With Azure AD B2C, you can migrate and consolidate users from other identity provider systems. In this blog, I’ll walk you through one approach for migrating user accounts: a Bulk Migration in one batch.
Read More: Consolidating Users into One Identity Provider with Azure AD B2C
Bulk migration can be done with little-to-no impact to the end user as long as the user account details (such as usernames, passwords, emails, account information, etc.) are readily available in a format that can be exported to clear-text and subsequently imported into Azure B2C.
For scenarios where you are unable to easily access the user account details from the current identity provider, you can use a Just in Time migration, which you can read about here.
Bulk User Migrations
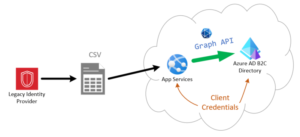
Today we will be looking at how to bulk create or migrate users from an existing identity provider into Azure B2C. In this scenario, all required user details will be exported from the current legacy identity provider to an .xlsx or .csv or some other delimited file type. Once all user details have been made available, they can be imported to Azure B2C using the Microsoft Graph API.
This migration strategy applies if the team has clear access to a user’s credentials (user name and password) or the credentials are encrypted, but the keys are available to decrypt them. The bulk migration process involves reading the users from the old identity provider via an export and using the Graph API to create new accounts in the Azure AD B2C directory.
Benefits of this approach
The benefits of this particular method are that it is relatively easy and quick to build out. There are multiple Azure Graph API SDKs available in the most popular programming languages such as:
The first step in implementing this strategy is writing the appropriate logic in the programming logic of choice to parse the user data from the file upload. Once the file upload is complete and the user data has been extracted, the web service can utilize the Microsoft Graph “Create User” HTTP POST endpoint to add the user to the B2C directory:
HTTP request: POST /users
In the request body, supply a JSON representation of user object.
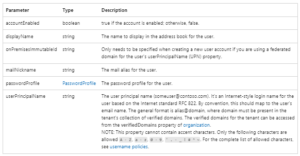
The following table lists the properties that are required when you create a user.
Potential Challenges
There are downsides to the approach, however. Namely – that the application must be brought offline for at least some portion of the migration – if the application and the existing Identity Provider are left online after exporting the user data, there is a risk of data loss as new users may be added or user data may change between the time it take export the user information and the time to bring the new B2C identity provider online.
Additionally, this migration strategy requires access to the users username and password. If the passwords are encrypted with a one-way hash or unknown then it would not be possible to use the Graph API POST endpoint to create the user. If the passwords from the legacy authentication provider are encrypted, one variation on the bulk migration is to migrate all users with a placeholder password and flag the accounts for forcing password reset the next time the user signs in:
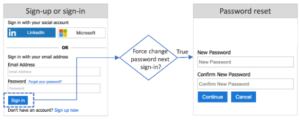
The ease of implementation and ability to quickly move all data makes this approach straight-forward. But it can result in significant impacts to the system’s user experiences – depending on the number of users, the upload to B2C may take up to 24 hrs. During this time the site would be unavailable for users to access. And even after the migrations, users may still be required to reset some of their data.
This leads us to the second migration approach: “Just In Time Migration” which we will discuss in the next part of this blog series.

