In my previous post on Cloud Resources – Policy and Practice, I referenced the “shared security model” adopted by all cloud providers. In this post, we will dive deeper into the differences and consequences of sharing the responsibility for securing computing resources, applications, data, and networks. Whether your organization is extending into cloud-based resources or shifting an on-premise data center, it is critical for all stakeholders to understand changes to security posture.
Failure to identify and modify corporate security policies and processes can lead to undesirable consequences such as data breaches, regulatory fines, revenue loss, and impact on corporate reputation.
Simply put, ensuring secure computing using cloud-based resources is a shared responsibility between the provider of services and the consumer of those services. The difficulty comes in identifying exactly where that line resides.
In the “old-world” of on-premise data centers, all responsibility for server security (with the possible exception of physical access) was maintained by the organization itself. This shared responsibility model changes when utilizing cloud-based resources. As noted in Figure 1, the customer (also known as “tenant”) retains all responsibility for some aspects such as security around data access, transfer, and modification. The cloud provider retains all responsibility for the physical plant, such as hardware, wiring, power, network connectivity, etc.
In between is where things become tricky.
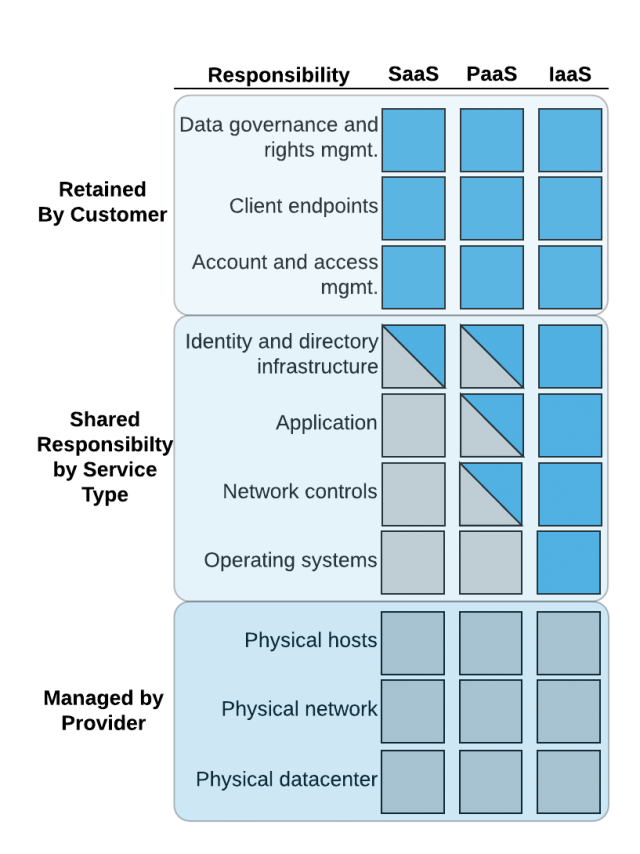
Figure 1. Cloud Resource Shared Security Model
Before we investigate what is shared, it is important to note some customer responsibilities are never shared. Responsibility for critical policy areas such as administrative privilege control, audit log maintenance, data recovery, incident response, and application security awareness are always retained by the customer. For these policies, the movement to the cloud changes the type and implementation of controls (e.g. AWS CloudWatch for audit and logs), but not their necessity.
Software-as-a-Service
It is first necessary to clarify the cloud-computing usage model. As noted in Figure 1, this depends heavily on the type of computing resources leveraged from a cloud provider. For Software-as-a-Service (SaaS), except for identity management, most security controls are shifted to the cloud provider. In this usage model, the tenant is using an application “as-is” from the provider. Examples include Salesforce, Atlassian Jira/Confluence, GitHub, Chef Automate, and many other software systems accessed by web-browser or programmatic API calls.
As an aid to development and security teams, the Center for Internet Security (CIS) has identified policies and controls required for cloud computing depending on the usage model. Based on these recommendations, the following security policy areas should be reviewed/revised when using cloud-based SaaS:
- Inventory control over software assets
- Secure configuration for mobile devices and workstations
- Secure configuration of email and web browsers
- Data protection and encryption
- Data access controls based on user permissions
- Identify management for application access and licensing
Platform-as-a-Service
As seen in Figure 1, leveraging a cloud provider’s offerings for Platform-as-a-Service (PaaS) results in a significant shift in responsibility to the service consumer. PaaS offerings vary widely between service providers and include complete architectural application hosting such as AWS Elastic Beanstalk, and full development automation support such as Azure DevOps.
In this computing model, the tenant takes on the task of application configuration, deployment, and identity permissions, in addition to all of the previously noted data integrity and access control. Depending on the degree of PaaS, the number and nature of client security policy/controls will need to be determined. Using the CIS guidelines, the following security policy areas should be reviewed/revised when using cloud-based PaaS:
- Inventory control over software assets
- Secure configuration for mobile devices and workstations
- Secure configuration of email and web browsers
- Data protection and encryption
- Data access controls based on user permissions
- Identify management for application access and licensing
- Malware and vulnerability monitoring (if server access is part of the PaaS offering)
- Secure network configuration and segmentation
Infrastructure-as-a-Service
The Infrastructure-as-a-Service (IaaS) usage model results in a further shift of responsibility to the tenant. In this case, the cloud provider is only responsible for the physical plant security and resilience. Essentially, in this computing model, the organization is leveraging the cloud provider’s flexibility in creating and removing virtual servers, network connections, and data storage. With the exception of no physical hardware, this model is the closest to a standard on-premise model.
The tenant, therefore, is fully responsible for securing the operating systems, servers, network configuration, access control, as well as all application deployment. Based on these requirements, the CIS guidelines add the following policy areas for review when using IaaS:
- Inventory control over hardware and software assets
- Secure configuration for mobile devices and workstations
- Secure configuration of email and web-browsers
- Data protection and encryption
- Data access controls based on user permissions
- Identify management for application access and licensing
- Malware and vulnerability monitoring (if server access is part of the PaaS offering)
- Secure network configuration and segmentation
- Limited access to network ports, protocols, and services
- Data recovery capabilities
- Boundary defense
- Operating system hardening
Conclusion
As discussed in this post, it can be challenging for development and security teams to understand exactly where security and compliance responsibility lies when using cloud-based computing resources. The shared security model offers some guidelines, as do on-line resources such as CIS and HiTrust, to aid identification and establishment of proper policies. At the end of the day, however, it is up to the development, security, and product management teams to ensure proper compliance and security when utilizing cloud-based computing resources.
