With about 42% of the U.S. labor force working remotely, managing devices has become more important than ever. Luckily, Microsoft has made great advancements in device management capabilities, many of which we’ll discuss today. In this blog, we’ll go over four main areas of Endpoint Management:
- Creating an app deployment
- Securing the app (conditional access with MFA)
- App-specific protections
- Monitoring and reporting of the app
Since my blogs typically cover all things Microsoft Teams, we’ll discuss how you can use Microsoft Endpoint Manager to secure Microsoft Teams! Let’s get started!
Creating the app deployment
Let’s start things off by creating our app deployment. We can do this by going to endpoint.microsoft.com and then going to Apps. Once there, if you select All apps, you’ll notice we have a list of pre-created apps at our disposal, but in this scenario, we’ll be creating our app deployment.
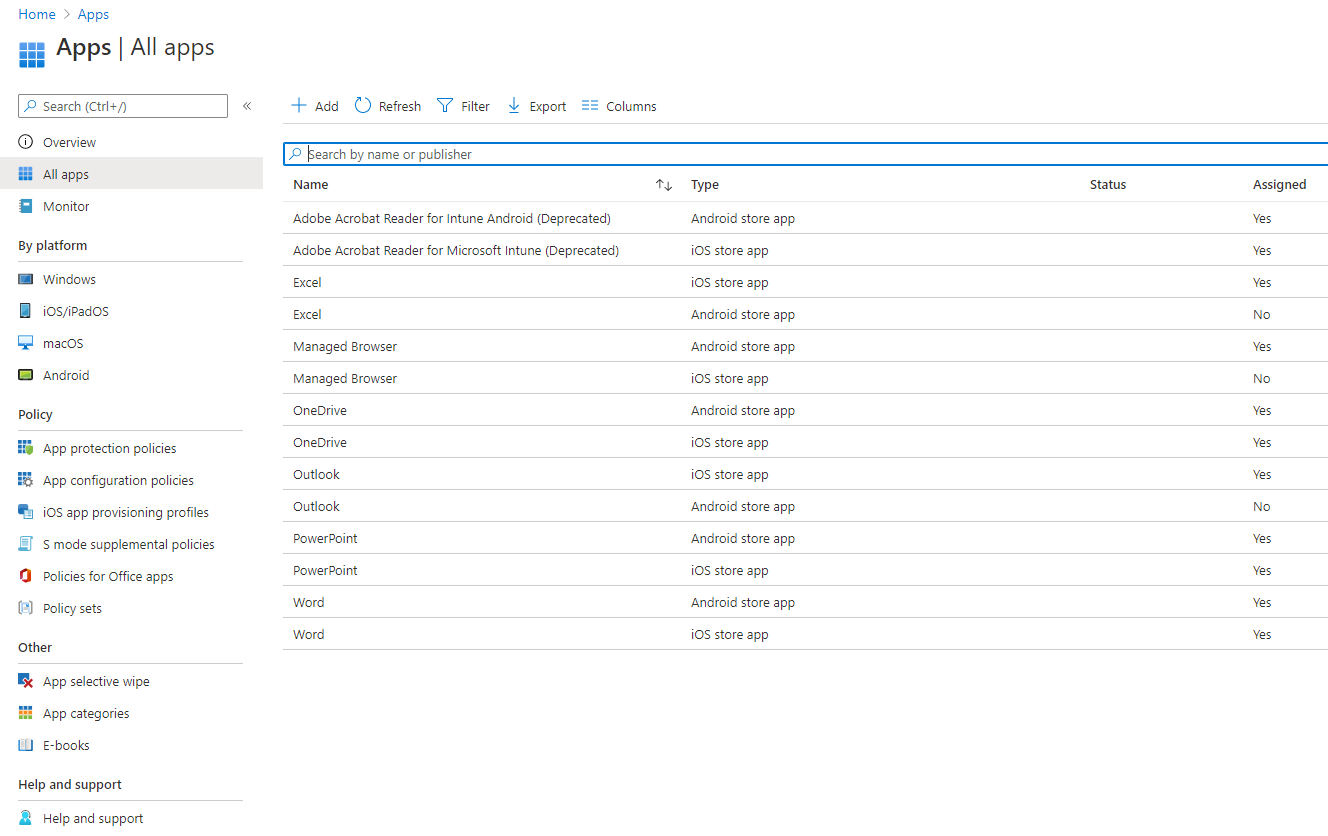
With that said, let’s select the Add option so we can create a new app policy for Microsoft Teams. After you’ve selected, Add you should see the option to select the App type. For this scenario, we’ll be creating our own built-in app.
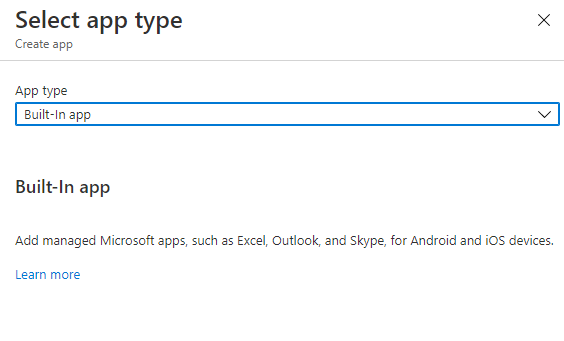
From here, we’ll select the Select App option, and then we’ll search for Microsoft Teams.
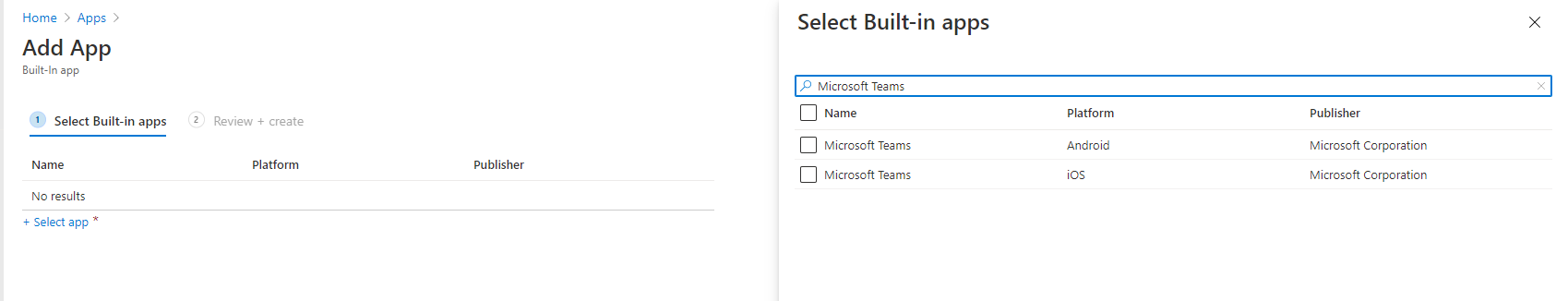
You’ll notice we have options for both Android and iOS devices, which. We’ll check both options and then press Select at the bottom. Now that we have both platforms selected, we’ll choose Next to go to the Review + Create screen, and then we’ll finalize things by choosing Create. Now that the app policy has been created, we’ll need to assign it to a group of users. We can do that by selecting the Properties, and then towards the bottom of the Properties, you should see the option to Edit the Assignments. 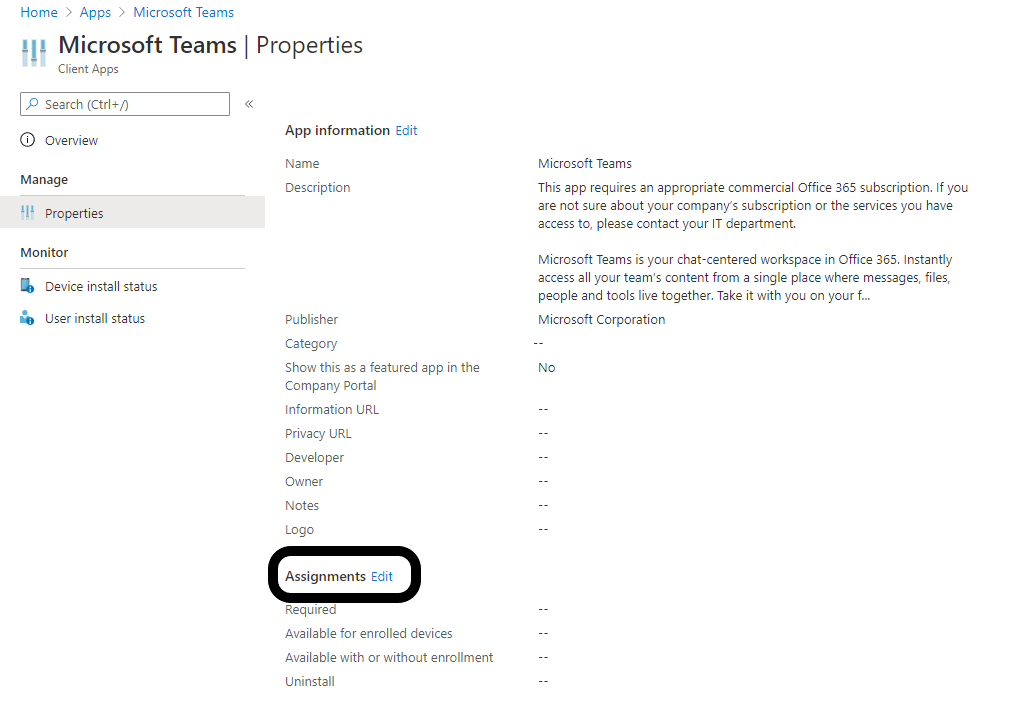
On the Edit Application page, you’ll see we have quite a few options to choose from depending on how you’d like to deploy the app. In this scenario, we’re going to make the Teams application available to all enrolled devices. However, if your organization wants to support the Teams app with or without enrollment, you will have that option as well.
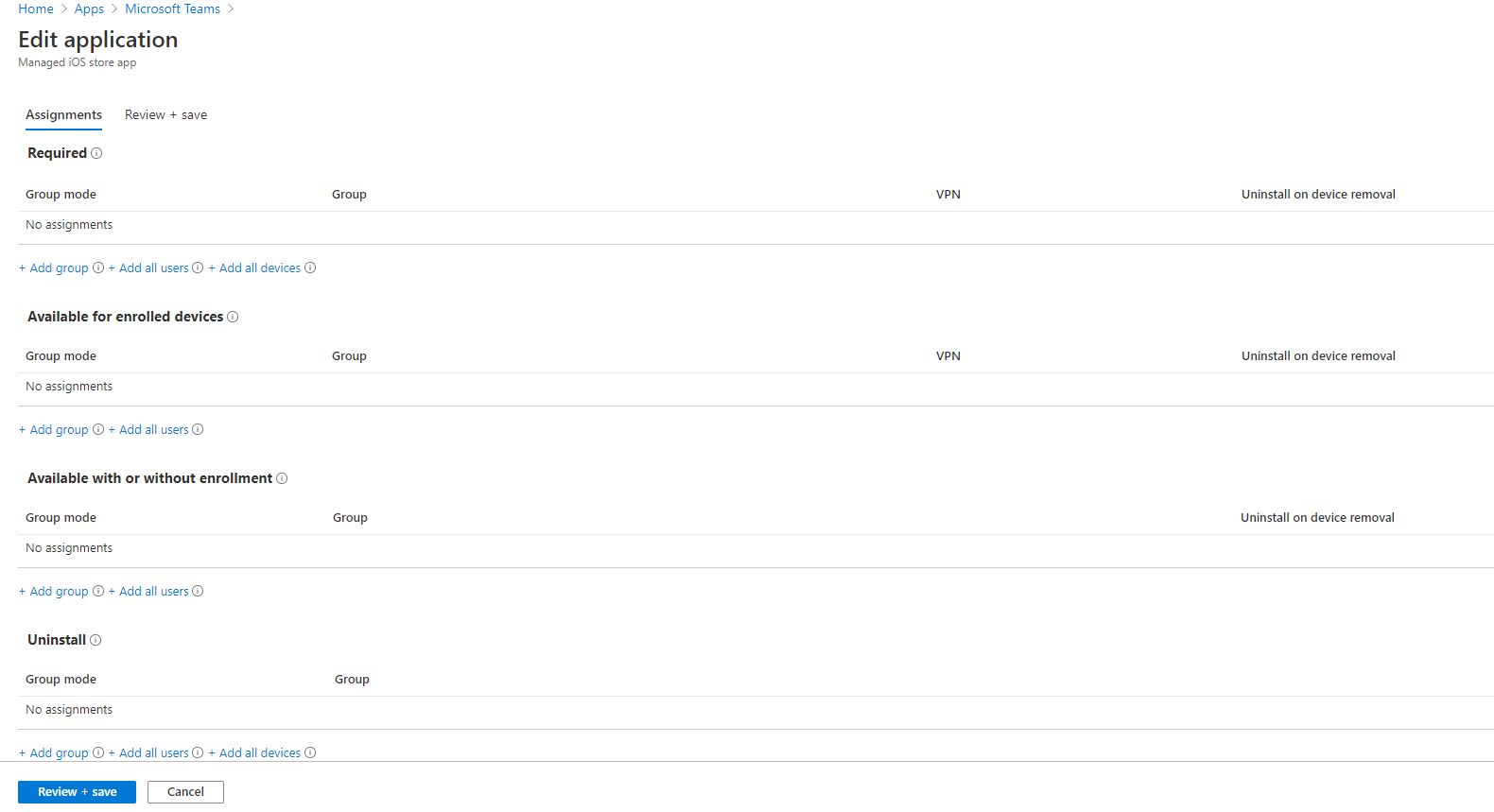
With that said, we’ll select the Add all users under our Available for enrolled devices and then select Review + save.

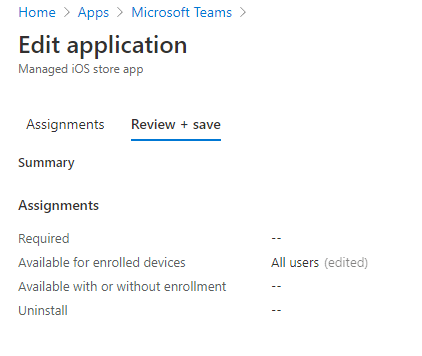
Securing the App
Now that we’ve assigned our Teams app for all enrolled devices, next up is securing the app via Conditional Access and MFA. To do this, we’ll navigate to Endpoint Security and then select the Conditional Access tab.
Let’s start by creating a new Conditional Access policy. Select New policy, and let’s name it something easily distinguishable like “Teams MFA.” Next, we’ll select Users and groups, and in this scenario, we’ll keep things pretty general and just select the org-wide option of All Users. However, if you find that you need to create a more secure or more heightened policy, you have that option. 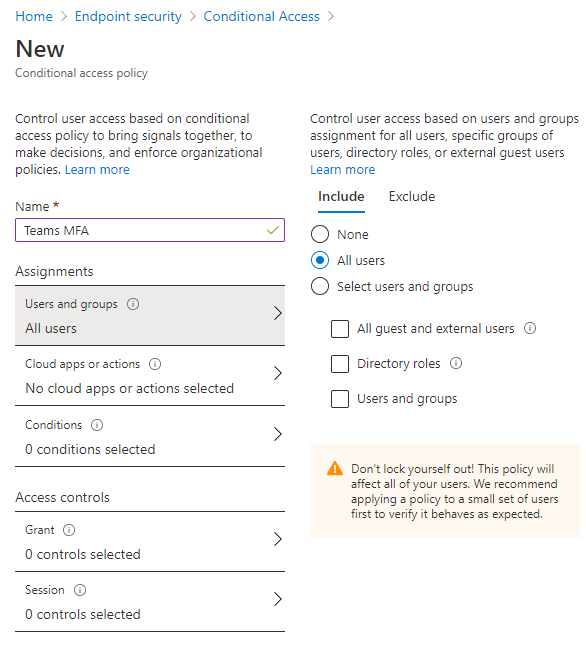
Next, we’ll go to our Cloud apps or actions and choose Select apps since we’re only applying MFA to our Teams app. Once selected, search for Teams and select Microsoft Teams.

Now we’ll jump over to the next section, Conditions, and for this condition, under Sign-in risk, we’re going to flag anyone with Medium or High risk meaning anyone with those risk levels will be prompted for MFA.
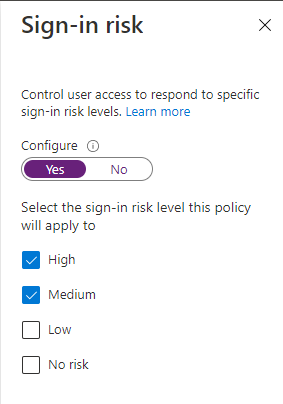
Next up is the Device platform. Here we’ll select Any device, but if your organization just wants to configure this policy to only include or exclude certain device types, you can make those changes here.
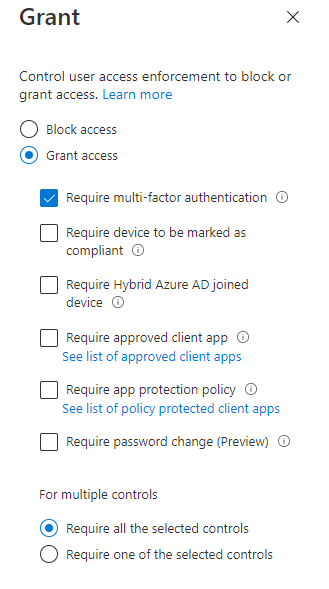
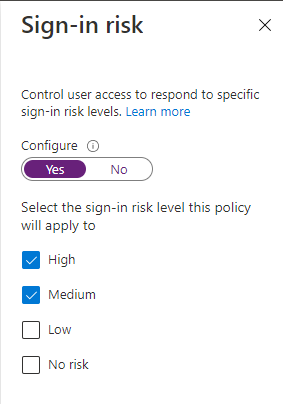 That wraps up all the things we need to do under our Conditions. Next up, we’ll tackle our Access Controls. First, select the Grant option, and in this scenario, we will grant access to the Teams app for anyone with medium or high risk as long as they pass the MFA request. So, in this case, we’ll select Require MFA and then choose Select.
That wraps up all the things we need to do under our Conditions. Next up, we’ll tackle our Access Controls. First, select the Grant option, and in this scenario, we will grant access to the Teams app for anyone with medium or high risk as long as they pass the MFA request. So, in this case, we’ll select Require MFA and then choose Select.
Lastly, we’ll select Create at the bottom of the page to officially create our policy. In this scenario, you’ll notice we are only reporting on this policy, but we haven’t officially enabled it yet. I recommend doing some testing before enabling the policy, especially since this is configured org-wide.
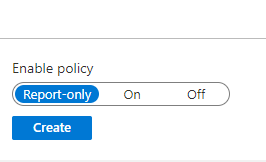
To summarize what we’ve configured, when an end-user is signing in to their Teams app from any device and deemed a medium or high risk, they will receive an additional MFA prompt. Once authenticated, they will be able to sign-in to Teams and use the app.
App-Specific Protections
Now that we’ve created our conditional access policy, we’ll want to create an app protection policy that protects the Microsoft Teams app.
You’ll see there a few canned app protection policies around data leakage for Android and iOS devices. However, in this case, we’ll create a new App Protection Policy for our iOS devices. To do that, select the Create Policy option and select iOS/iPadOS.
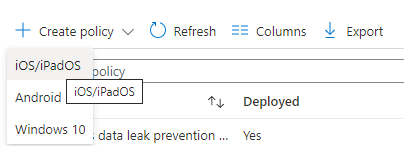
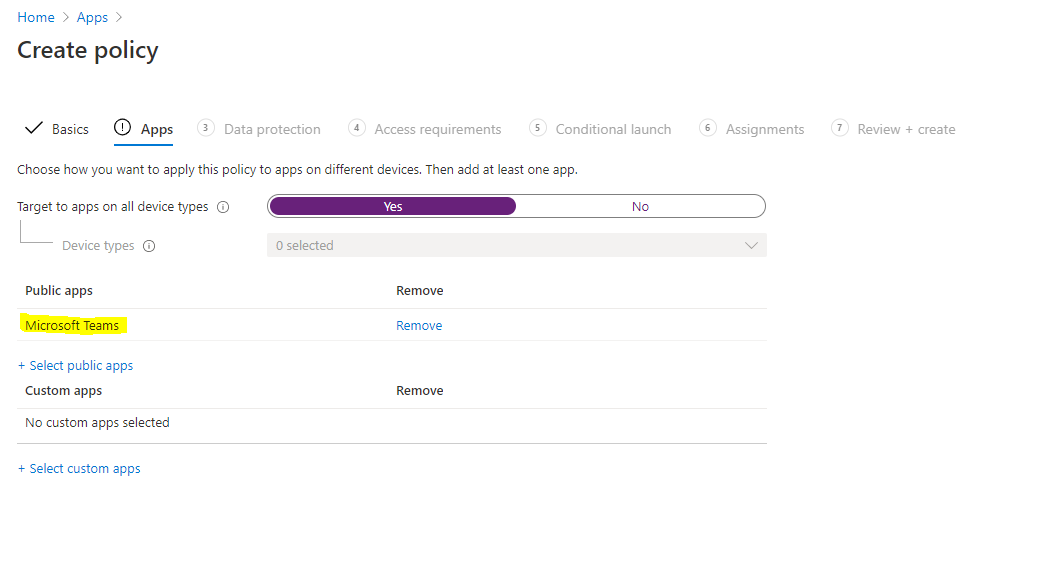
Let’s name it something easily distinguishable again, something like “Teams Data Protection.” Include a description if you’d like and then select Next. In the App section, we’ll let this apply to All device types, and then under Public Apps, we’ll choose Select public apps and then search for and select Microsoft Teams.
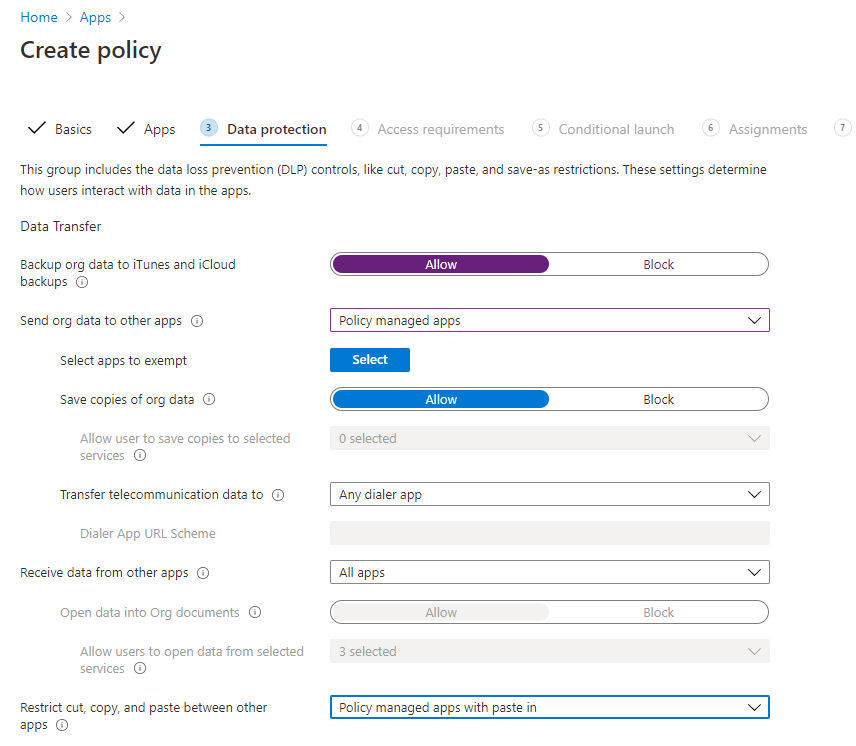
Now we’ll select Next, and so we can move on to the Data Protection step. In Data Protection, you’ll see many different options, some of which Microsoft has enabled automatically. However, feel free to enable/disable as see you fit. In this scenario, we want to restrict sending org data to only other policy managed apps. Also, we don’t want users cutting, copying, and pasting data between other apps. So we’ll restrict this to some degree by selecting Policy managed apps with paste in.
We’ll leave everything else as-is and then move on to our Access Requirements section by selecting Next. In the Access Requirements, you’ll see Microsoft has the baseline configurations already in place, but we do have the option to change settings if need be. For example, let’s say we want to change our PIN length to 8 instead of the default of 4. We can easily change that setting here. Since many of these settings are pretty standard for the organization, we’ll leave them as-is.
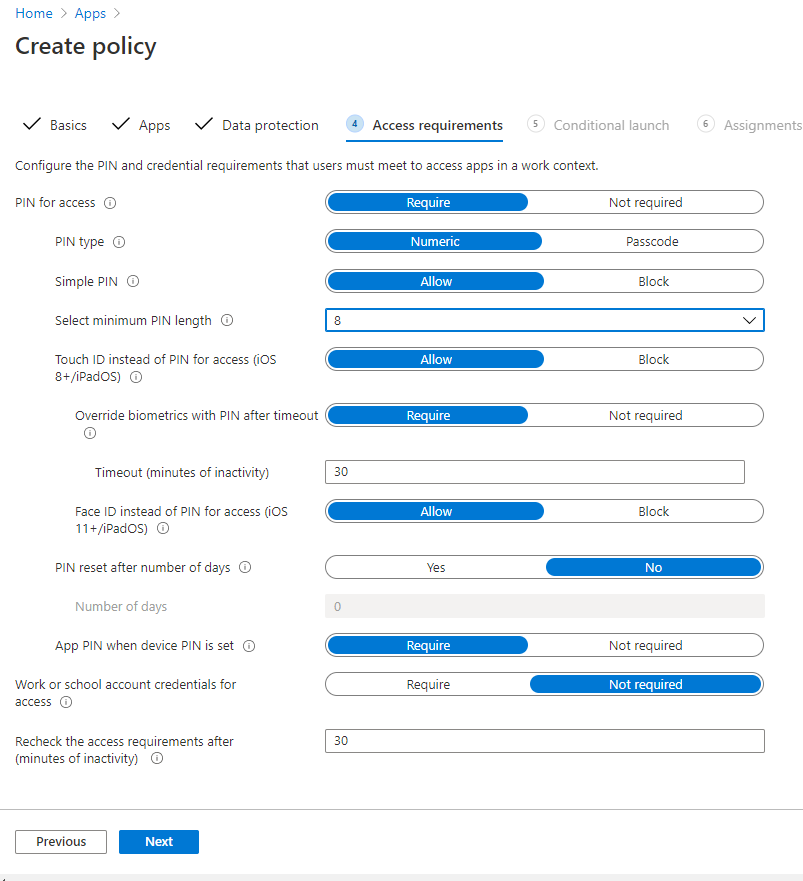
Once we’re done there, we’ll select Next to move on to our Conditional Launch settings. The Conditional Launch means that if one of the app conditions occurs, we will flag an additional review. In the example below, you’ll see we have our baseline App conditions of Max pin attempts being 5, and if they are incorrect more than 5 times, then their PIN will be reset. Also, we have offline grace period conditions that block access after 720 minutes and wipes the data after 90 days of being offline. However, we can set additional conditions like requiring a minimum app version or SDK version and even blocking or wiping access for disabled accounts. We also have some Device conditions like blocking access for jailbroken/rooted devices, requiring a minimum OS version, requiring a specific device model, or setting a maximum device threat level.
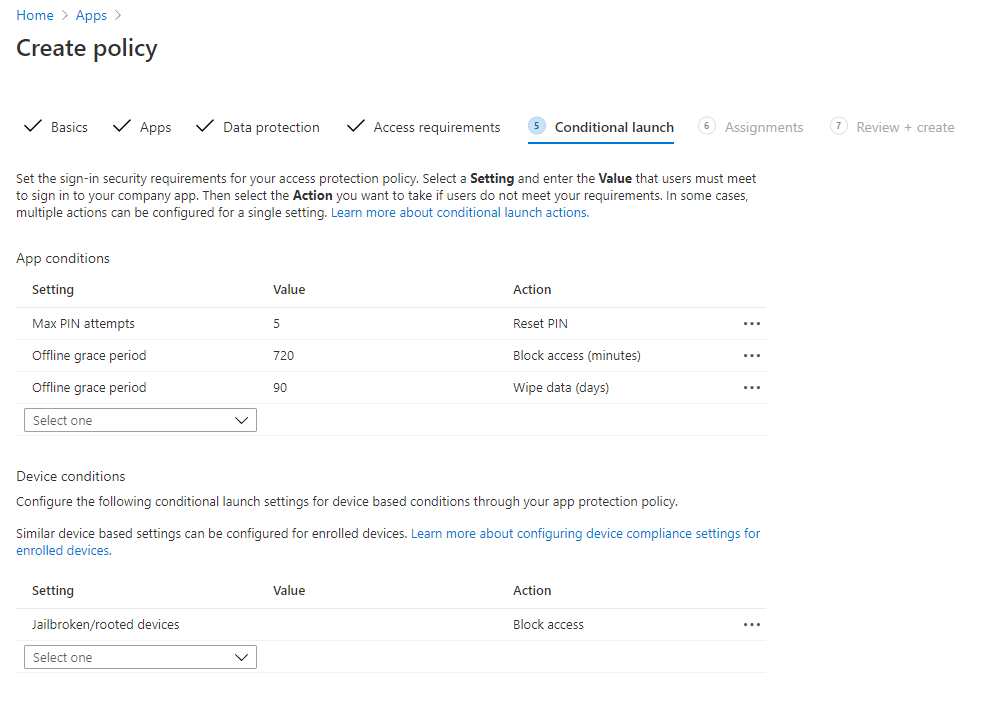
These are some great baselines, and we’re happy with these settings, so we’ll select Next. Last but not least, we’ll apply this policy to our users. For this example, we’ll select our Retail as well as our Sales and Marketing groups. We also won’t be excluding any groups from this policy assignment, so we’ll select Next.
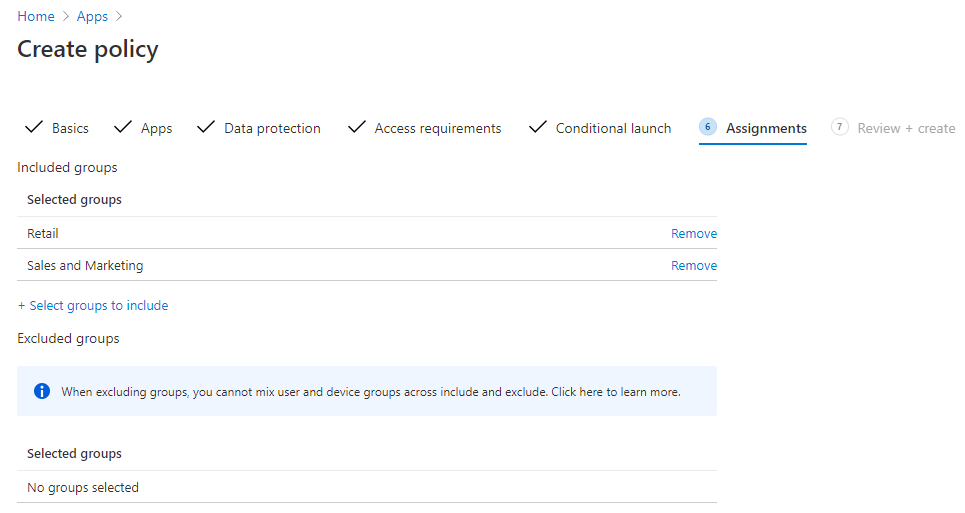
Lastly, we’ll review our changes and then select Create at the bottom once you’re ready. Great job! We’ve created our app protection policy, and we’re ready to use it!
Monitoring and Reporting
Last but certainly not least, we have the monitoring and reporting of the app. We can monitor the app by going to Apps and then selecting Monitor. In the Monitor tab, you’ll see four different options: licensing, discovered apps, app install status, and app protection status. If we want to review any user or device failure, we’ll navigate to the App install status tab, and we’ll easily be able to locate any issues presented there. If you do see errors occurring, you have the option of exporting the list for further review. Finally, we have our App protection status tab, which gives us an easy location to download our app protection reports for various scenarios and app configuration reports.
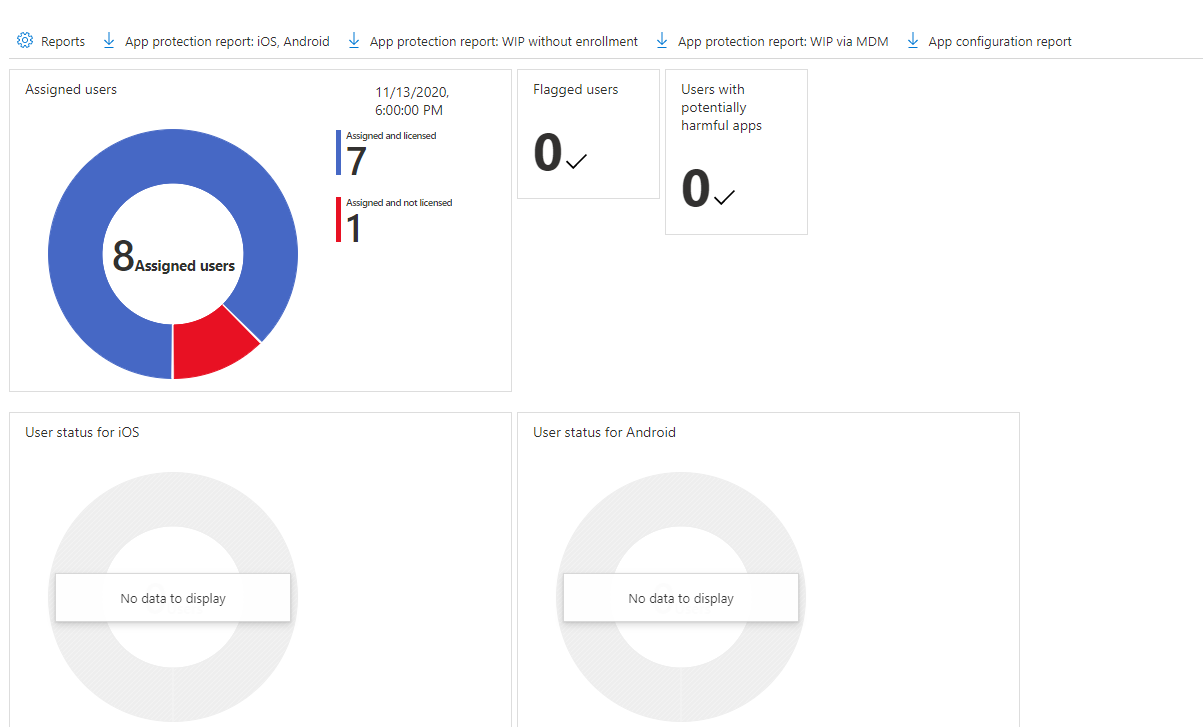
That wraps up securing our Teams app using Microsoft Endpoint Manager. I hope you have found this blog helpful, and I encourage you to check out the Endpoint Manager and start experimenting with settings so you can determine what works best for your organization!

