Introduction to DevSecOps
DevSecOps is the evolution of DevOps with a focused integration of security throughout the software development lifecycle (SDLC). It promotes a cultural and technical shift by “shifting security left,” integrating security early in the CI/CD pipeline instead of treating it as an afterthought.

While DevOps engineers focus on speed, automation, and reliability, DevSecOps engineers share the same goals with an added responsibility: ensuring security at every stage of the process.
DevSecOps = Development + Security + Operations
By embedding security from the beginning, DevSecOps enables organizations to build secure software faster, reduce costs, and minimize risks.
Why Shift Left with Security?

Cost Savings

Early Detection
Shifting security left means embedding security checks earlier in the pipeline. This approach offers several key benefits:
- Early Detection: Identifies vulnerabilities before they reach production.
-
Cost Savings: Fixing security issues in earlier phases of development is significantly more cost-effective.
-
Reduced Risk: Early intervention helps prevent critical vulnerabilities from being deployed.
Implementing DevSecOps in an Existing CI/CD Pipeline
Prerequisites
To implement DevSecOps in your Azure DevOps pipeline, ensure the following infrastructure is in place:
-
Azure VM (for self-hosted Azure DevOps agent)
-
Azure Kubernetes Service (AKS)
-
Azure Container Registry (ACR)
-
Azure DevOps project and repository
-
SonarQube (for static code analysis)Docker Registry Service Connection
Service Connections Setup
1. Docker Registry Connection
-
Go to Azure DevOps → Project Settings → Service Connections.
-
Click “New service connection” → Select Docker Registry.
-
Choose Docker Hub or ACR.
-
Provide Docker ID/Registry URL and credentials.
-
Verify and save the connection.
2. AKS Service Connection
-
Azure DevOps → Project Settings → Service Connections.
-
Click “New service connection” → Select Azure Resource Manager.
-
Use Service Principal (automatic).
-
Select your subscription and AKS resource group.
-
Name the connection and save.
3. SonarQube Service Connection
-
Azure DevOps → Project Settings → Service Connections.
-
New service connection → SonarQube.
-
Input the Server URL and token.
-
Save and verify.
Main Features Covered in DevSecOps Pipeline
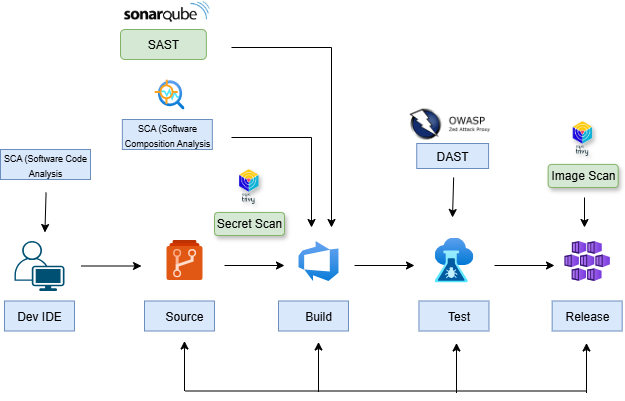
-
Secret Scanning
-
Dependency Scanning (SCA)
-
Static Code Analysis (SAST)
-
Container Image Scanning
-
DAST (Dynamic Application Security Testing)
-
Quality Gates Enforcement
-
Docker Build & Push
-
AKS Deployment
Pipeline Stages Overview
1. Secret Scanning

Tools
detect-secrets, Trivy
Steps
-
Install Python and
detect-secrets. -
Scan source code for hardcoded secrets.
-
Run
Trivywith--security-checks secret. -
Save results as HTML → Publish to pipeline artifacts.
-
Apply quality gates to fail builds on critical secrets.
2. Dependency Scanning (SCA)

Tools
Safety, Trivy
Steps
-
Use
requirements.txtfor dependencies. -
Run
Safetyto identify known vulnerabilities. -
Scan the filesystem using
Trivy fs. -
Publish results.
-
Fail pipeline if critical vulnerabilities exceed the threshold.
3. Static Code Analysis (SAST)

Tools
SonarQube, Bandit
Steps
-
Use
Banditfor Python security issues. -
Run SonarQube analysis via CLI.
-
Enforce SonarQube Quality Gate to fail the pipeline on low scores.
4. Container Image Build & Scan
Tools
Docker, Trivy
Steps
-
Build the Docker image with a version tag.
-
Scan the image using
Trivy. -
Generate and publish scan reports.
-
Apply a security gate — fail on high-severity vulnerabilities.
-
Push image to ACR if passed.
5. DAST – OWASP ZAP Scan
Tools
OWASP ZAP
Steps
-
Run the app in a test container network.
-
Perform ZAP baseline scan.
-
Save results as HTML.
-
Stop the test container.
-
Apply a security gate to block high-risk findings
6. Deploy to AKS

Tools
kubectl, Kubernetes
Steps
-
Fetch AKS credentials.
-
Use
envsubstto fill in manifest variables. -
Deploy the app via
kubectl apply. -
Trigger a pod restart to deploy a new image.
Conclusion
DevSecOps is not just a practice; it’s a mindset. By integrating security at every phase of your CI/CD pipeline, you’re not only protecting your software but also enhancing the speed and confidence with which you can deliver it.
Implementing these practices with Azure DevOps, SonarQube, Trivy, and other tools makes securing your applications systematic, efficient, and measurable.
Secure early. Secure often. Secure always. That’s the DevSecOps way.

