, stating, “You can enable federated access and controls via any SAML 2.0 compliant identity provider, such as Microsoft Active Directory Services, Okta, Ping Identity, and Shibboleth. Once this is done, agents and managers can sign in to Amazon Connect through your identity provider portal with a single click, and without a separate username and password for Amazon Connect.”
Amazon provides detailed instructions for enabling single-sign, which further link to specific identity provider instructions. Missing from this list of identity providers is Microsoft Azure Active Directory (Azure AD). This post briefly covers how to enable single-sign on to Amazon Connect with Azure AD.username and password for Amazon Connect.
Azure Active Directory and Single Sign-On
While working on our Amazon Connect Toolkit for Microsoft Dynamics 365, we started thinking about single-sign on between Azure AD and Amazon Connect.
For Amazon Connect agents working in Microsoft Dynamics 365, it would be convenient to use their Azure AD credentials for both Dynamics and Amazon Connect.
Microsoft provides detailed instructions for single-sign on to the AWS Console.
When these steps are complete, you will be able to log in to the AWS Console using Azure AD credentials by clicking on the Amazon Web Services app in your Azure Applications page:
Avoid Contact Center Outages: Plan Your Upgrade to Amazon Connect
Learn the six most common pitfalls when upgrading your contact center, and how Amazon Connect can help you avoid them.
Getting to Amazon Connect
In my testing, I found I could not access Amazon Connect from the AWS Console at this point. Navigating to my Amazon Connect instance I got a “Session Expired” notice.
To get access to Amazon Connect, I had to take two additional steps, both referenced in the Amazon Connect documentation on single-sign:
-
Grant the IAM Role permissions to my Amazon Connect instance
-
Change the Relay State URL to point to my Amazon Connect instance
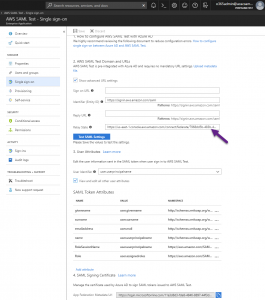
For step 2, I had to go to the Azure Portal to make the necessary changes. I went to Azure Active Directory, Enterprise Applications and selected the Amazon Web Services app I created during the single sign-on setup.
Within the Amazon Web Services app, I went to Single sign-on and clicked on Show advanced URL settings. I entered a Relay State URL with my Amazon Connect instance id as shown below:
Once I saved this change, I was able to log in to Amazon Connect from the Amazon Web Services app in Azure!
Misc. Notes
-
Within Azure AD, you can only have one Amazon Web Services app and therefore one Relay State URL; so while it would be nice to direct agents directly to the CCP by adding ?destination=%2Fconnect%2Fccp and admins to the Admin Site by having different URLs per user type, I’m not sure that’s possible with Azure AD
- If your agents are using a custom CCP, they should log in via the Amazon Web Services app in Azure first and then your custom CCP will load up just fine
Thanks for reading. Any questions, comments or corrections are greatly appreciated. To learn more about what we can do with Amazon Connect, check out Helping You Get the Most Out of Amazon Connect



Thanks for this guide; it got me working with SSO for AWS Connect. FYI I have 2 x Azure Enterprise Apps for Console access; 1 for main account, 1 for a sub account, a 3 x Azure Enterprise Apps for AWS Connect; 1 each for my 3 regions.
I did this by adding a #x (x=1,2,3 etc) onto the Identifer (Entity ID) i.e. https://signin.aws.amazon.com/saml#1
I could then create multiple Azure Apps and publish them to my users base on membership in security groups.
Hi, Can you please guide me how to use SSO for the Azure AD users to access Amazon Connect. I want AAD user to use their domain credential to access Amazon Connect, in admin, QA and agent roles.