP system is a repository of financial transactions containing sensitive information that requires protection. To protect your credit card and external bank account information, Oracle Cloud Payment system provides the tools to enable your information security policies and assure your employees and business partners that your business takes securing their information seriously.
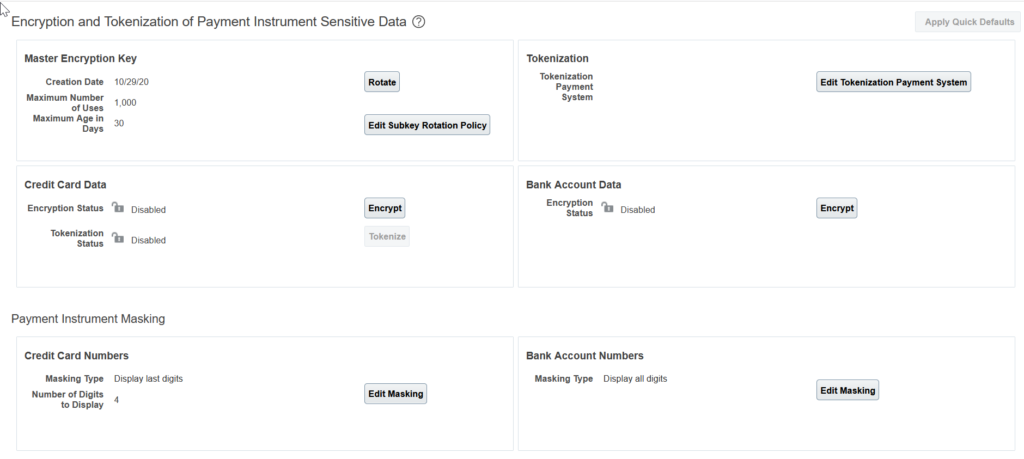
You can set the application security to align with your enterprise’s security policy. You can set security options for encryption, masking, and tokenization of credit cards and bank accounts. Both funds capture/collection and disbursement processes use these security options.
Answer these security questions to improve the security of your sensitive data:
- Which security practices do I want to employ?
- Do I want to tokenize my credit card data?
- Do I want to encrypt my bank account data?
- Do I want to encrypt my credit card data?
- How frequently do I want to rotate the master encryption key and the subkeys?
- Do I want to mask credit card and bank account numbers?
Leading Security Practices for payment processing:
- Comply with the Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is the security standard required for processing most types of credit cards.
- Comply with all requirements for accepting credit card payments.
- Minimize the risk of exposing sensitive customer data.
- Create the master encryption key.
- Rotate the master encryption key periodically.
- Share key pairing with your bank/ or payment system.
Enable Encryption, Masking, and Tokenization.
Considerations for data protection should include the following:
- Consider implementing segregation of duties and a multi-party protocol for establishing MasterKeys to eliminate a single point of control/failure.
- Establish and manage consistent encryption and key management policies.
- Consider implementing automated key lifecycle management processes.
- Only owning organizations should have access to their data.
- Owning organizations govern all cryptographic keys, not service providers.
The above considerations should not be viewed as static one-time actions. Practicing these recommendations at a regular cadence can result in an improved data security program. If you’re considering a move to Oracle ERP Cloud, Perficient has a dedicated Oracle ERP practice to help you with your cloud journey.

