Datapower has a built-in publish-subscribe mechanism that is robust and flexible for logging. As many transactions flow through many events occur. Some of these events occur because of normal processing and some of the other occurs because of exceptions.
Log Target:
Log target capture messages that are posted by various objects and services that runs on the appliance.
Target type enable additional capabilities that include rotating file, signing, encryption and sending files to remote servers.
To create new Log target
Click Administration
Click Manage Log targets
Click Add to create new Log Target.
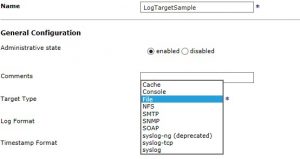
Enter name of the LogTarget.
In type click File.
The drop down list will show many below options.
Console-Writes log entries to the screen when using telnet,SSH or Command Line access through serial port.
Cache-Writes log entries to system memory
Syslog-Forwards log entries using User Datagram Protocol to remote syslog.
Syslog-ng(deprecated)-use Syslog-tcp.
SMTP-Forwards log entries as email to configured remote SMTP servers and email addresses.Before sending the content of the logs can be encrypted and signed.
File-Writes log to file on the appliance.
SNMP-Forwards log entries as SNMP traps to all configured recipients. The processing rate can be limited.
SOAP-Forwards log entries as SOAP messages. The URL can be set. The processing rate can be limited.
Syslog-tcp-Forwards log entries by using TCP to a remote syslog daemon. The local address, remote address, remote port, and syslog facility can be set. A secured connection to the syslog host can be created. The processing rate can be limited.
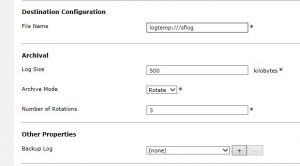
Enter destination file name.
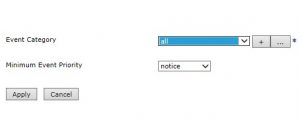
Click Event Subscription.
Click add. Log target must have at least one Event subscription.
Select all from Event Category list.
If needed we can create our own Event category but it should be unique.
Select notice in Minimum Event priority.
Click Apply and Save Configuration.
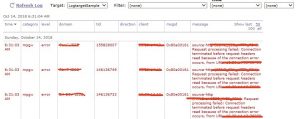
Now the below log target is created.
Now post any valid or invalid request.
Now go to system-log and filter for LogTargetSample.
In addition to event subscriptions, log targets offer the ability to create filters of various kinds. Filters restrict the messages that are captured by the log target. Filters can be any of the following types:
Event filters- Event filters either include only messages with the designated event code within them or exclude messages with the designated event code within them.
Object filters -Object filters include only messages that are published by the selected object class and name. The name can be a wildcard, including all objects of the selected class.
IP address filters- IP address filters include only those messages with the client IP addresses that are included in the filters that are set for this target.
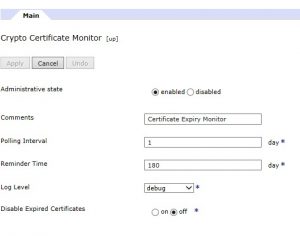
For Monitoring Certificate expiration, we can do below customization to log targets
Datapower appliances come with an embedded function for certificate monitoring, called Crypto Certificate Monitor. This function is available only at the default domain. The certificate monitor object can help to keep you informed about every X.509 certificate expiration date that is installed in the device.
DataPower appliances come with several log categories set and enabled, by default. A useful category for certificate monitoring is the cert-monitor category. We can use this category when setting monitoring for certificate expiration.
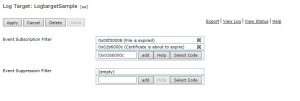
Also we can filter Events as below
Add event filter and select the code that you want to filter.
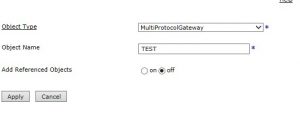
Similarly, we can also do Customization to filter objects as below.
Log Category:
Datapower provides predefined log categories and supports up to 175 custom log categories. A custom log category is limited to a specific domain. Its name must be unique to the appliance.
When you create a log category with the same name in two domains, the appliance places the second log category in the down operational state.
To define custom messages, use the xsl:message extension function. The dp:type attribute of this element indicates the custom log category.
Log Level:
We can change logging level for the system-wide log for the default domain or the domain-specific log in an application domain.
Go to troubleshooting and log level.
Any of these levels can be used.
Setting level to information or debug will affects performance.
Log Action:
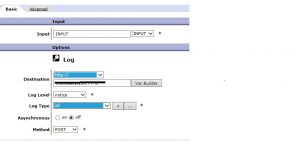
We can use log action inside processing rule.
A log action takes a copy of a particular message payload and sends it to a log destination for auditing purposes.
Select Log action from Advanced in processing rule.
You can find various destinations available.
Select Log Level.
Click done.
Now when request is posted it will be logged into remote server or mq whatever is configured.
Reference
https://www.ibm.com/support/knowledgecenter/SS9H2Y_7.5.0/com.ibm.dp.doc/logtarget_logs.html