In this day and age, protecting your organization’s sensitive data has started to become exceedingly difficult. Where remote work has become the new norm, you will likely see many end-users using their own unmanaged devices to access corporate information. With this comes the risk of unmanaged devices sending/sharing sensitive information without the ability to control or monitor these types of activity. Luckily, there are ways to control and combat this with the use of MCAS. In today’s blog, I’ll show you how you can block downloading of files with sensitive data to unmanaged devices with the use of session policies in Microsoft Cloud App Security (MCAS). As part two of this blog, we’ll take things a step further and show you how to restrict cut/copy, paste, and print activities in MCAS!
Controlling End-Users using Sensitive Data on Unmanaged Devices
Let’s say we have a user, Megan B. who is working from home on her personal laptop. Megan is working on a file that has several different Social Security Numbers of different employees at her organization. Although we want Megan to have the ability to access this data from her personal device, we do want to restrict her ability to download that file since it contains sensitive information that could be harmful to the organization if downloaded to an unmanaged device and sent/shared elsewhere. This is where our Session Policies come into play within MCAS. With a Session Policy, we will be able to define which types of sensitive information we want to block so that when Megan B. goes to download a file on her personal laptop with a Social Security Number in it, she will be blocked from doing so and an alert will be generated within MCAS. To create the session policy, we’ll do the following:
- Navigate to portal.cloudappsecurity.com
- On the left-hand side, find the Control drop-down and select Policies
- Find Create Policy drop-down and select Session Policy
- On the “Create session policy” page, select the Policy template drop-down and choose the Block download based on real-time content inspection
- Select Apply template
- Find Session Control Type and in the drop-down to select the type of control you want to enable, select Control file download (with inspection).
- Note: You should see several options at your disposal, monitor only, block activities, control file download (with inspection), and control file upload (with inspection). For this use case, we’ll be controlling the file download and inspecting the content.
- Under Activity Source we’ll choose the corresponding filters that we want to match on. For this use case, we’ll want to find all devices that aren’t Intune compliant nor hybrid Azure AD joined. In addition, we’re only going to look at Teams, OneDrive, and SharePoint Online for our apps. Your filter should look something like this:
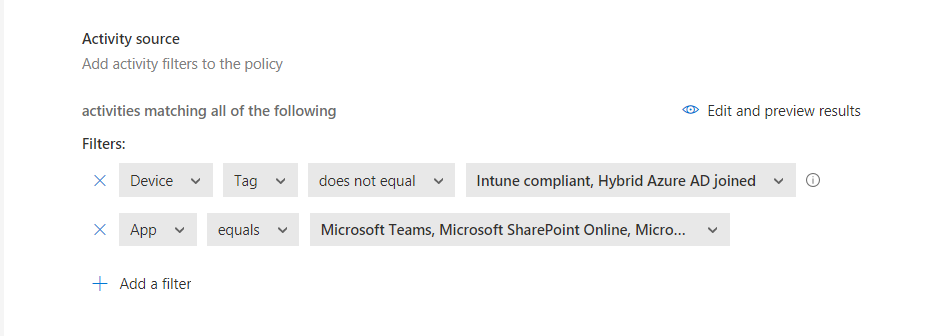
- Now that we have our activity filters defined we’ll specify the inspection method we’d like to use to find any Social Security Numbers present in files. To do this find the Inspection method drop-down and select Data Classification Service.
- Now we’ll need to specify our inspection type, in this scenario we’re looking for SSNs so we’ll choose Sensitive information type.
- You should see a new box asking you to select the sensitive information types you want to search for. In our case, we want Social Security Numbers so we can just search for SSN in the search bar on top and hit enter. For this scenario, we’ll only look for U.S. Social Security Numbers.
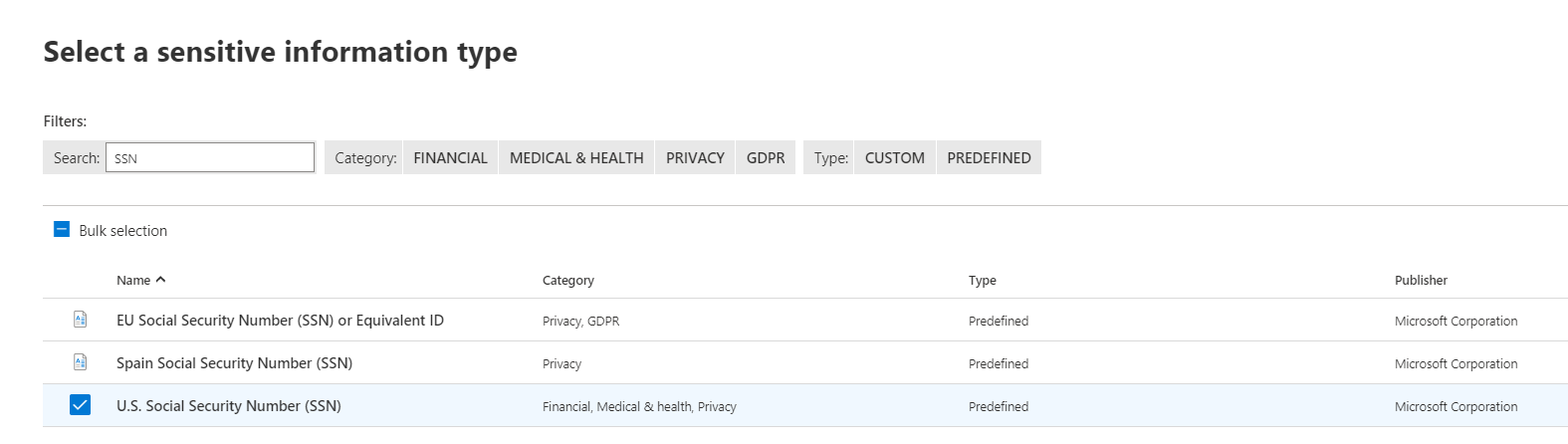
- Select Done once you’ve selected the U.S. Social Security Number (SSN) box.
- Now we get to choose how we want to govern this real-time policy. We can either block the file download or protect the file by applying a classification label to it. Since we want to block this sensitive data we’ll choose the Block option which will block the file download and monitor all activities. Additionally, if we wanted to notify the user by email and/or customize the block message that appears, we can do that here.
- Last but not least, we can choose to create an alert for each matching event with the policy’s severity. Our default daily limit is set to 5, however, this can be increased to as many as 1,000 daily alerts! In addition, we can send the alert as an email and/or text message. We can even send the alerts to Power Automate if you’d like!
- Once you’ve reviewed your policy go ahead and select Create.
Now that the policy has been created, let’s test!
End-user experience
Let’s revisit our scenario. We have Megan B attempting to download a file that contains SSNs from her personal laptop. Since we are now blocking any file that contains a U.S. SSN from being downloaded, we should see this being blocked for Megan since she is attempting to download this file to an unmanaged device. From Megan’s perspective, when navigating to SharePoint Online she immediately sees a screen letting her know that her access to SharePoint Online is being monitored and that access will only be available from a web browser. Once she selects Continue to Microsoft SharePoint Online, she will be proxied through MCAS but from the end-users perspective, everything will look the exact same.

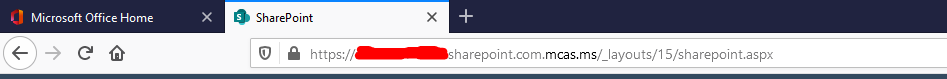
A good way to tell that this has successfully been forced through MCAS is by looking in the address bar once the page has loaded. You should see mcas.ms in the address.
Megan B has now reached the SharePoint site from her personal laptop and proceeds to open the Excel file that contains several different SSNs.
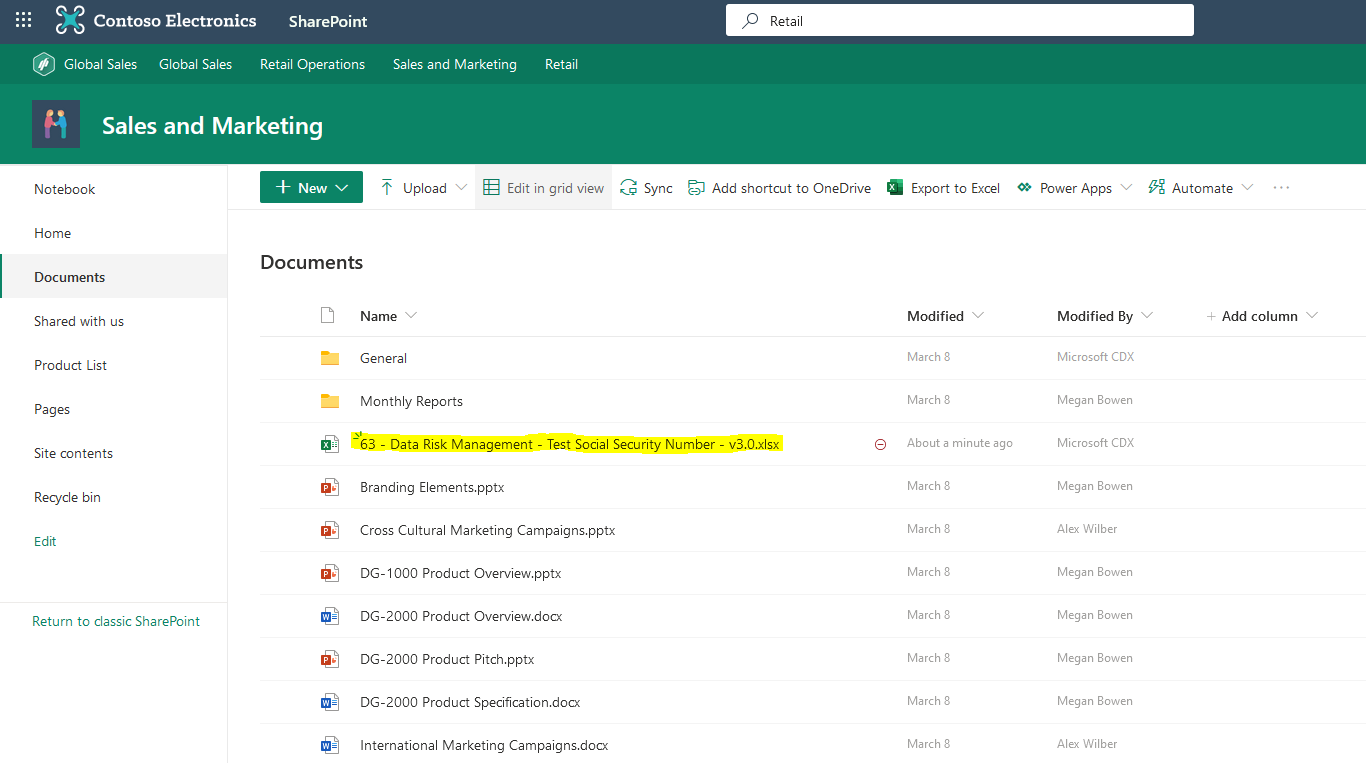
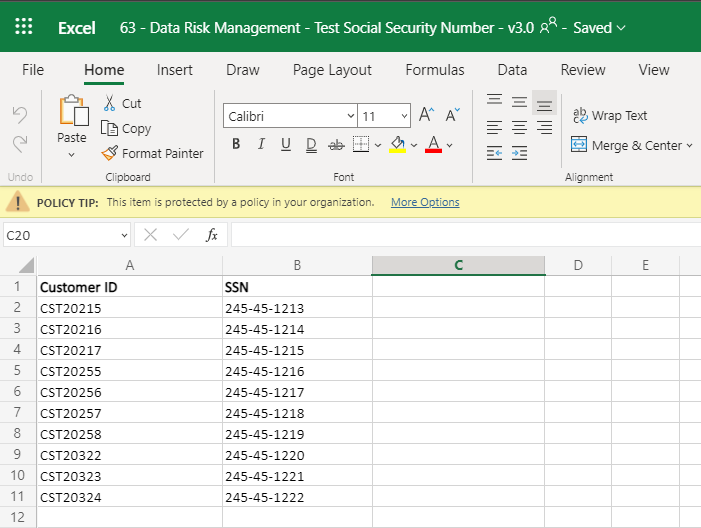
Previously, Megan B. would be able to download this file to her personal device and at that point, you could kiss that sensitive information goodbye as it just left your organization for good. However, with the new Session Policy in place, when Megan B. attempts to download a copy of this file to her personal device she will be blocked from doing this and will receive a pop-up informing her that downloading this file has been blocked due to the organization’s security policy.
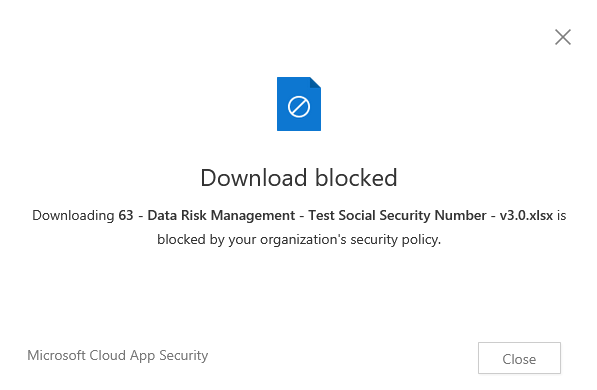
It is as easy as that, and this is just scratching the surface of what MCAS can do to protect your data at rest and in transit! I hope you have found this quick run-through helpful and I encourage you to check back shortly for part two of this blog!

