In my previous article, I covered JSON Web Token and how to issue and validate it on data power firmware v 7.2.0.0 using custom gateway scripts. In this article, I will cover the issuance and validation of JWT with AAA action on data power firmware v 7.2.0.1.
No need to write the code. Leverage the built-in feature of AAA action to issue and validate JWT.
Here is the step-by-step guide to generate the JWT:
Step – 1: Configure the AAA action on Request rule in processing policy.
Step – 2: Select the Identification method. Mostly in case of REST services, Identification method is HTTP Authentication Header as shown in below screenshot.
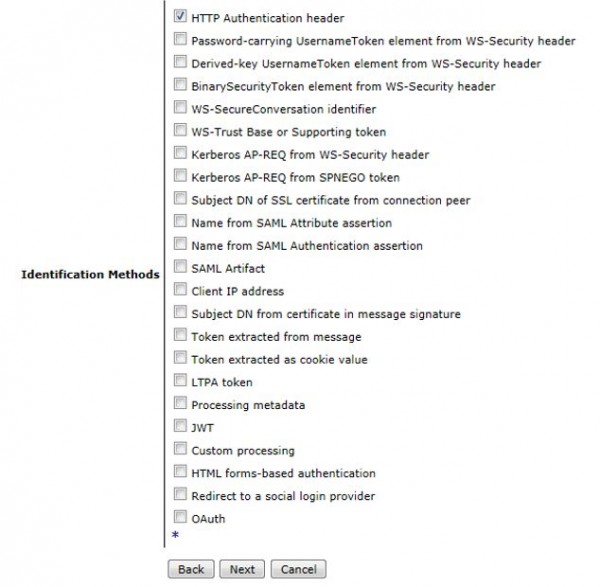
Step – 3: Authenticate the user with LDAP or locally with AAAInfo.xml file.
Step – 4: Extract the resource and authorize the user. Again, either you can make a call to LDAP, retrieve the groups associated with user and authorize or locally with AAAInfo.xml file.
Step – 5: Post successful Authentication and Authorization, its turn now to generate the JSON Web Token.
- Turn ON the Generate a JSON Web Token Property in Post processing step of AAA action as shown below.

- Create and configure a new JWT Generator.
Unlock Your Potential with Application Modernization
Application modernization is a growing area of focus for enterprises. If you’re considering this path to cloud adoption, this guide explores considerations for the best approach – cloud native or legacy migration – and more.
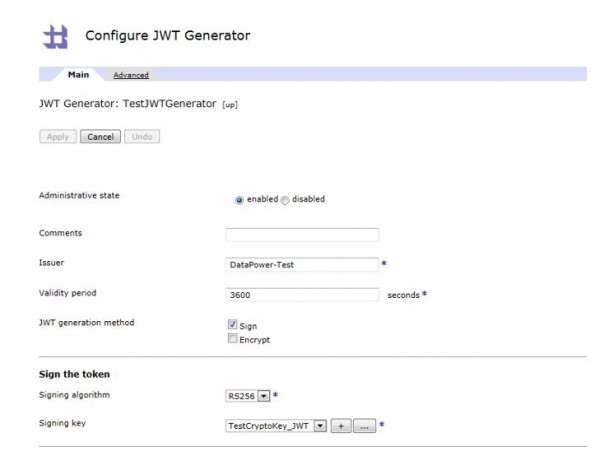
- Configure Issuer Name, Validity period as per your requirement.
- Select JWT generation method. Mostly, it’s sign.
- Once you select Sign, configure the Signature algorithm and Key.
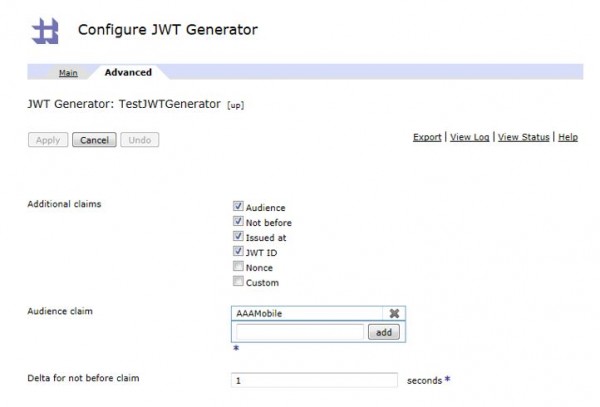
- Configure additional claims such as iat (Issued at), nbf (Not before), aud (Audience), jti (JWT ID) in Advanced tab of JWT Generator.
Step -6: Commit and apply AAA policy changes.
Here is the step by step guide to validate the JWT.
Step – 1: Configure the AAA action on Request rule in processing policy.
Step – 2: Select the Identification method as JWT as shown below.

Step -3: Create a new JWT Validator object.

Step – 4: Configure the JWT Validator object.
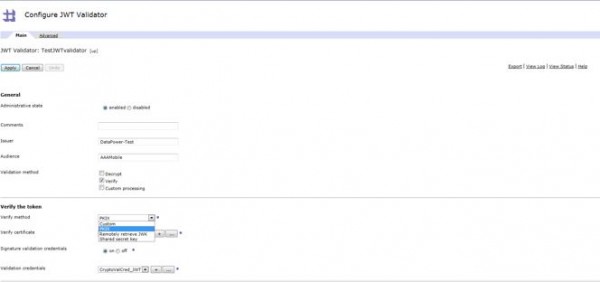
- Configure the exactly same values for Issuer and Audience fields which were used to generate the token. If there is any mis-match then validation will fail.
- Configure the Verify method. Mostly, it would be PKIX. Once you select that, configure the cert also to verify the signature.
Step – 5: In User Authentication step, select the option shown in below screenshot.
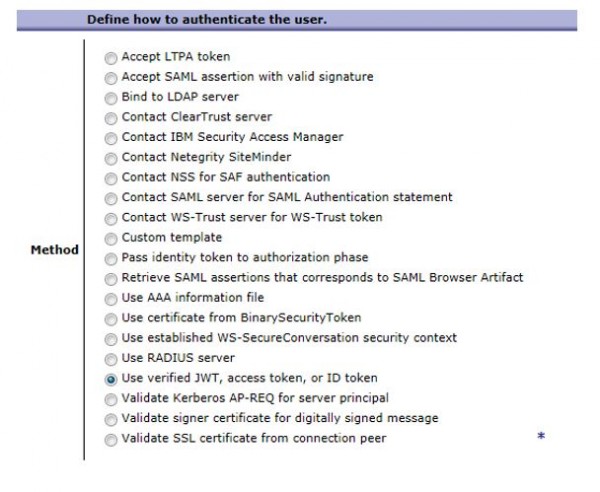
Step -6 : Commit and apply AAA policy changes.
