
Security in the cloud is a critical concern of every customer who leverages cloud offerings. IBM InterConnect 2016 had a very informative session with great speakers, Staying Secure in the Cloud with SaaS. The following IBM leaders presented:
- David Cass, Chief Information Security Officer, IBM Cloud
- Nathan Reid, Director, Cloud Engineering, IBM Analytics
- Dave Durazzano, Offering Manager, IBM Social Cloud
The key topics covered include:
Threat Landscape
- There has been a 40% increase in reported breaches in the last 3 years
- Security leaders are more accountable than ever
- Risks include loss of market share, legal, fines, impact to data and systems, violation of privacy policies, loss of trust
Offerings
IBM has 150+ Cloud Security Offerings
- Executive level of support for CIO, cloud operations, VP cloud security and CISO cloud
- Offerings know who has access to data and where is it accessed from
- Security requirements addressed in deployment checklist before going to market
SaaS Security components include
- Delivers SaaS solutions and takes care of individual needs including
- Pen testing
- Separation of Duties
- Shared operating servies
- Encryption
- Logging and monitoring
- All SaaS offerings going through ISO 27001 certification
- Standardized on SoftLayer platform
- Data centers are geographically distributed
- IBM takes a leadership position on new security standards
Service Development
Secure Engineering Practices are in in place at all stages of development life-cycle.
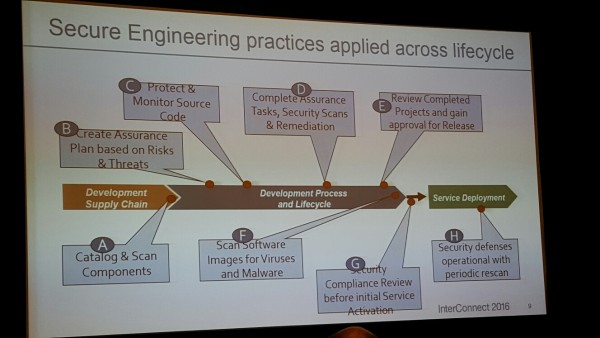
Service Delivery
How IBM Protects Client Data
- Physical, logical, organizational and engineering controls are in place
- Governance focused on continuous assessment & enhancement
- Shared services for vulnerability scanning, intrusion detection, log storage and more are provided
- Architectural separation of data stores is implemented
- Encryption is pervasive
- Over 2,000 pages of confidential authoritative internal security policies
IBM offerings support virtually all important compliance regimes including ISO standards, HIPAA / HITECH, PCI DSS, EU Model Clauses and many more
Service Consumption
How do clients protect their data when using SaaS? They should:
- Classify data correctly
- Configure services correctly
- Train workforce sufficiently
- Leverage controls as intended
- Verify cloud service provider’s audit posture
- Review log analytics and usage
The remainder of the session was an open panel discussion. It is clear that security is at the forefront of every phase, decision and aspect of all of IBM’s SaaS offerings and customers can be assured IBM solutions are among the most secure in the industry. Additional references include:
