As a security professional, I spend a considerable amount of time building awareness around good password hygiene, and I am starting to see forward progress in efforts like moving users away from short passwords to longer passphrases. But even as we are moving towards better password selection, most people don’t know that their old passwords can still pose a threat, even after they’re no longer used. In this post I’ll give you a detailed walk-through of a phishing attack that someone used against me – an attack that used one of my old passwords to try to throw me off balance, building the sense of urgency needed to fool me into falling for a scam. I’ll also determine how successful this phishing campaign has been for the scammer.
The Attack
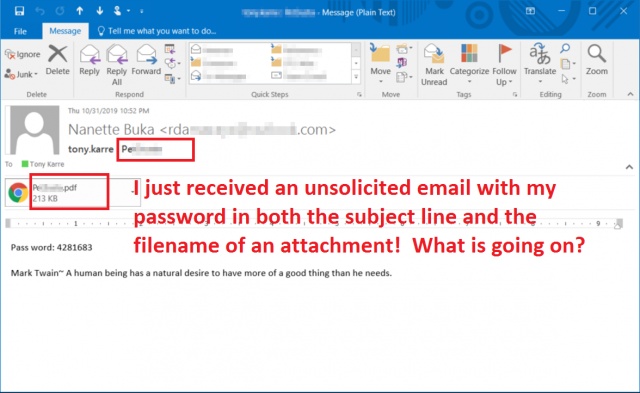
Late in the evening on Halloween (nice!) an email to one of my accounts caught my eye. The subject line of the email contained a string of characters that I recognized as my actual password! When I opened the email, I also saw a PDF attachment with the same password embedded in the filename! Nothing generates a quick jolt of adrenaline more than seeing your own clear-text password emailed to you by someone you don’t know.
Time to do some critical thinking. Yes, that was my password, but it was also an old password – I recognized it as one that I’ve long since changed. Since I don’t re-use passwords across my accounts (and neither should you, by the way), I knew which account the password had come from. To help you understand what is happening here, let’s start with a little back-story.
Some Back-Story
Everyone is clearly aware that a multitude of big websites have been breached over the years, but that is just an abstraction for most people – you may know that a site has been “breached”, but what does that really mean? What data has been stolen?
Many times, a “breach” means that personal information registered with an account has been stolen, and that often includes password information, whether it’s the actual passwords themselves, or password “hashes” that can be cracked over time. In many cases the data thieves will stash the stolen data, including your passwords, on an unprotected website or online database. These are called password dumps. You can read a good discussion of password dumps in this CSO Online article.
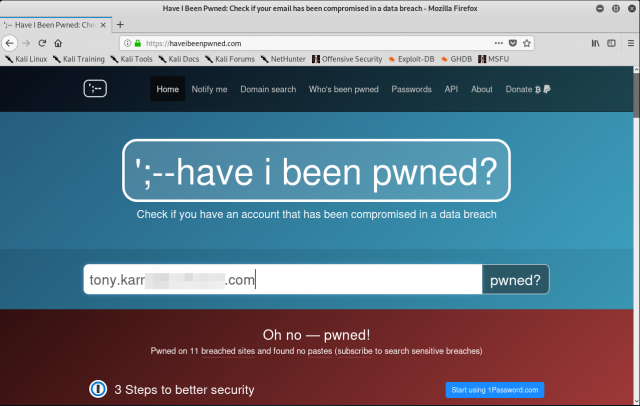
Password dumps happen often enough that security consultants have collected these dumps and created password checker tools around them. One such tool is “have i been pwned” by Troy Hunt. With this tool, you can check to see if your username or email address have been found in a password dump somewhere. Let’s check it out.
Yep, according to the haveibeenpwned site, accounts associated with my email address have been “pwned” several times in various website breaches. In fact, I’ve been pwned eleven times. Remember, though, that we all often reuse the same email address for numerous accounts. So from which account was my password stolen? This site doesn’t directly tell you, but I have a pretty good idea based on the password in the email. Let’s scroll down to see if we can find it in the list.
There it is – LinkedIn is the culprit. No worries for me though – LinkedIn has long since fixed their website, I’ve long since changed my password, and I’ve also long since added two-factor authentication to my account (you should too).
So back to our attack – at this point I’m feeling pretty confident that this is a personalized phishing attack that is using my old password to scare me into being vulnerable for the social engineering part of the phish. Just think about it – if you still used that same password for one or more of your other accounts, your adrenaline would still be pumping right now, am I right? Let’s take a closer look at the attack.
Am I Getting Phished?
All phishing awareness training focuses on a list of red flags to look for as you open and read new emails. But unlike generic awareness training, I’ve got an actual phishing email that we can pick apart and analyze. Let’s take a look at this email to see if we can identify any of those red flags.
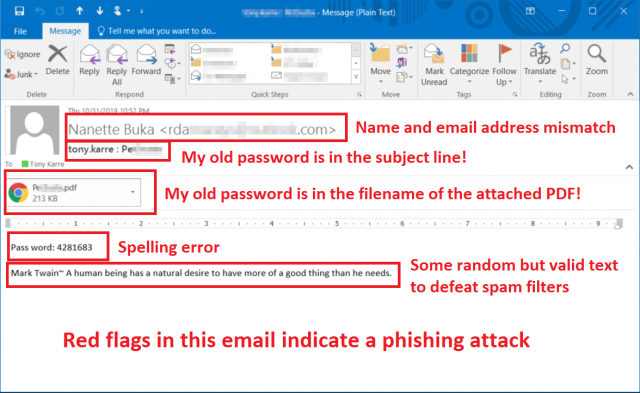
Looking at the email, I can see a number of red flags:
- The descriptive name portion of the email “From” address, “Nanette Buka”, does not match the actual email address seen in the “From” field of the email. While this might not be completely unusual for a personal email, it is rare in business contexts. For instance, if your CFO’s name is “John Smithson”, then I would expect to see “john.smithson @ mycompany.com” in the From field, not “rdaxxxyyzz @ unrelated.fakesite.com”.
- My old but actual password is in the subject line, along with a potentially real username. That’s a scary red flag right there. But also note that the subject line isn’t really meaningful or contextually related to anything I might be doing or know about. As an aside, always make the subject line actually reflect the topic of the email when you send email. Don’t use short ambiguous phrases like “followup” or “invoice attached”. Treat the subject line like a very short tweet – make it meaningful.
- There is an obvious spelling error (“Pass word”) in a prominently featured word, and “password” is almost never spelled incorrectly in a real email.
- There is a quote from Mark Twain in the body of the email. There’s nothing wrong with that quote from an English language perspective, but it’s completely out of context here. My guess is that it is intended to help the email defeat spam and other protective filters.
- Finally there is an attachment that is designed to social-engineer me into opening it. It’s a PDF, it’s not discussed in the body of the email, and the filename has my password embedded in it, for goodness sakes!
So far this really looks like a phishing email. However, it’s missing the one thing critical to a typical phish – an urgent call to action. An urgent call to action is a message or statement in which the author wants you to do something, but there’s not much time to do it, and something bad will happen to you if you don’t do it quickly.
However, the email does have that PDF attachment, and we haven’t explored it yet. My password is in the filename, I’ve been social-engineered, and I really really really want to open it. Is this a good idea?
Is This Malware?
It’s never a good idea to open an untrusted PDF file. Why exactly?
By design, the PDF file format is intended to support interactive behavior. Besides the images and text that you normally see, the internal structures of a PDF can also include javascript that can be executed when triggered by various actions defined by the author. In my email’s file attachment, it’s certainly possible that the file contains javascript that will run after I open and browse the file, and the javascript might contain malware. For this reason, I definitely don’t want to open the file in the normal fashion – I need to analyze it in some other manner.
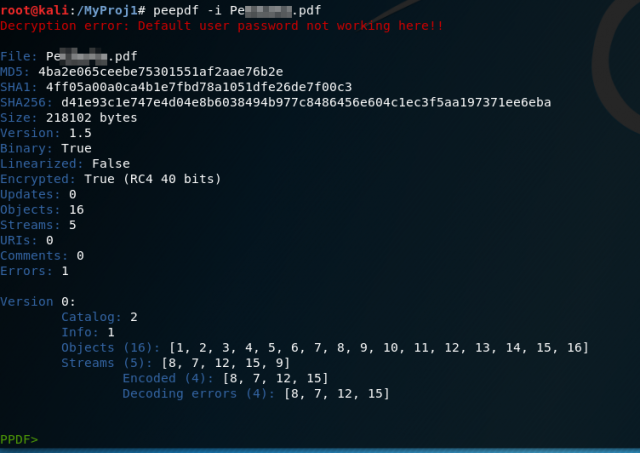
Let’s use the linux peepdf utility to safely examine the internals of the PDF file. I’ll run the peepdf utility in interactive mode so I can browse around the insides of the file.
When I first open the file with the peepdf utility, it gives me an error message indicating that the content within the PDF is encrypted, and the default password used by the utility does not work with my file. Encryption was probably used by the author to keep spam filters and file antivirus from catching and blocking the file. No worries, though, this is probably why the email contains a “Pass word”!
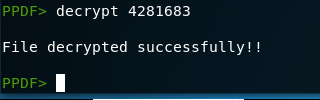
Since we are still in the peepdf utility, let’s use the decrypt command with the password provided in the email body.
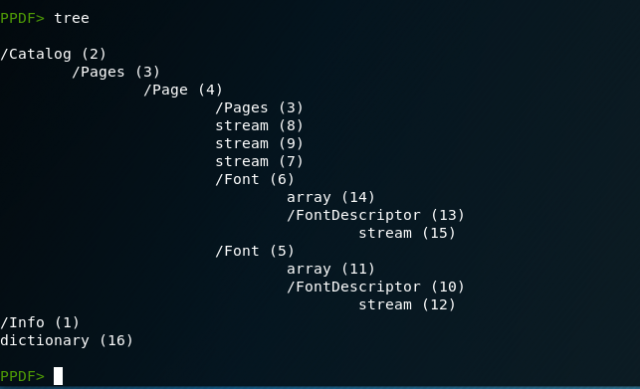
Good – now we can easily browse the PDF data structures to see what is there. Let’s use the tree command to list the “tree” of content data structures.
The tree command shows us that there are five different content streams. Streams 12 and 15 contain font packages, and streams 8, 9, and 7 are page-level content streams that need further examination. Let’s take a look at each of those three streams.
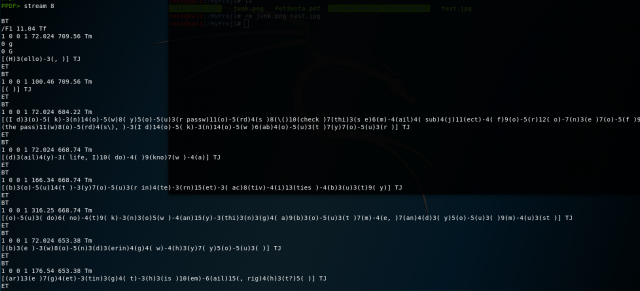
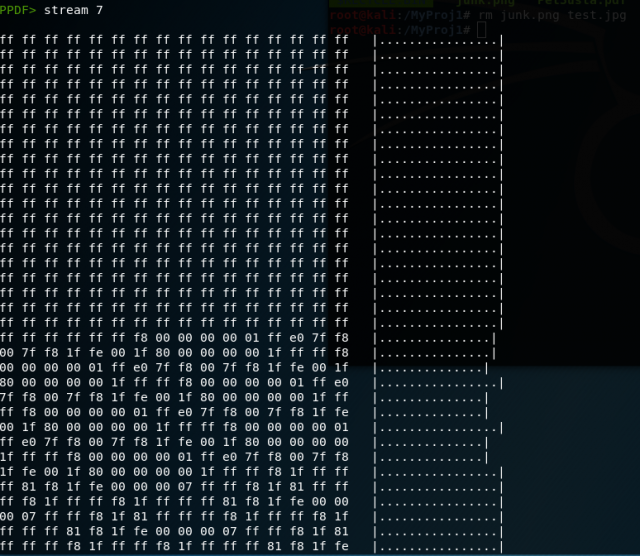
The “stream” command dumps the interpreted content for the stream number you wish to examine. As seen above, stream 8 contains numerous blocks of postscript command streams that describe how encoded blocks of text should be rendered. These postscript commands will be rendered as readable text on the page by your PDF reader application, so this indicates that our PDF will have sections of text for us to read. Let’s keep going and take a look at stream 9.
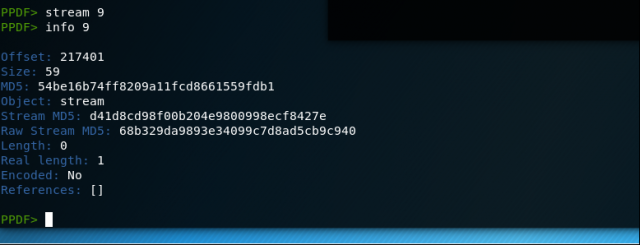
Stream 9 appears to be an empty stream – the stream length is zero. Let’s look at our final stream.
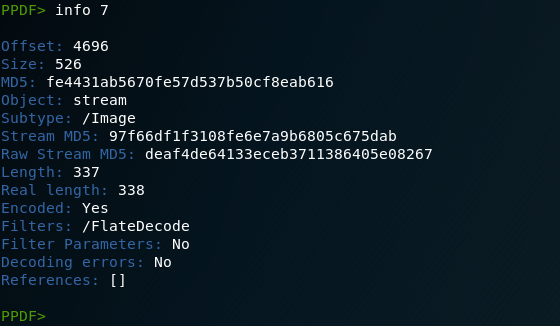
Stream 7 contains some kind of binary data, but we can’t be sure what the stream contains without looking at additional metadata. Let’s use the “info” command to help us figure that out. The info command looks at the descriptive object-level metadata for the stream object, so we’ll use this command to dump the metadata for stream 7.
The output of the info command tells us that stream 7 contains an image. Let’s therefore use the “object” command to dump additional descriptive information about the image.
According to the output of the object command, the image is a 200×200 non-interpolated gray-scale image with one bit per pixel. In other words, a very simple 200×200 black and white image. Let’s use another utility – pdfimages – to extract it.
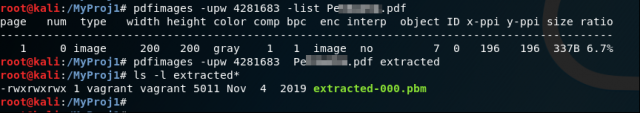
I’ll start with the pdfimages “list” option to generate a list of all the images it can find in the PDF file. I’ll also use the “upw” option to provide the user password needed to decrypt the file. From our earlier work with the peepdf utility, I’m only expecting to see the one single image that we saw in stream 7.
Sure enough, the pdfimages “list” option confirmed that we have a single 200×200 image, and it was found in object 7. I immediately reran the pdfimages utility a second time without the “list” option to extract the image. It turns out that the image is a PBM-type image, which is a platform-independent rasterized image format.
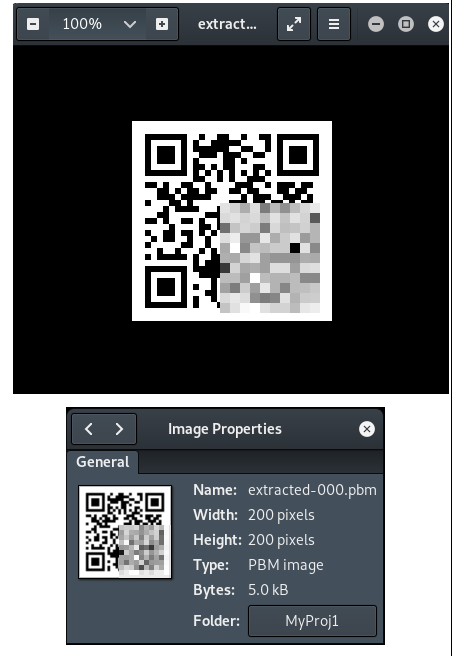
Now that I have the extracted image in a separate image file, it is safe to open it in an image viewer to see what it is (hopefully it’s “safe for work”).
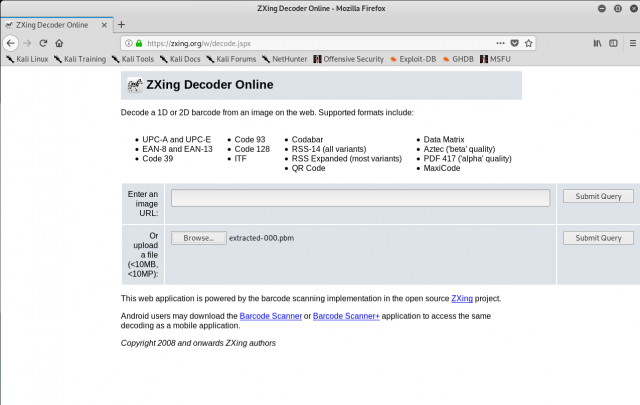
Aha! The image is a standard QR code. Yes, I’m curious about the data contained by the QR code, but there’s no way I’m going to open it with my phone camera to “see where it goes”. The safe way to analyze QR codes is to use a local or online utility to decode the QR code without any other automatic action. In this case, I’m going to upload the QR code image file to the ZXing online decoder to see what it contains.
After uploading the image file, the ZXing online decoder returns the following results:
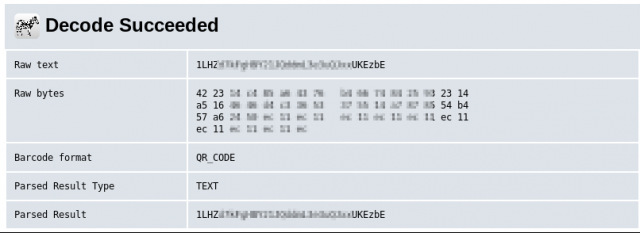
So the data in the QR code is not a URL for a website – it’s a simple string of alphanumeric text.
So what do we know so far?
- The PDF contains text and one non-URL QR code
- The PDF does not contain any interactive elements, such as javascript that might contain malware with triggers and actions to run it
This PDF should be safe to view. I’m going to do this in my virtual machine to avoid any surprises. Here is a screenshot of the rendered PDF:
So now we have our phishing urgent call to action – If I don’t send $1,000 in bitcoin to the provided bitcoin address, then something bad will happen to me. None of the things claimed by the PDF are really true, of course, so I can safely ignore and delete the PDF.
Now normally we might sit here and wonder how intelligent people could ever fall for this type of scam – it’s just too outrageous, right? Well, it turns out that people can and really do fall for this.
Bitcoin and the Blockchain
The “blockchain” is a software implementation of an accounting ledger. A blockchain has these rough characteristics according to the US Department of Homeland Security:
- The ledger is transparent and communally verifiable within an open and shared database
- Each ledger entry (think deposits, withdrawals, etc.) forms a new block in the ledger
- As a shared, synchronized and geographically disbursed database, with no centralized data storage, the system is designed to remove the “single point of failure” risk (including technical malfunction and malicious alteration) that is present in many other systems
- The historical transactions of a specific unit of currency (or data) from its introduction into the system until a specific date, that can be done and verified by multiple independent users
- The blocks form an unbroken “chain” that acts as a visible digital paper trail
Bitcoin, like most virtual currencies, uses a blockchain to maintain the accounting for the bitcoins themselves, and because of the open, visible, and transparent nature of the bitcoin blockchain, anyone can see the transaction history for any bitcoin address!
Let’s take advantage of this and look at the scammer’s bitcoin account using an online lookup tool. If anyone has fallen for this scam, we should see the corresponding bitcoin deposits in the ledger.
Was This Phishing Campaign Successful?
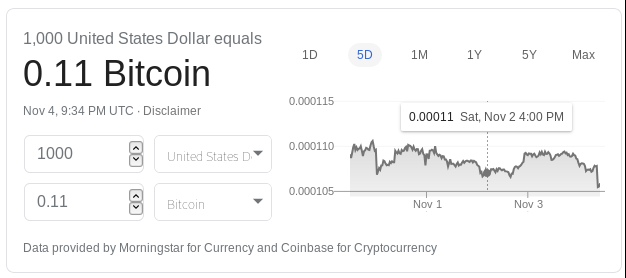
Start by understanding what the size of each phishing transaction should be in this campaign. At the time I did this research, the Google currency calculator found that $1,000 US was approximately equal to 0.11 bitcoin. Anybody falling for the scam would be making deposits of approximately 0.11 bitcoin.
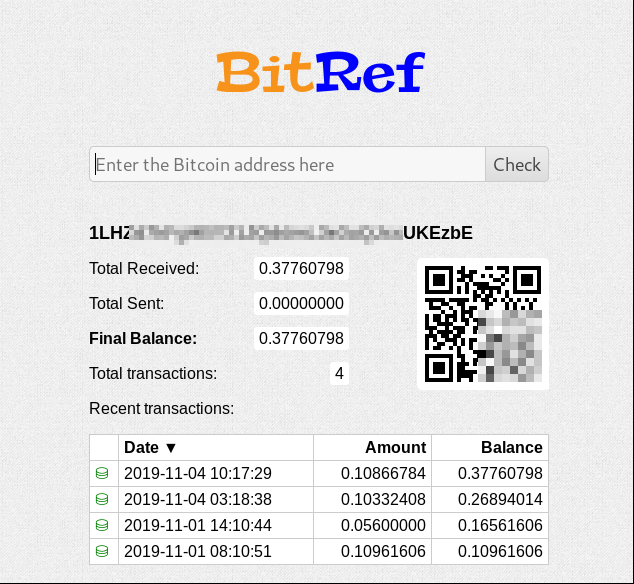
The transactions in any bitcoin account are publicly visible, and there are several websites with online tools that can be used to display them. Let’s use the BitRef.com site to view the transactions for our scammer’s account.
There are four deposits to the account. Three of the deposits are in the neighborhood of 0.11 bitcoin, so it looks like three unfortunate souls fell victim to the scam. There is a fourth deposit of about half of the required 0.11 bitcoin, so perhaps a fourth individual was scammed, and that person has their fingers crossed hoping that $500 US will be enough.
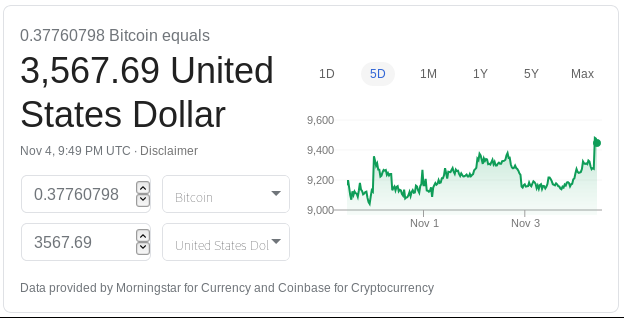
All told, the account balance stands at 0.37760798 bitcoin. Let’s convert that back to US Dollars to see how much money the scammer has earned in their phishing campaign.
Our scammer has earned about $3,566 through this phishing campaign as of November 4. Checking again on November 10, no additional transactions had been recorded, so the number of bitcoin in the account was still the same. The value of bitcoin relative to the US Dollar decreased slightly over those few days, so the value of the bitcoin in the account had fallen to $3,427.
How To Reduce Your Own Risk
This phishing attack was a good reminder of the complex threat environment that the internet poses, and there is no single silver bullet that can keep you safe. Here are some ways to stay away from trouble:
- Don’t ever reuse passwords. Make sure that you use a unique password for each and every account that requires one. If you don’t, then a breach on “website A” can make your password available to criminals who will give your password a try on other accounts. For example, if you reuse a particular password in an online store that is subsequently breached, a criminal can try that same password on your online bank account, work account, ecommerce account, etc. Kiss your money goodbye if you’ve reused your password there.
- Ditch your short but random password for a long passphrase of four or more words. Short passwords, say 12 characters or less, can be cracked fairly quickly, even if they are just strings of nonintelligible random characters. Passwords that are long, say 20 characters or more, are way harder to crack.
- In support of the first two points above, use an app called a “password safe“. You let the application handle all of your passwords, so all you need to remember is the password to the safe itself. The passwords live in an encrypted datastore that can be synced across all of your devices.
- Use two-factor authentication (2FA) for every web account that offers it.
- Pay attention to your company’s mandated phishing awareness training! If you get one of these emails, resist the urge to open the attachments and notify your IT help desk. Don’t worry – they will appreciate the fact that you are paying attention.
- If you get an email from your CEO, CFO, or other person in management, and that person is asking you to transfer large sums of money, change account information, or take some other business action that has financial consequences, please confirm that request with a personal phone call before doing anything. And remember, in real life your CEO is probably never going to ask you to buy a bunch of gift cards in the next two hours for that important client…
- If someone asks you to pay for something with digital currency, gift cards, or other non-traditional payment methods, think twice about it. Unless this is a normal thing for you, it’s probably associated with a scam.
- Make sure you use an antivirus program on your personal computer (including Macs), and keep it updated.
To Learn More
How to avoid getting hacked after data breaches: https://www.intego.com/mac-security-blog/how-to-avoid-getting-hacked-after-data-breaches/
SANS Phishing Awareness: https://www.sans.org/security-awareness-training/ouch-newsletter/2015/phishing
Applying actions and scripts to PDFs: https://helpx.adobe.com/acrobat/using/applying-actions-scripts-pdfs.html
PDF File Format: Basic Structure: https://resources.infosecinstitute.com/pdf-file-format-basic-structure/
National Institute of Standards and Technology – Blockchain Technology Overview: https://nvlpubs.nist.gov/nistpubs/ir/2018/NIST.IR.8202.pdf