Burp Suite is a comprehensive web application security testing tool that provides a range of features to help identify vulnerabilities in web applications. One of its most powerful tools is Sequencer, which allows testers to analyze the randomness and quality of tokens and other random values used in web applications. In this blog, I’ll walk you through the step-by-step process of using Sequencer in Burp Suite:
- Open Burp Suite and navigate to the “Proxy” tab.
- Click on the “Intercept” button to enable intercept mode.
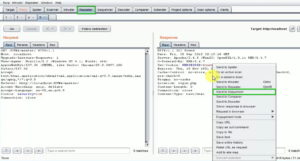
Fig: Intercepted request sending to Sequencer
- Navigate to the website or application you want to test and perform an action that generates an HTTP request.
- Once the request is captured in the “Intercept” tab, right-click on it and select “Send to Sequencer”.
- The Sequencer tab will open, and you will see the captured request.
- In the Sequencer tab, click on the “Options” tab, and select the “Token Location” option.
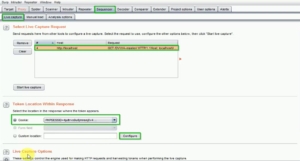
Fig: Configuring Sequencer
- Choose where you want the Sequencer to look for tokens by selecting the appropriate option.
- Click on the “Start Live Capture” button to begin capturing tokens.
- Perform actions in the web application that generate tokens to capture them in real-time.
- Once you’ve captured enough tokens, click on the “Stop Live Capture” button.
- The Sequencer will now analyze the tokens and generate a report on their quality.
- The report includes information such as the number of unique tokens, the entropy of the tokens, and the overall randomness score.
- You can use the report to identify weak points in the web application’s token generation process and take steps to improve it.
- The Sequencer also includes a “Guess” feature that can be used to predict future tokens based on the captured tokens.
- You can use the “Guess” feature to test the strength of the web application’s token generation process against potential attacks.
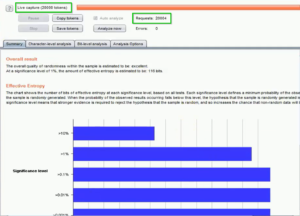
Fig: Sequencer report analysis
- With the insights gained from using the Sequencer tool, you can improve the security of your web applications and protect them against attacks that exploit weak or predictable tokens.
Consider the following guidelines during the testing process:
- Configure Browser Proxy Settings: Ensure that your web browser is configured to use Burp Suite as a proxy. This is crucial for capturing and analyzing the HTTP requests effectively.
- Customizing Token Analysis: Burp Suite allows users to customize the analysis parameters, such as the number of tokens to capture and the analysis technique. Encourage users to explore these options based on the specific requirements of their testing scenario.
- Interpreting Results: Emphasize the importance of carefully reviewing the Sequencer report and understanding its implications. Explain how to interpret the results and prioritize issues based on the severity of the findings.
- Secure Communication: Highlight the need for testing in a controlled environment and obtaining proper authorization before conducting security assessments. Emphasize responsible and ethical use of security testing tools.
Conclusion
Sequencer is a powerful tool that provides valuable insights into the randomness and quality of tokens and other random values used in web applications. By following these simple steps, you can use Sequencer to capture and analyze tokens, generate reports, and identify weak points in the token generation process. This will help you improve the security of your web applications and protect them against potential testing.

