In the ever-evolving landscape of cloud computing, Infrastructure as Code (IaC) has emerged as a cornerstone practice for managing and provisioning infrastructure. IaC enables developers to define infrastructure configurations using code, ensuring consistency, automation, and scalability. AWS CloudFormation, a key service in the AWS ecosystem, simplifies IaC by allowing users to easily model and set up AWS resources. This blog explores the best practices for utilizing AWS CloudFormation to achieve reliable, secure, and efficient infrastructure management.
Why Use AWS CloudFormation?
AWS CloudFormation provides a comprehensive solution for automating the deployment and management of AWS resources. The primary advantages of using CloudFormation include:
- Consistency: Templates define the infrastructure in a standardized manner, eliminating configuration drift.
- Automation: Automatic provisioning and updating of infrastructure, reducing manual intervention.
- Scalability: Easily replicate infrastructure across multiple environments and regions.
- Dependency Management: Automatically handles resource creation in the correct sequence based on dependencies.
- Rollback Capability: Automatic rollback to the previous state in case of deployment failures.
Comparison with Other IaC Tools
- AWS CloudFormation stands out among other IaC tools, such as Terraform and Ansible, due to its deep integration with AWS services. Unlike Terraform, which supports multiple cloud providers, CloudFormation is tailored specifically for AWS, offering native support and advanced features like Drift Detection and Stack Policies. Additionally, CloudFormation provides out-of-the-box rollback functionality, making it more reliable for AWS-centric workloads.
Best Practices for CloudFormation
1. Organize Templates Efficiently
Modularization
Breaking down large CloudFormation templates into smaller, reusable components enhances maintainability and scalability. Modularization allows you to create separate templates for different infrastructure components such as networking, compute instances, and databases.
Example:
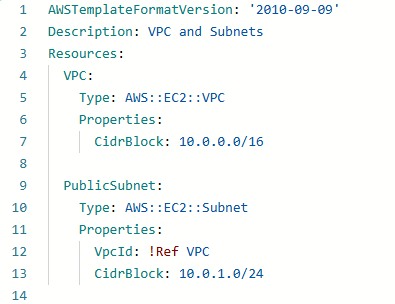
compute.yml
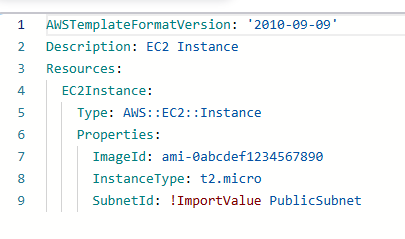
The network.yml template creates the VPC and subnets in this example, while the compute.yml template provisions the EC2 instance. You can use Export and ImportValue functions to share resource outputs between templates.
Nested Stacks
Nested stacks allow you to create a parent stack that references child stacks, improving reusability and modularization.
Example:
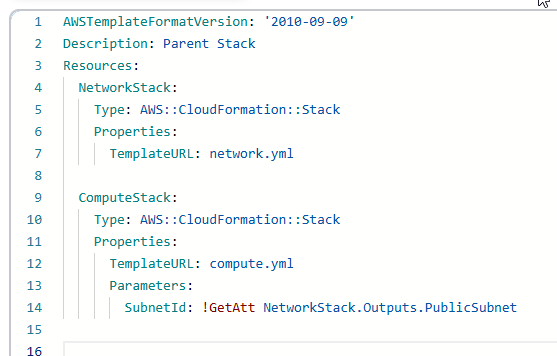
Using nested stacks ensures a clean separation of concerns and simplifies stack management.
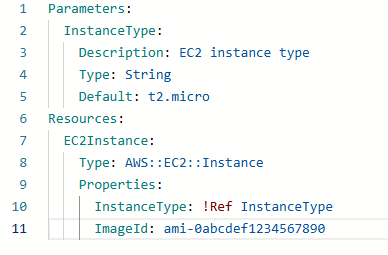
2. Parameterization and Reusability
Enhance template reusability and flexibility through parameterization:
- Parameters Section: Define configurable values such as instance types, environment names, and AMI IDs.
- Mappings Section: Use mappings to create static mappings between parameter values and resource properties.
- Default Values: Set default values for optional parameters to simplify deployments.
- AWS CloudFormation Macros: Use macros to extend template functionality and perform custom transformations.
Example:
3. Security Considerations
Securing infrastructure configurations is paramount. Best practices include:
- IAM Roles and Policies: Assign least privilege permissions to CloudFormation stacks and resources.
- Secrets Management: Store sensitive data such as passwords and API keys in AWS Secrets Manager or Systems Manager Parameter Store.
- Encryption: Enable encryption for data at rest using AWS KMS.
- Stack Policies: Apply stack policies to protect critical resources from unintended updates.
Example:
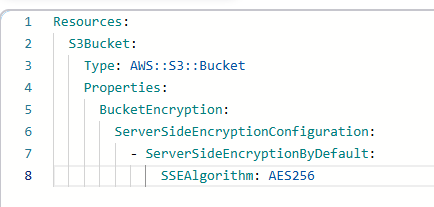
4. Version Control and Automation
Integrating CloudFormation with version control systems and CI/CD pipelines improves collaboration and automation:
- Version Control: Store templates in Git repositories to track changes and facilitate code reviews.
- CI/CD Pipelines: Automate template validation, deployment, and rollback using AWS CodePipeline or Jenkins.
- Infrastructure as Code Testing: Incorporate automated testing frameworks to validate templates before deployment.
Example Pipeline:
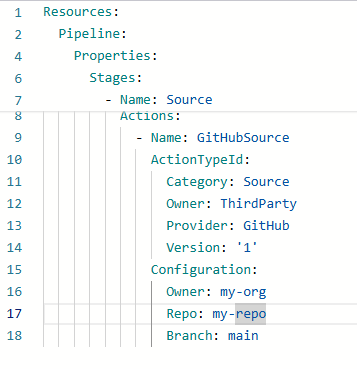
5. Template Validation and Testing
Validation and testing are critical for ensuring the reliability of CloudFormation templates:
- Linting: Use the cfn-lint tool to validate templates against AWS best practices and syntax rules.
- Change Sets: Preview changes before applying them using CloudFormation Change Sets.
- Unit Testing: Write unit tests to verify custom macros and transformations.
- Integration Testing: Deploy templates in isolated environments to validate functionality and performance.
Example:
cfn-lint template.yml aws cloudformation create-change-set --stack-name MyStack --template-body file://template.yml
6. Stack Policies and Drift Detection
Protecting infrastructure from unauthorized changes and maintaining consistency is essential:
- Stack Policies: Define stack policies to prevent accidental updates to critical resources.
- Drift Detection: Regularly perform drift detection to identify and remediate unauthorized changes.
- Audit Trails: Enable AWS CloudTrail to log API activity and monitor changes.
Example Stack Policy:
- Define the Stack Policy in a separate JSON file:
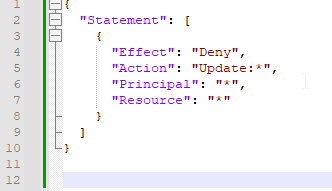
- Apply the policy while creating or updating the stack:
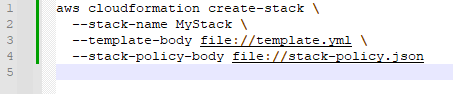
AWS CloudFormation Architecture
Below is a high-level architecture diagram illustrating how AWS.
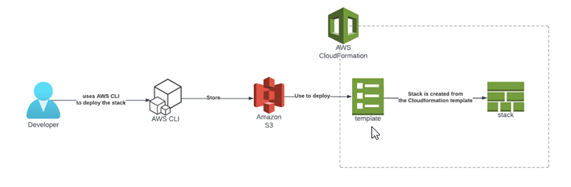
Step-by-Step Configuration
- Create a CloudFormation Template: Write the YAML or JSON template defining AWS resources.
- Upload to S3: Store the template in an S3 bucket for easy access.
- Deploy Stack: Create the stack using the AWS Management Console, CLI, or SDK.
- Monitor Stack Events: Track resource creation and update progress in the AWS Console.
- Update Stack: Modify the template and update the stack with the new configuration.
- Perform Drift Detection: Identify and resolve configuration drift.
Conclusion
AWS CloudFormation is a powerful tool for implementing infrastructure as code, offering automation, consistency, and scalability. By following best practices such as template modularization, security considerations, and automation, organizations can enhance the reliability and efficiency of their cloud infrastructure. Adopting AWS CloudFormation simplifies infrastructure management and strengthens overall security and compliance.
Embracing these best practices will enable businesses to leverage the full potential of AWS CloudFormation, fostering a more agile and resilient cloud environment.


Thank you for sharing good information.