A majority of cyber attacks today are due to a compromised username and password. As a result, many organizations have tried to combat these threats by implementing multi-factor authentication. Although this method is significantly better than just one form of authentication, this typically leaves the end-user frustrated with the extra steps on top of just remembering the username and password. This is where passwordless authentication can shine, as it gives you the best of both worlds, security, and convenience for your end-users and organization as a whole. Three different methods can be used with passwordless authentication:
- Windows Hello for Business
- Microsoft Authenticator App
- FIDO2 security keys
In today’s blog, we’ll be covering passwordless sign-in using the Microsoft Authenticator App. This will include a breakdown of how it works, prerequisites, and how you can start using it within your organization.
How does it work?
The Microsoft Authenticator App allows you to sign in to any Azure AD account without even entering a password. It sounds almost too good to be true, but in fact, it is possible! The Microsoft Authenticator App uses something called “key-based” authentication which ties a specific user account to a device. Once the user account is tied to the device, the device then prompts for a PIN or biometric to successfully authenticate. The best thing of all, this can be used on any device platform and can be used with any website that integrates with Microsoft Authentication Libraries. So what does the end-user see when trying to authenticate if no password is required? Glad you asked! For users that have enabled the phone sign-in method from within the Microsoft Authentication App, they will be prompted to tap on a number within the app. As you’ll see in the image below when attempting to sign in to your Microsoft 365 account you will be presented with a number. Then in your authenticator app, you will need to match the number with the one you see in your browser. After matching the number, select Approve, and lastly, you’ll provide your PIN or biometric to gain access to your application. As you may have noticed, I never mentioned anything about a username or password prompt, that’s the beauty of it all!

Requirements/Prerequisites
There are a few prerequisites that must before you can start using passwordless sign-in:
- Azure AD MFA with push notifications must be allowed as a verification method
- You must have the latest version of the Microsoft Authenticator app installed on your device
- You must have a minimum version of iOS 8.0 or Android 6.0
- The device you’re using for authentication must be registered in Azure Active Directory to an individual user
How do I enable Passwordless Sign-in Authentication?
Now that we’ve discussed what passwordless sign-in is, how it is used, and the prerequisites that must be met, let’s cover how to go about implementing this method within your environment! As we’ve mentioned, there are a few different authentication methods to choose from, but in this case, we’re going to use the passwordless sign-in method. To enable this you’ll need to do the following:
- With a Global Administrator account, navigate to the Azure AD portal.
- Browse to Security > Authentication Methods > Policies
- Under Microsoft Authenticator select from the following options:
- Enable: Yes or No
- Target: All users or Select Users
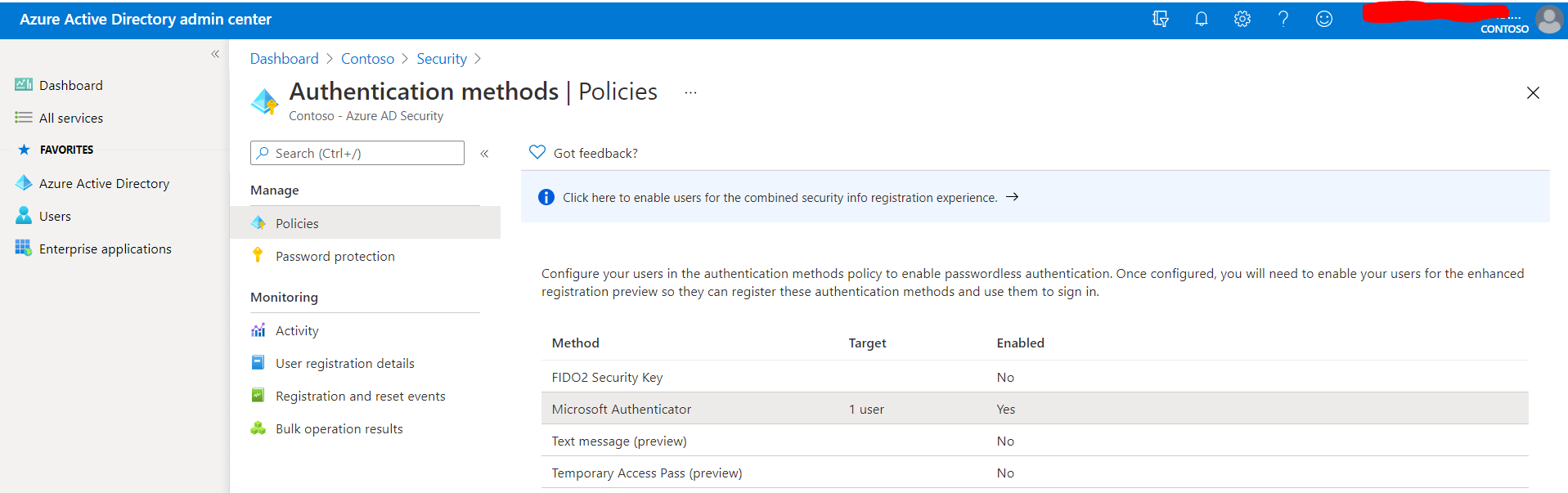
- Any group or user that is targeted will use the passwordless and push notification modes (“Any” mode) by default. If you’d like to change this you will need to do the following:
-
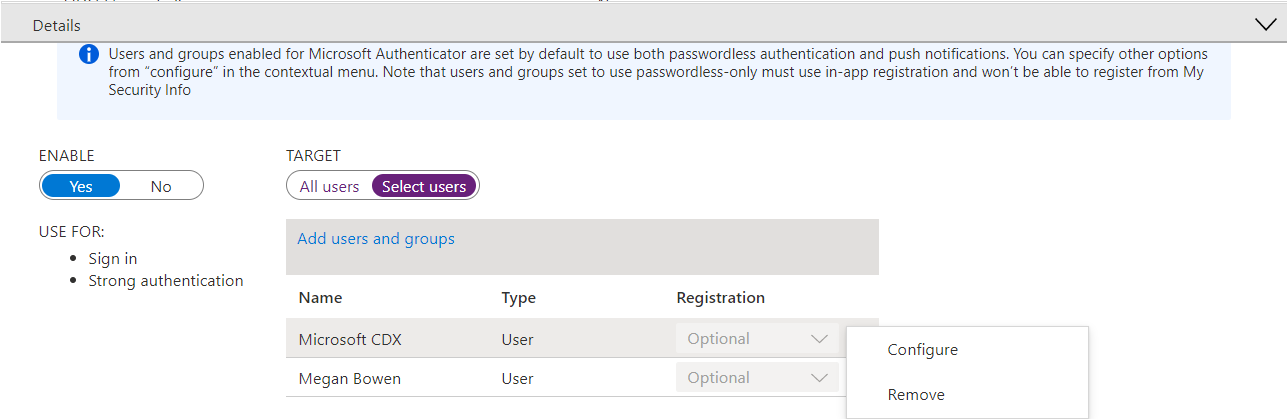
- Expand the Details pane and next to the group name or user name you should see an ellipses (…). Select that and choose Configure.
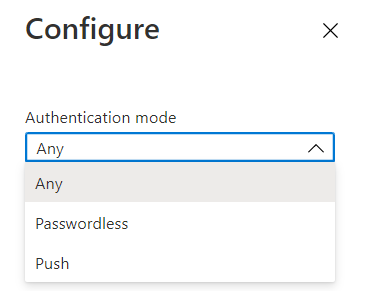
- In the Configure pane, expand the drop-down and choose the authentication mode(s) you want that user or group to use.
- In our case, we’d change this from Any to Passwordless
- Expand the Details pane and next to the group name or user name you should see an ellipses (…). Select that and choose Configure.
-
- Once you’re all done with making these changes select Done and then don’t forget to also select Save.
That’s all it takes! I hope you have found this quick run-through of the passwordless sign-in via Microsoft Authenticator helpful, and I encourage you to start thinking about implementing this method within your organization!
