Welcome back to the last part of our “Four Microsoft 365 network connectivity principles you need to know” blog series! Last time, we discussed the concept of enabling direct connectivity for Microsoft 365 connections
If you haven’t had a chance to check that blog post out yet, I encourage you to check it out here. In this blog, we’ll cover the last principle which involves modernizing security for software as a service (SaaS). Let’s talk about why this concept is so important!
Principle #4: Modernize Security for SaaS
Lately, Microsoft has found that many customers have been struggling with maintaining rich and consistent security protection around their software as a service (SaaS) applications. This can be for many different reasons but often involves the growing impact over the traditional network controls to the user experience. Traditional enterprise networks often enforce network security on Internet traffic by using technologies like proxies, SSL inspection, packet inspection, and data loss prevention systems. Although these technologies serve an important purpose in reducing risk for generic Internet requests, this can also have a negative impact on the performance, scalability, and quality of the end-user experience when these technologies are used on Microsoft 365 traffic. With all that being said, Microsoft recommends that you review your network security and risk reduction methods (specifically for Microsoft 365 bound traffic) and instead start using Microsoft 365 security features to reduce your organization’s reliance on intrusive network security technologies that may be impacting your Microsoft 365 traffic. Furthermore, Microsoft recommends that customers start moving away from the traditional network security inspection capabilities, and instead start to adopt the “Zero Trust” architecture. The Zero Trust architecture relies more on using security dimensions which have been natively built into the SaaS application already. This includes leveraging signals and capabilities on the user, identity, device, workload, and data aspects.
In the diagram below we see two different scenarios. The first one we see is the Network Perimeter Inspection which can still be very effective for things like browsing the Internet or accessing an application on the Internet but as mentioned earlier does have a negative impact on Microsoft 365 traffic. The line below that we have our zero trust architecture which has several different ‘lenses” that combine signals and provide the richest most meaningful security visibility and most optimal security outcomes.
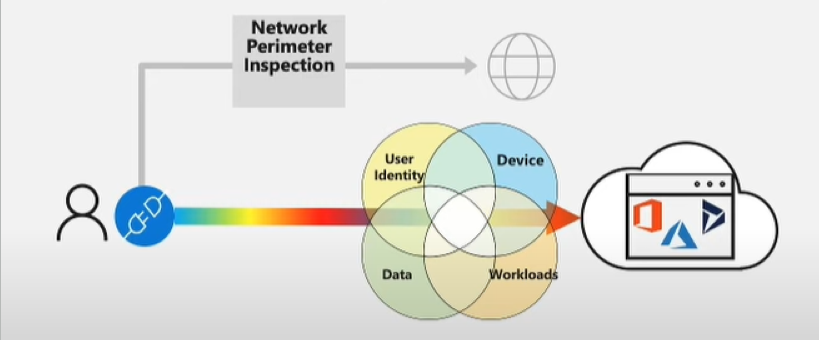
When it comes to accessing our SaaS applications Microsoft recommends the Zero Trust model as this allows us to evaluate signals and achieve the security outcomes that are related to the application itself. With this principle comes the need to identify and differentiate different types of network connections as close to the source/user as possible. Microsoft indicates that this is where the best value in security and user experiences can be achieved when different connections with different performance and security contexts are treated differently. By differentiating network connections closest to the user, this will provide the highest value for the most performance-sensitive apps (i.e. Microsoft 365). Even better for you, many SD-WAN platforms now have this capability and differentiation built-in natively so that you as the customer don’t have to do this manually and can still benefit from these outcomes as part of your SD-WAN adoption. That wraps up our final network connectivity principle! I hope you have found this helpful, and I encourage you to check back soon where I’ll be covering the different network connectivity testing tools at your disposal so you can start testing your network between your users and Microsoft 365!

