 Back in April 2015, Microsoft announced their new Exchange Online “Advanced Threat Protection” (ATP) feature. A month later, I saw it for the first time at the Microsoft Ignite conference and it looked like something well worth checking out later.
Back in April 2015, Microsoft announced their new Exchange Online “Advanced Threat Protection” (ATP) feature. A month later, I saw it for the first time at the Microsoft Ignite conference and it looked like something well worth checking out later.
Microsoft later made it available as a purchased add-on for existing licenses and released a few posts demonstrating the feature. I haven’t come across clients that went for the add-on option but I suspect we’ll be seeing more subscriptions with this functionality soon.
Among the many features included in the new E5 licenses is ATP. With the release of the E5 licenses last week, I took the time to check out ATP myself.
Below are some notes from that experience…
Brief Overview
Advanced Threat Protection (ATP) is really two types of protection for inbound emails. The first, “Safe Attachments”, is a deeper inspection of message attachments including sandboxing of suspicious attachments. The second, “Safe Links”, provides real-time inspection of links within an email along with reporting of what users have clicked a particular link and who bypassed the security notification (if allowed).
How To Get It
As stated above, ATP is available as an add-on to your existing licensing on a per user basis for $2.00/month or it is included as part of the new E5 licensing.
Enabling ATP
You can enable ATP in your tenant today by purchasing the add-on, adding E5 trial licenses to your current subscription or working with your account rep to get a trial setup.
When I first assigned E5 licenses in my tenant, the ATP feature remained unchecked on my E5 user (even after checking it, it would uncheck again). I was still able to create a policies and use the feature; a few days later I noticed the license was now checked, YMMV. My experience has primarily been around the “Safe Links” functionality in ATP; for some examples of the “Safe Attachments” feature, check out the “More Info” links below.
Once enabled, you’ll see an “Advanced Threats” option within the Exchange Admin Center portal, this is where you will configure the policies and can see reports. You will also see a “URL Trace” option within the “Mail Flow” tab, this option allows you to search for activity related to Safe Links.
Within your Safe Links policy, there are very few options to configure. It’s basically whether you want URLs rewritten, if you want to track user clicks, if you want to allow users to bypass the security warning and what URLs should be excluded.

User Experience – Safe Links
With “Safe Links”, URLs within an email are “rewritten” similar to how a URL shortening service works (although these URLs are far from short). The text of the URL stays the same but the HTML link behind it is changed to one prefixed with something similar to “https://na01.safelinks.protection.outlook.com/” and some parameters such as “url”, “data” and “sdata” are appended to it. When a user clicks on a rewritten link, Microsoft evaluates what is behind that link before passing the user through to the actual URL. This is meant to mitigate situations where emails are sent out containing links that are okay at the time the email is sent but redirected to malicious content some time later when the email is sitting in the user’s Inbox.
If a link is suspicious, the user is prompted with this alert:
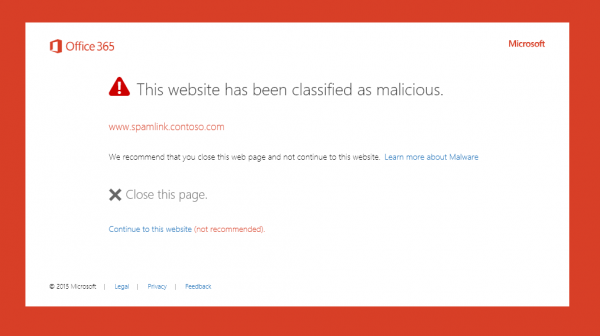
Assuming you’ve allowed users to bypass the warning, they can click “Continue to this website (not recommended)” to view the page. If you’re testing out ATP, you can use the URL “www.spamlink.contoso.com” in your testing to force this warning.
Some Nuances
There are a few things about ATP that I suppose should be expected but found interesting:
1. Since the URLs are rewritten and done so with incredibly long strings, it becomes more difficult to discern when a URL is legitimate or not. While the source URL is embedded in the string, something like a phishing attempt pointing to a slightly modified URL is not as easy to see. Now this is part of what ATP is there to protect and it’s probably only your real power users that will notice this but it is an important point to communicate to users on what ATP is and what it’s doing.
2. This may seem obvious but once a URL is rewritten, the content of the email has been changed. That means if I forward that email to someone else, they’re going to get the same ATP Safe Links behavior whether they use Office 365 or not. The rewritten URLs do not require any authentication beyond what’s embedded in the link so the recipient receiving the forwarded email will still be able to click the link. I haven’t seen it occur yet but I could imagine some non-Microsoft mail system looking at the HTML link not matching the text could possibly flag it; this will be something to watch for.
3. Likewise, if you copy and paste a URL from your email, it copies the Safe Link. I’ve already seen some Microsoft blog posts where a Microsoft employee apparently copied the Safe Link out of their mailbox and the blog now has the Safe Link instead of the intended URL. Like the situation with forwarded emails, the links still work however from a reporting standpoint, each time someone clicks on the URL, it’s recorded as if the original Safe Link recipient clicked it.
4. It looks like if a message is “Digitally Signed”, ATP does not replace links within the email. Hopefully you’re not receiving Digitally Signed phishing emails but that’s probably the next thing we’ll see if it’s not being done already.
Summary
Overall, I like the functionality provided by ATP and time will tell how successful the added protection is. The changing of content within an email has me a little concerned and it would be nice to know how long the rewritten URLs remain active for. Like most Office 365 features, I look forward to seeing how this one evolves and develops.
More Info
• Exchange Online Advanced Threat Protection Service Description
• Advanced Threat Protection in Exchange: New Tools to Stop Unknown Attacks
Did you find this article helpful?
Leave a comment below or follow me on Twitter (@JoePalarchio) for additional posts and information on Office 365.
Looking to do some more reading on Office 365?
Catch up on my past articles here: Joe Palarchio.

Hello Joe, just reading this article and as someone who has been using ATP for a few months now, it has been interesting.
The biggest things for me are:
1: The delay added to each and every attachment while it goes through detonation. I find between a 5′ and 20′ delay on my mail now. Is this something I accept as a professional? Yes. Is this something, my users will accept? No.
2; the ability to quickly know if ATP actually protected me. Yes, i know that the Message Trace will indicate it, but it would be nice to see something when it is delivered to my Junk Mail folder or personal Quarantine.
Thanks for sharing your experience – David
Is there a way to test the non save links? I tried to sent the http://www.spamlink.contoso.com link used in the demo’s but that is not firing of ATP.
Jan Groenen-
That URL will only get flagged if it’s been processed by ATP. You’ll want to send an email to an ATP-enabled mailbox with that URL. If you see that the URL has been rewritten, it should show malicious when you click on it.
Thanks
Joe
I came to this thread because my colleague sent me some links from her website. She uses Outlook: I’m on a Mac. I got a four-line link with that red malicious box. She thinks it’s because I have a Mac; I gather it’s more likely that she’s got a threat protection setting that makes it impossible for me to use her link.
How can either a) I read links from her, or b) she send links that aren’t impenetrably ‘protecteed’?
So I had a forum validation link re-written in a way that makes it useless. Not only that, but it took two days before I got the email, and only after Microsoft put it in spam quarantine. This is some broken behavior. But the spam quarantine and delay issue aside, how can I retrieve the original link text? From what I read, I should “see” the original link, and only the code under the link is altered… But in this case, I see the altered link and only the altered link in outlook. I can tease out some of the details of the original link, but not with enough clarity to make the link work. How do we decode the encapsulated link, or otherwise retrieve a copy of the original link?
I don’t get a lot of email links I care about, but validation email are critical and urgent, and for vendor relations the validation must be with my official corporate email address, not a free account on Gmail.
This is a horribly broken system to not include user access to the unadulterated link.