The digital world today is filled with hackers, cyberpunks, and data crackers. Data security and integrity is a major concern. We want to keep our data safe as possible to protect it from attackers, which makes managing data so important and time-consuming. We want a simple solution to use power to withstand attacks. An ansible vault provides the best of both worlds.
Using an ansible vault is easy. First, we need to have a Linux control node that supports ansible. We need the ansible package to be installed in the node to use the ansible vault. In this example, we’re using REHL 8 with Ansible-2.9.
Understanding an Ansible Vault and Its Specialties
A vault provides a mechanism to encrypt our secrets and decrypt them at the runtime when you need it. Ansible Vault is a utility that secures confidential data by encrypting that on the disk and provides it at the run time when you needed it. An ansible volt utility is integrated with “ansible” and “ansible-playbook” commands to decrypt data at the run time.
An ansible vault works on an Advanced Encryption Standard (AES), a 256 symmetric key algorithm that applies the same key for encrypting and decrypting the playbooks. For example, the implemented password.
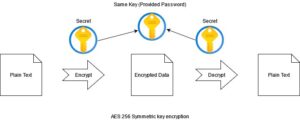
Ansible Vault: Secret Management
Ansible Vault is managed using a command-line utility called “ansible-vault.” This command is used to encrypt, view, edit, and decrypt the playbooks.
How to Create an Encrypted Play
We can create encrypted plays by using the following command:
“# ansible-vault create <Play Name>”
We’re creating a simple encrypted playbook file, which contains multiple plays, in this example. After firing the command, it prompts for a password to encrypt the file, just like in the image below:

By default, it uses vi editor. If we want to change, we simply can change the editor.
By default, it uses vi editor. If we want to change, we simply can change the editor.
Changing the Default Editor
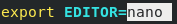
- To set the editor with every AD Hoc command. Pre pond it with environmental variable assignment for example:
![]()
- To make it persistent, open the ~./bashrc file and specify your favorite editor by specifying the EDITOR assignment at the end of the file.
And to apply changes by re-logging to your shell.
Let us continue to test the vault, we create a simple play (you can take any play) to create a user here and save changes.
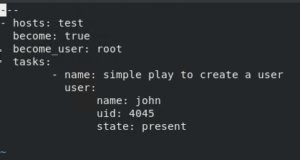
To verify if the play we save got encrypted, you need to read the file using the “cat” command and the following output presented:
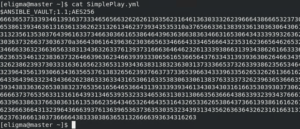
When we read the file, only the encrypted block is visible. Ansible vault uses the “AES256 symmetric key encryption” as the user-supplied password. It applies the same password for encryption and decryption of data, which makes it comfortable to use.
Encrypting the Existing Playbooks
We can encrypt an existing playbook by using the ansible-vault utility as follows:
ansible-volt encrypt <Play Name>
And verify if the playbook is got encrypted by reading the file using the cat command.
If you do not want to encrypt an original file you can create a new encrypted version of the original file using option –output.
# ansible-volt encrypt <Play Name> –output=<Encrypted play name>
We can verify if the play is encrypted by simply reading the file by using the cat command.
Viewing the Encrypted Playbooks
It’s easy to view our encryption by using the “view” option with the “ansible-vault” command followed by file name, after that it prompts for a password, which we used while encrypting the file:
“# ansible-vault view <play name>”
Editing the Encrypted Playbooks
We can edit the encrypted file by simply using the “edit” option with the “ansible-vault” command followed by the play name. It will ask for a password and open the file in our default editor, and we can make changes and save as we save our regular files.
# ansible-vault edit <play name>
Changing the Encryption Keys
We can change the encryption keys with the “help rekey” option after the ansible-vault command followed by the playbook name.
# ansible-vault rekey <play name>

Running the Encrypted Plays
We can run our encrypted plays by simply with the “–vault id @prompt” option with the ansible-playbook command:
“# ansible-playbook –vault-id @prompt <play name> -K”
“-K” is the option is used to provide a key if it uses to become some other user and execute the play.
![]()
An Ansible Vault Ensures Your Data is Safe
An ansible vault is a simple and powerful utility that enhances the security of our playbooks. It is amazingly easy to use thanks to its user-friendly nature. That magnifies its scope to be used at every point. This makes us able to implement it in each of our automation tasks, which intensifies the security of our overall infrastructure. For more information, contact our experts today.

