OBIEE 12c by default uses WebLogic internal user directory for security purposes. This is effective only when the number of the users is very limited and is not expected to grow much over the years. But, in a real world business scenario, almost all implementations require configuring a more robust way to implement authentication and authorization to allow additional users access to OBIEE without changing a lot of things from the OBIEE end.
LDAP is one of the very effective ways to enable users to login with common IDs – that they use across a company network allowing access to OBIEE via the same central active directory as applications. It’s best to implement LDAP active directory in addition to the internal WebLogic user directory so that WebLogic IDs and other administrative IDs remain unaffected due to this change and also if required the default active directory can also be used if required separate to the LDAP directory. It’s best to create a new realm for the new LDAP authentication allowing easy toggling from one realm to another as and when required.
Pre-Requisites
- Oracle Business Intelligence Enterprise Edition 12c g must be installed and running.
- LDAP server to be used as the identity store that contains users must already be configured.
Security Settings
This document captures security settings in OBIEE 12c environment.
Authentication: Active Directory Authentication – LDAP
Weblogic Console Modifications
Login in to WelbLogic Manager using weblogic account. Click on bi -> Security Realms in left panel.
http://machine.domain.com:9500/console
Click on ‘myrealm’. Configuration -> General tab would open.
Click on “Providers” tab. Here you will see following three default ‘Authentication Providers’.
Click on “DefaultAuthenticator” provider. Click on Lock and Edit -> Change the Control Flag from Required to Sufficient and then Click Save.
Once the settings updated successfully message is displayed click on Activate Changes.
The ‘All Changes have been Activated. However 2 items must be restarted for the changes to take effect‘ message would be displayed. Wait for the entire process to complete before restarting OBIEE server.
First LDAP Authentication Provider needs to be set up. For that, go to Providers Tab -> Lock and Edit and Click on New.
Name it as “Edir_LDAP”. Select the type as IPlanetAuthenticator. Click OK.
Once done open the Edir_LDAP provider again and change the control flag to Sufficient. Save it.
Enter the following details in the provider specific tab.
Host: hostname.domain.com
Port: 123
Principal: uid=user1,ou=system,ou=users,dc=domain,dc=com
Credential: (Enter the password for the Principal Account listed above)
Confirm Credential: Re-enter the same
User Base DN: dc=domain,dc=com
All Users Filter: (&(uid=*)(objectclass=person))
User From Name Filter: (&(uid=%u)(objectclass=person))
User Search Scope: Subtree
User Name Attribute: uid
User Object Class: person
Group Base DN: dc=statestreet,dc=com
Group From Name Filter: (|(&(cn=%g)(objectclass=groupofUniqueNames))(&(cn=%g)(objectclass=groupOfURLs)))
Group Search Scope: Subtree
Group Membership Searching: unlimited
Max Group Membership Search Level: 0
Group from User Filter for Memberuid: (&(memberuid=%M)(objectclass=groupofuniquenames))
Static Group Name Attribute: cn
Static Group Object Class: groupofuniquenames
Static Member DN Attribute: uniquemember
Static Group DNs from Member DN Filter: (&(uniquemember=%M)(objectclass=groupofuniquenames))
Dynamic Group Name Attribute: cn
Dynamic Group Object Class: groupofURLs
Dynamic Member URL Attribute: memberURL
Connection Pool Size: 6
Connect Timeout: 0
Connection Retry Limit: 1
Parallel Connect Delay: 0
Results Time Limit: 0
Follow Referrals: check
Cache Enabled: check
Cache Size: 32
Cache TTL: 60
Cache Statistics Enabled: check
Guid Attribute: nsuniqueid
Identity Domain: Blank
No need to modify the Performance tab. Keep it default. Click Save and click Activate Changes. The following message in green would be displayed.
Restart the OBIEE servers after running the ./stop.sh and ./start.sh scripts located at $Oracle_Home/user_projects/domains/bi/bitools/bin.
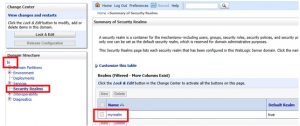
Once it is started to validate if LDAP authentication is correctly setup, search for a particular user id by going back to weblogic console -> ‘mysecurityrealm’ >> Users and Groups >> Users >> customize this table.
Enter a user id under ‘Criteria’ and hit enter. If LDAP authentication is setup right, you will be able to pull that userid from server:
Enterprise Manager Configuration Changes
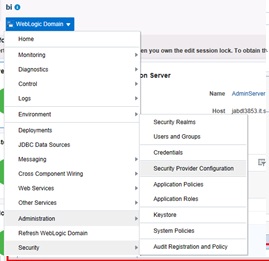
The next step is to configure OBIEE to see users from your new LDAP provider in addition to the weblogic internal directory users. To do this you need to login to the Enterprise Manager with your admin user account
Once logged in, from the Weblogic Domain drop-down menu select Security -> Security Provider Configuration
From the Security Provider Configuration screen expand ‘Security Store Provider’, then expand Identity Store Provider and finally click ‘Configure’
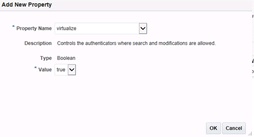
In this screen we need to add a new Custom Property. Click the +Add button.
Then enter a property name of ‘virtualize’ and a value of ‘true’. Then click OK again to save:
Click OK again.
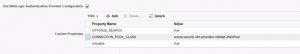
Similarly add one more property of OPTIMIZE_SEARCH = true.
Restart the OBIEE servers after running the ./stop.sh and ./start.sh scripts located at $Oracle_Home/user_projects/domains/bi/bitools/bin.
Object Level Security: Storing Groups in Database
We will look at settings for connecting the system to an external set of database tables that contain the group membership for users authenticated through LDAP.
Pre-Requisites
- A suitable database schema containing at least one table with the required groups in it, and a mapping table which maps those groups to the names of users authenticated by LDAP must be running and accessible from the WebLogic Server on which Oracle BI EE is running. There is a job which extract User responsibilities which match User Group data from EBS and loads into Data warehouse. Let’s assume that the table name is STT_AUTHORIZATION_GROUPS..
- Copy the “bi-sql-group-provider.jar” file from the location $ORACLE_HOME/bi/plugins/security to $ORACLE_HOME/wlserver/server/lib/mbeantypes. Stop and Start the entire OBIEE server using the scripts present at $Oracle_Home/user_projects/domains/bi/bitools/bin.
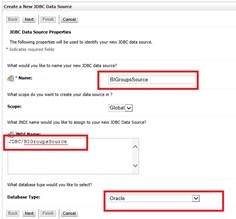
Configure the Data Source
Login into WebLogic Console and click on ‘Services’ >> ‘Data Sources’:
Lock and Edit.
Click New -> generic data source.
Enter the details marked in Red and click Next.
Select the following Driver and click Next.
Click Next.
Enter the following details and click Next.
Check all the details and Test Configuration. It should succeed. Click Next.
Select the target and click Finish.
The datasource will be created.
Next create a BISQLGroupProvider against this JDBC data source.
Configuring the BISQLGroupProvider SQL Authenticator
Go back to Services >> Security Realms >> mysecurityrealms >> Providers. Click New.
Put the name as BIGroups and Type BISQLGroupProvider. Click OK.
Notice ‘control Flag’ under configuration >> common tab for ‘BIGroups’. It should be Optional.
Click on ‘Provider Specific’ tab. This authentication provider is using ‘BIGroupsSource’ as JDBC data source. We will talk about configuring that data source in subsequent screenshots. Please follow pre-requisites for setting ‘BIGroupsSource’ before adding it as data source. Steps are listed in next section.
Data Source JNDIName:JDBC/BIGroupsSource
Group Membership Searching: Unlimited
Max Group Membership Search Level: 0
SQLList Groups:SELECT WEB_GROUP FROM TABLE_NAME WHERE WEB_GROUP LIKE ?
SQLGroup Exists: SELECT WEB_GROUP FROM TABLE_NAME WHERE WEB_GROUP = ?
SQLIs Member: SELECT USERID FROM TABLE_NAME WHERE WEB_GROUP = ? and substr(UPPER(USERID), 2, 6) = substr(UPPER(?), 2, 6)
SQLList Member Groups: SELECT WEB_GROUP FROM TABLE_NAME WHERE SUBSTR (UPPER (USERID), 2, 6) = SUBSTR (UPPER (?), 2, 6)
Descriptions Supported: check
SQLGet Group Description: SELECT WEB_GROUP FROM TABLE_NAME WHERE WEB_GROUP = ?
Save. Go back to Providers List and reorder as below. Activate Changes.
Create custom Application Roles and assign them to Groups using EM
We have three custom groups GPS_AUTHOR, GPS_ADMIN and GPS_CONSUMER. Now we need to assign them application roles.
Login into Oracle Enterprise Manager.
Expand Weblogic Domain tree on left hand side.
Select Security -> Application Roles.
By default we have three application roles that come with the installation and one superuser: weblogic.
Here create three custom application roles ‘GPS_ADMIN’, ‘GPS_AUTHOR’ and ‘GPS_CONSUMER’ and assign them to respective groups.
Screenshots below show how each custom GPS role is assigned to a GPS group:
GPS_ADMIN role should have same rights has BIServiceAdministrator and GPS_AUTHOR should have BIContentAuthor rights. So assign GPS_ADMIN, GPS_AUTHOR role under box BIServiceAdministrator, BIContentAuthor roles respectively.
Restart the entire OBIEE server.
Validate the Custom Application Roles from Analytics
Login into analytics using one of the userid authenticated against LDAP and navigate to My Account >> Roles and Catalog Groups. You should see your custom application role here.
Assign permissions to Application Roles using Analytics
Login into analytics using weblogic account and navigate to Administration >> Security >> Manage Privileges.
Here you can assign permissions to individual components to each custom Application Role. It is a self-explanatory process.































Hi Avik,
we’ve configurend both LDAP and BISQLProvider on our enviroment.
We see DB groups in EM and we can associate them to Application Roles.
But if we log-in to Analytics with a LDAP user (which are related to a DB group in our SQL tables), under My Account –> Roles and Catalog Groups we didn’t see the Application Role.
Any Suggestion?
Thanks in advance.
Francesco
Hi Francesco,
Thanks for following my blog. So if I understand correctly the LDAP authentication is working properly since you can login to the BI portal with LDAP credentials.
Can you please do the following to test it a bit more thoroughly:
“validate if LDAP authentication is correctly setup, search for a particular user id by going back to weblogic console -> ‘mysecurityrealm’ >> Users and Groups >> Users >> customize this table. Enter a user id under ‘Criteria’ and hit enter. If LDAP authentication is setup right, you will be able to pull that userid from server”
If this is fine, then make sure you HAVE TAGGED the newly created application roles (with identical names) to the groups being retrieved from database. Make sure you have followed everything precisely mentioned under the section: “Object Level Security: Storing Groups in Database”.
Hi Avik,
thanks for your reply.
Yes we have configured correctly our LDAP because users can already access to analytics.
The problem is to assign users to Application Roles in the SQL Database Tables.
We tried to create the application roles with the same name of the groups (at database level) but nothing seems to happen.
We’ve seen, with a SQL profiler, that a query is generated that controls that the connected user are present in our SQL tables. But again if we go to My Account –> Roles and Catalog Groups we didn’t see the Application Role we didn’t see the Application Roles assigned.
We think (but we are not sure) that a problem could be with the configuration of the bi_sql_groups_adapter_template.xml file.
In the section “Object Level Security: Storing Groups in Database” of your post we followed everything, also with the oracle documentation: JBDC datasource are working correctly, provider flags are configured correctly.
Any suggestions?
Thanks
Francesco
Its strange because I have done this process following the identical steps and have never faced such problems. I am thinking doing the same in a fresh new environment just to make sure its not or is a problem with the environment or configuration files.
Hi Avik,
just a question: we’ve see that you’ve not mentioned the bi_sql_groups_adapter_template.xml file in your guide, did you modify it or not?
Thanks
Yes, that’s because no changes were made to this file during our set up.
HI Avik,
This is a very detailed and well explained blog. Thank you very much for it. But, i am having issue with the screenshots you provided. They are very small and i cant read them. Is it possible for you to upload better resolution screenshots?
Hi Avik,
I am troubleshooting an issue in OBIEE and I came across this post. I have Windows AD authentication set up in all my environments. All but Prod is using Kerberos SSO. The Prod environment still requires users to log on with LAN ID and password. That will change soon. One user is reporting an issue that they cannot log in with their credentials. They should be getting BIConsumer role through autheticated-user and they are a member of the group that has been added to web.xml in analytics.ear. I’ve restarted the environment, I’ve had the user clear their cache. I can see the user ID in myrealm in AdminConsole. Any advice on where to go from here? Other users have no issue, including myself- and I am not an Admin in the application.
Thanks,
Alan
hi,
we needed a step by step guide for configure RDBMS authendication as SUFFICIENT along with default,
Have in environment
1 – Oracle DB server 19c
2- Oracle Analytics Server 7.6
Help please.