Ensuring the security of business-critical servers hosting e-commerce websites is a challenge in itself. And with the internet becoming an increasingly hostile environment, with threats of all kinds lurking around and ready to exploit, one needs to be a step ahead and increase the perimeter of their security.
A bastion host, as the name itself suggests, is that fortified host standing guard as the first line of defense, ensuring that your servers are protected against any intruders.
This post specifically applies to Linux bastion host systems. However, best practices apply to all computer systems.
Background
A common practice in many data centers and IT companies is to allow systems administrators Secure Shell (SSH) access to the servers they are administrating directly from their desktops using generic login credentials generated at the time of server provisioning.
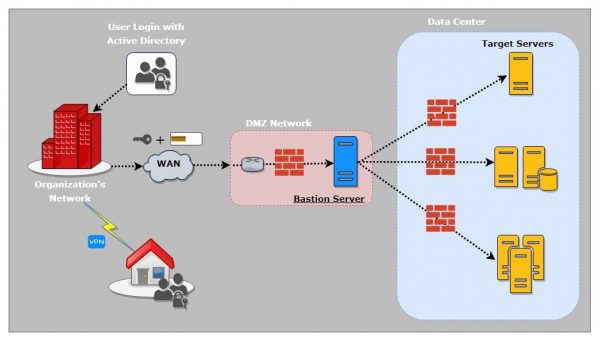
Limiting such unrestricted access through generic users and instead having an individual login for each systems administrator can be regulated through the use of a bastion host, which for this purpose is also called a jumpbox or jump server.
A bastion host is a secure server that all system admins first connect to before launching any administrative task or use as an origination point to connect to other servers. The use of an intermediate bastion host increases security and ease of management of your Linux production server.
Another important reason to consider setting up a bastion host is to comply with Payment Card Industry Data Security Standard (PCI DSS) requirements and security assessment procedures.
Implementation Highlights & Protective Measures
In order to effectively protect your system against attacks, keep these general principles in mind:
- Enhanced Security: Additional security measures can be taken such as turning off unwanted services and implementing the latest available security patches.
- Network & Host-Restricted: It is very important that the bastion host is not allowed to connect to any place. The perimeter firewall must be configured to block all connection attempts on the network or open internet from the bastion host.
- Security settings to avoid Denial of Service (DoS), spoofing, and flood attacks.
- Creating an individual login credential for each systems administrator.
- SSH public-key authentication with a strong passphrase-protected key.
Access Procedure
- System admins wanting to access the remote servers from the office initially have to establish a connection with the bastion server and authenticate using their given key. In the process, they will be prompted to enter the passphrase of their RSA key and then the user-account password.
- System admins who need to access the remote servers from their homes or any other location need to connect to their secure office VPN first.
- Once authenticated and logged into the bastion host, simply type the SSH command and give the name of the remote server you wish to access. If you don’t remember the server names (which is obviously a difficult job), simply start typing the first letter of the project to which the server is related and then hit the Tab key to show predictions.
- The smart predictions are fetched from the database of Advanced SSH config tool.
- After you type the complete and the correct alias name as predicted, hit Enter to initiate the SSH connection to that remote server. You will now be authenticated with your pre-configured key and, upon success, will be prompted to enter the passphrase.
- Once the passphrase is verified, you will be logged in to the remote server.
With this configuration in place, we (the Perficient Digital Hosting Team) maintain a policy that addresses information security and keeps our customers’ valuable information safe and secure, thus ensuring its confidentiality, integrity, and availability.
